Zero-Day in Netgear Router Products Affecting 79 Models
- 79 Netgear router models are vulnerable to a pretty simple and versatile exploitation method.
- Even after three months, the vendor hasn’t fixed the zero-day since its reporting by two independent researchers.
- Exploiting the flaw would be as easy as leading the target to a particular website with a specially crafted HTML page.
Researchers Adam Nichols (Grimm) and “d4rkn3ss” (VNPT ISC) have discovered a zero-day flaw in the HTTPD daemon used to manage Netgear routers, potentially enabling an attacker to take full control over the device by launching a remote attack. The zero-day flaw affects a total of 79 Netgear router models, and as there’s already a proof of concept (PoC) out there, replacing your router with a new and supported model should be a priority right now. Unfortunately, Netgear hasn’t clarified if they’re planning to push a firmware update that addresses the problem, so waiting for the vendor to do something wouldn’t be the ideal way to go.
The router models that are affected are the following:
AC1450 MBR1516 WGR614v9 D6220 MBRN3000 WGR614v10
D6300 MVBR1210C WGT624v4 D6400 R4500 WN2500RP
D7000v2 R6200 WN2500RPv2 D8500 R6200v2 WN3000RP
DC112A R6250 WN3100RP DGN2200 R6300 WN3500RP
DGN2200v4 R6300v2 WNCE3001 DGN2200M R6400 WNDR3300
DGND3700 R6400v2 WNDR3300v2 EX3700 R6700 WNDR3400
EX3800 R6700v3 WNDR3400v2 EX3920 R6900 WNDR3400v3
EX6000 R6900P WNDR3700v3 EX6100 R7000 WNDR4000
EX6120 R7000P WNDR4500 EX6130 R7100LG WNDR4500v2
EX6150 R7300 WNR834Bv2 EX6200 R7850 WNR1000v3
EX6920 R7900 WNR2000v2 EX7000 R8000 WNR3500
LG2200D R8300 WNR3500v2 MBM621 R8500 WNR3500L
MBR624GU RS400 WNR3500Lv2 MBR1200 WGR614v8 XR300 MBR1515
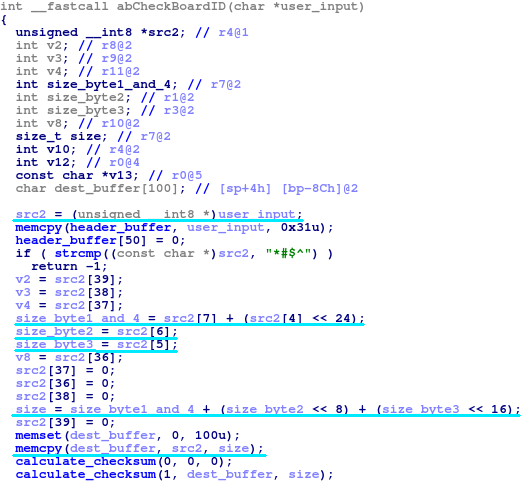
The problem lies in the inadequate checks of the length of data inputted by the user onto the HTTPD daemon, which can practically lead to a buffer overflow condition. Thus, an attacker could create a specially crafted string that would exploit this flaw, executing commands on the router remotely and without the need to authenticate. This is a much-deprecated method of exploitation that was later addressed by the use of stack cookies, but the 79 models presented above are unfortunately not supporting stack cookies.
Source: blog.grimm-co.com
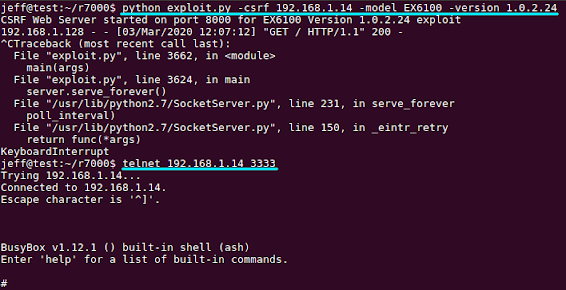
As the researcher mentions, a user with a vulnerable Netgear router could just browse a website that would serve a malicious HTML page, sending an AJAX request containing the exploit. If the attacker knows the model and version they’re targeting (via detection), they could serve a CSRF (cross-site request forgery) attack before the token is checked. That said, casually browsing the web with one of the vulnerable Netgear models could result in getting hacked.
Source: blog.grimm-co.com
The reporting researcher comments about network device security and how this finding highlights a terribly low level of code quality, failing to address or cover even basic requirements in today’s world. These vulnerabilities have been around for many years now, so the users of the devices were exposed to potential exploitation for a very long time.
The Zero Day Initiative claims to have disclosed this flaw to Netgear on January 8, 2020, and both researchers agreed to make it public this month. Netgear failed to address the problem and asked for more time to resolve the bug. Still, researchers rejected this request, as the security of a large number of people was already at risk for an extended period.
UPDATE: Netgear reached out to inform us of the release of a relevant security advisory. Firmware updates, mitigations and workarounds are included, so all practical scenarios are covered. Also, the vendor has released hotfixes for R7850, R8500, and WNR3500Lv2.