Zoom Could Leak Your Windows Login Credentials to Hackers
- Zoom could allow an attacker to capture the hashed Windows login credentials and then dehash them.
- The attack takes place on the app's chat and stems from the improper handling of shared URLs.
- There's a manual fix for this bug, while Zoom has not acknowledged the problem yet.
The more popular the Zoom video-conference app is getting during the pandemic, the more attention it's receiving from security researchers. The software was forced to mature quickly so it could accommodate the needs of a rapidly growing audience. Still, things in software development aren't easy or straightforward when scaling up at this rate. The latest discovery comes from a hacker who uses the @_g0dmode Twitter handle, who figured that the Windows client of Zoom is vulnerable to UNC path injection in the chat feature of the app. The problem lies in how Zoom automatically converts Windows networking UNC (Universal Naming Convention) paths into clickable links.
A UNC path can be used to access network resources such as files hosted on servers. When a user clicks on a UNC path hoping to obtain access to a file that was shared by another user on the Zoom chat, Windows activates the SMB (Server Message Block) file-sharing protocol. It results in sending the user's Windows login credentials with their NTLM hash, which a hacker could easily capture and potentially dehash. An offense security solutions firm has already tested the theory in practice and was able to expose the user's credentials.
Hi @zoom_us & @NCSC - here is an example of exploiting the Zoom Windows client using UNC path injection to expose credentials for use in SMBRelay attacks. The screen shot below shows an example UNC path link and the credentials being exposed (redacted). pic.twitter.com/gjWXas7TMO
— hackerfantastic.x (@hackerfantastic) March 31, 2020
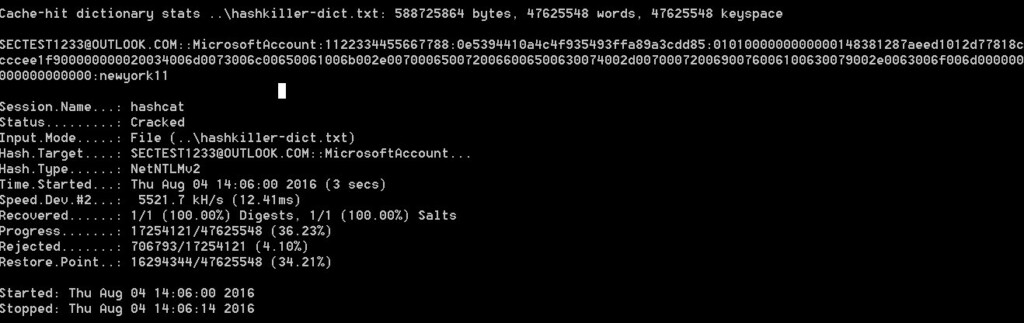
The researchers said that free dehashing tools like Hashcat, along with the computing resources that are available to anyone today, could make dehashing these passwords a matter of a few seconds.
Source: Bleeping Computer
And to make things even more dangerous for Zoom users on Windows, the UNC path can also be used for sharing executables. It means that launching programs this way would also be possible, although Windows would at least display a dialog for the user to accept first. This action at least prevents the UNC paths from firing up programs silently in the background.
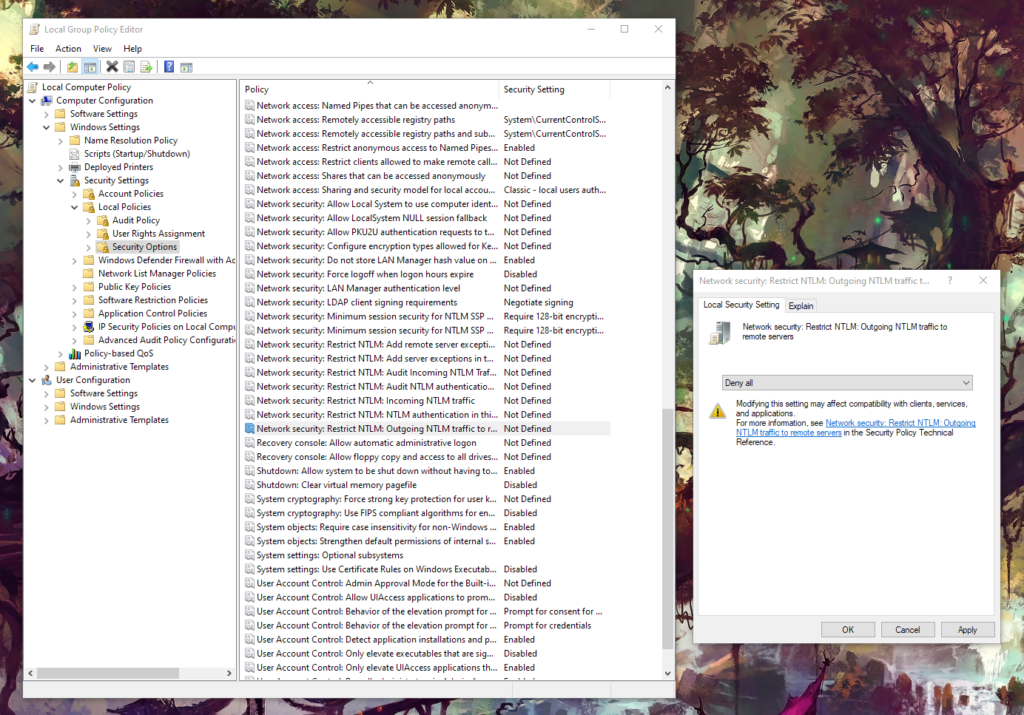
Zoom is already dealing with a lot of trouble right now, so we're not sure about when they're planning to fix this flaw. Those of you who want to take the matter into their own hands, open the "Edit Group Policy" tool on the Windows Control Panel and follow the same path that is shown in the above image to locate the "Restrict NTLM: Outgoing NTLM traffic to remote servers" entry. Open it and set it to "Deny All," which should prevent the leaking of the Windows credentials when clicking UNC paths on Zoom without requiring a system reboot.