Zeoticus 2.0 Is a Ransomware That Doesn’t Need a C2 Server
- Zeoticus introduced version 2.0, and it comes with better performance and more offline capabilities.
- The particular ransomware tool uses powerful encryption on a lean shell but doesn’t offer many amenities yet.
- Thus, it’s not the most popular ransomware choice for crooks right now, but this could change soon.
Command and control (C2) infrastructure is typically useful to malware actors for maintaining communications with the compromised systems, dropping more payloads or additional modules, exfiltrating data, executing commands remotely, and for gathering reconnaissance information before the main attack is launched. According to a new report by Sentinel Labs, not every threat actor needs a C2 server to have a functional operation, and the latest example of that is the Zeoticus 2.0 ransomware.
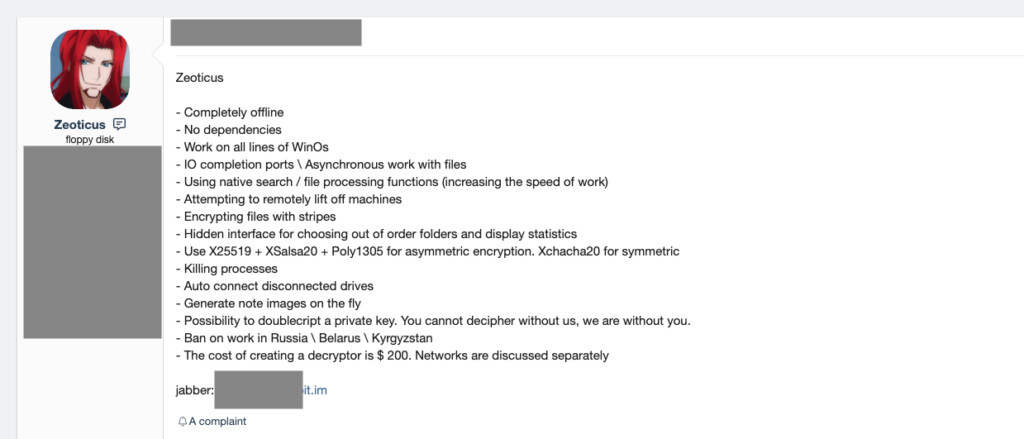
Zeoticus first appeared in the wild in December 2020 as an underground ransomware platform sold in various dark web markets and forums. It is thought to be authored by Russian hackers, as it is designed to exclude victims that appear to be based in the regions of Russia, Belarus, and Kyrgyzstan.
Besides that, it is advertised as a “completely offline,” “no dependencies,” lean and powerful ransomware that uses X25519 + XSalsa20 + Poly1305 asymmetric and Xchacha20 symmetric encryption schemes. It can generate note images on the fly, “doublecript” private keys, and automatically connect and encrypt disconnected drives.
Zeoticus also kills many running processes on the system to make the execution and encryption faster, allowing the victim little time to respond to what’s happening.
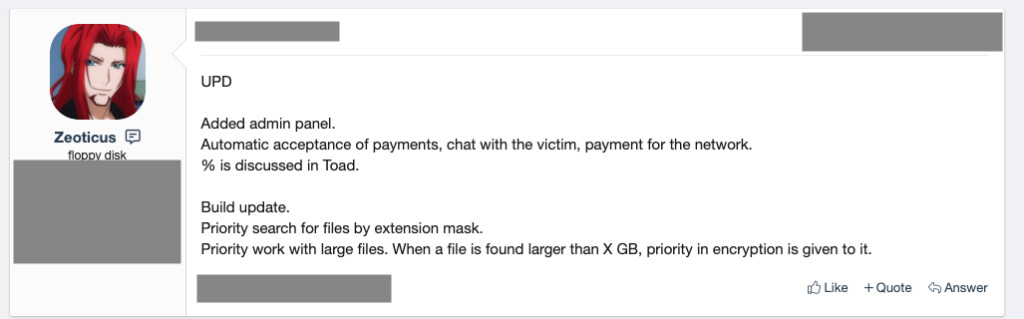
The authors continue to work on the ransomware strain, making it leaner and speedier, focusing more on the malware's performance side and its functionality. However, there’s some work on the usability side, too, as the developer has also added an admin panel, automatic acceptance of payments, live chat with the victim, etc.
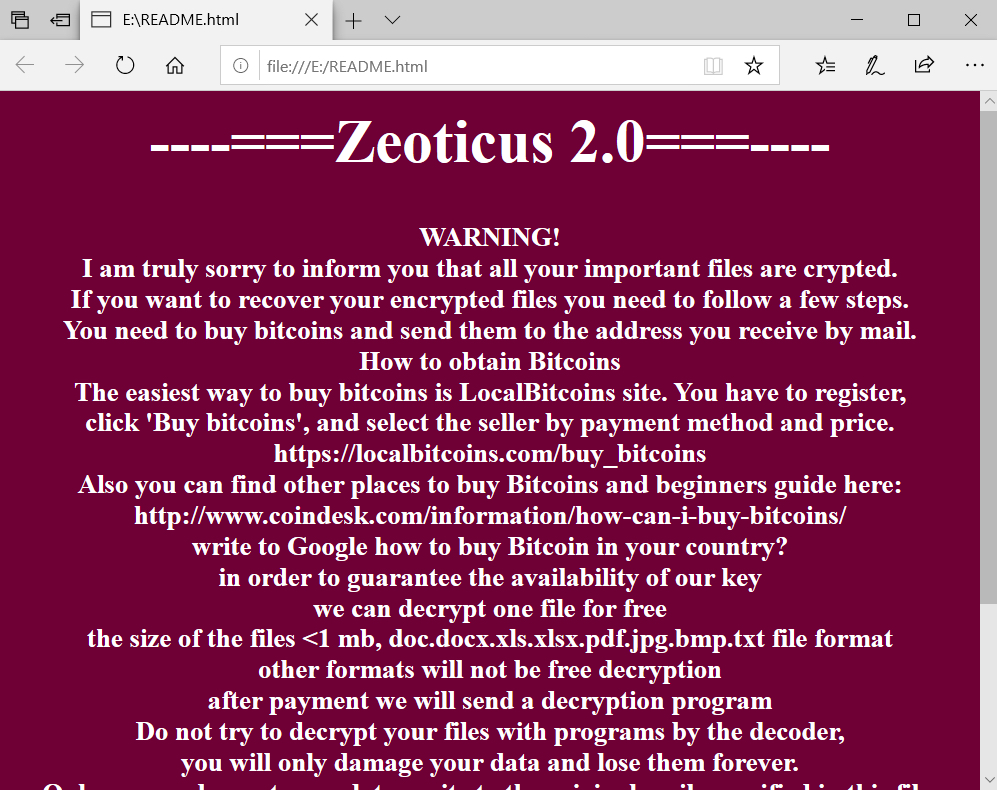
While some effort to introduce “quality of life” features has been made, there’s no dedicated portal for victims. Hence, those infected have to contact the actors via email to arrange the payment and reception of the key.
The particular ransomware isn’t very popular in the underground community yet, but considering the development love it’s getting, this may change soon. For now, there’s no working decrypter for Zeoticus, so prevention is the only way to protect your stuff from it.
Also, keeping regular backups would be a good idea in general. Remember, this ransomware can hit Windows versions as old as XP, so there’s no hiding from it through obscurity.