ZyXEL Pushes Fixing Patch for 0-Day that is Under Active Exploitation
- Many of ZyXEL’s NAS devices are vulnerable to a newly discovered zero-day flaw that is under exploitation.
- The exploit code is available for sale on the dark web by hackers who specialize in this field.
- The company has pushed a fixing patch for four devices, but the rest is no longer supported.
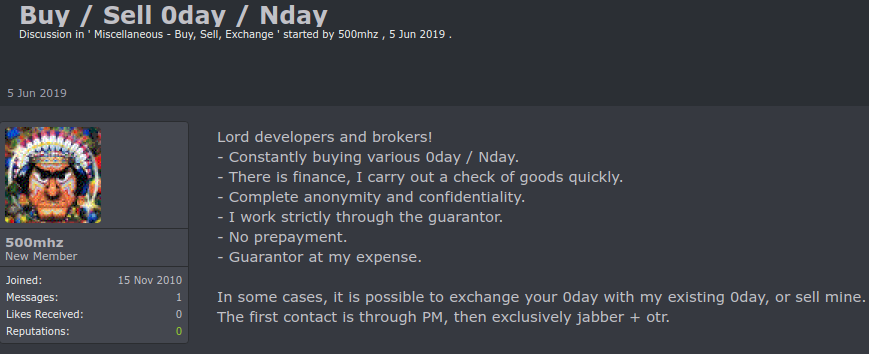
ZyXEL has just released a patch for its Network Attached Storage (NAS) devices, which plugs a zero-day vulnerability that is under active exploitation. The newly-discovered flaw (CVE-2020-9054) affects a dozen of ZyXEL NAS products, enabling actors to launch remote code execution attacks and take full control of them. The attacks require no user interaction, while the exploit code was offered for sale on darknet forums by someone going by the nickname “500mhz”. Zero-days are vulnerabilities that have been discovered by hackers but remain unknown for the vendors, and thus they may go undetected and unpatched for extended periods of time. This is why they sell for very high prices on the dark web. This particular 0-day with detailed instructions on how to use it had a price tag of $20000.
Unfortunately for both the hardware vendors and the users of these devices, there is a whole industry set up around the discovery and selling of zero-days. Oftentimes, crooks can make a lot more money by joining the dark side than reporting it to companies and receiving a bug bounty. The profile of “500mhz” on Russian forums, for example, makes it clear that the person is devoted to buying, selling and exchanging zero-day exploits, exactly as if they are a tradable commodity.
Source: KrebsOnSecurity
The first time that ZyXEL got to know about the exploit was on February 12, 2020, after a tip by “KrebsOnSecurity”. After four days of not hearing back from the Taiwanese network hardware maker, the researcher notified the U.S. DHS (Department of Homeland Security), as ZyXEL products are used virtually everywhere in the country. This has finally brought the matter into ZyXEL’s attention on February 17, and yesterday, they released a fixing patch along with a security advisory. Having investigated the issue, the company reached to the conclusion that all of the NAS products that run firmware version 5.21 and earlier are vulnerable to the particular 0-day.
The devices that should be upgraded to the latest firmware version available right now are the NAS326, NAS520, NAS540, and NAS540. However, there is also a set of affected devices that are no longer supported by ZyXEL, and which won’t get a fix. These are NSA210, NSA220, NSA220+, NSA221, NSA310, NSA310S, NSA320, NSA320S, NSA325 and NSA325v2. If you own one of these, you should take them offline, or connect them to a security router or firewall. If possible, upgrade to a newer product that is actively supported by its vendor, receiving regular security updates and patches.