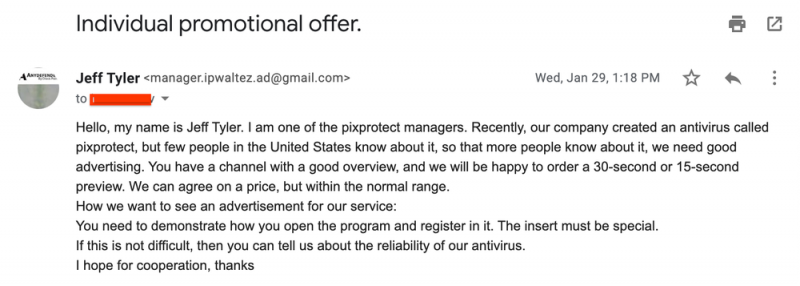
YouTube Creators Targeted With Phishing Scams Based on Cookie Theft Malware
- Google discoverd a new Cookie Theft-based phishing scam that targeted channels belonging to YouTube creators.
- Actors were sending phishing emails and hijacking channels for selling them or for running crypto investment scams after rebranding.
- As a result, the tech giant has augmented its regulations on YouTube, Safe Browsing, and Account Safety.
Google’s Threat Analysis Group (TAG) identified a new phishing campaign targeting YouTubers with Cookie Theft malware, aiming to earn money through selling the stolen data and sometimes through cryptocurrency scams. Google says it started disrupting financially motivated phishing scams using this type of malware in early 2019.
As per the research details posted by TAG, Google attributed this campaign to a group that was recruited on Russian-speaking forums. The actors lured victims with fake opportunities such as collaboration contracts for anti-virus software, VPN, music players, photo editing, or online games. If the victim took the bait, the actors took control of the channel and either sold it for maximum profit to the highest bidder or used it for crypto scams.
These fake deals are usually mimic legit companies and their email templates, prompting victims to click a software download URL containing malware. Scammers would also use PDFs via Google Drive and even Google Docs. The most popular bait included prominent brands like Luminar, Cisco VPN, games on Steam, etc. In some instances, the hackers would create fake social media pages containing URLs leading to cookie theft malware download. Since Gmail is pretty prompt to spot scam-like activity, most of these scammers would divert victims to WhatsApp, Telegram, or Discord.
After the victims downloaded the app and launched its installer, it would launch a cookie-stealing malware. Some very common malicious apps as found on GitHub are RedLine, Vidar, Predator The Thief, Nexus stealer, Azorult, Raccoon, Grapnd Stealer, Vikro Stealer, Masad (Google’s naming), and Kantal (Google’s naming). Out of these some of the software would use anti-sandboxing techniques, including enlarged files, encrypted archive, and download IP cloaking.
The malicious script would collect cookie-related data and sometimes user passwords as well from the user’s device and send these to the scammer. Mostly these scripts get promptly deleted to minimize detection and response but they can be kept for future data theft as well. Once all the data was transferred, they would gain access to the YouTuber’s channel and then either control it discreetly or outright lock the owners out to use it as they saw fit.
Aside from selling such stolen accounts, hackers also used these YouTube channels for cryptocurrency scam live streaming. These live stream sessions would present the channel as belonging to large crypto companies by repurposing name, profile, and other channel details and draw in investors with lucrative returns. Hijacked channels ranged from $3 to $4,000 depending on the number of subscribers on account-trading markets.
Google’s Threat Analysis Group tracks actors involved in financially motivated abuse, disinformation campaigns, and even government-backed hacking. The tech giant says its entire suite of cybersecurity brands reduced the number of phishing emails by 99.6% as per the latest audits in May 2021.
In addition to informing users of these thefts, Google has announced additional heuristic rules on all types of phishing emails, cookie-based hijacking, and crypto-scam live streams. Similarly, it has increased its oversight of YouTube, Account Safety as well as Safe Browsing.
To bolster knowledge and protection against such scams, Google has issued recommendations to all its clients: take Safe Browsing warnings seriously, perform virus scanning before running software, enable the “Enhanced Safe Browsing Protection” mode in Chrome, be aware of encrypted archives, and use multi-factor authentification.