Open-Source XenoRAT Variant Distributed by North Korean Threat Actors
- A XenoRAT-based malware was seen developed and deployed in cybercriminal operations.
- The individuals behind it are believed to be part of a state-sponsored North Korean cluster of threat actors.
- The RAT is a sophisticated malware strain with advanced capabilities that can be used for cyberespionage.
XenoRAT, a variant of the open-source remote access trojan (RAT), is actively developed by a nexus of threat actors tracked as UAT-5394, which Cisco Talos security experts believe to be a state-sponsored North Korean group. They named the malware “MoonPeak.”
The MoonPeak malware samples show that XenoRAT evolved after it was forked by the threat actors. It has capabilities such as obfuscation, persistence, monitoring, evading detection, and can even uninstall itself.
This cluster of activity has some overlaps in tactics, techniques, procedures (TTPs), and infrastructure patterns with the North Korean state-sponsored group Kimsuky, which evolved rapidly throughout 2024.
Security experts believe UAT-5394 may actually be Kimsuky (or a sub-group) using MoonPeak instead of their old QuasarRAT implants or another North Korean APT that borrowed Kimsuky’s TTPs and infrastructure patterns.
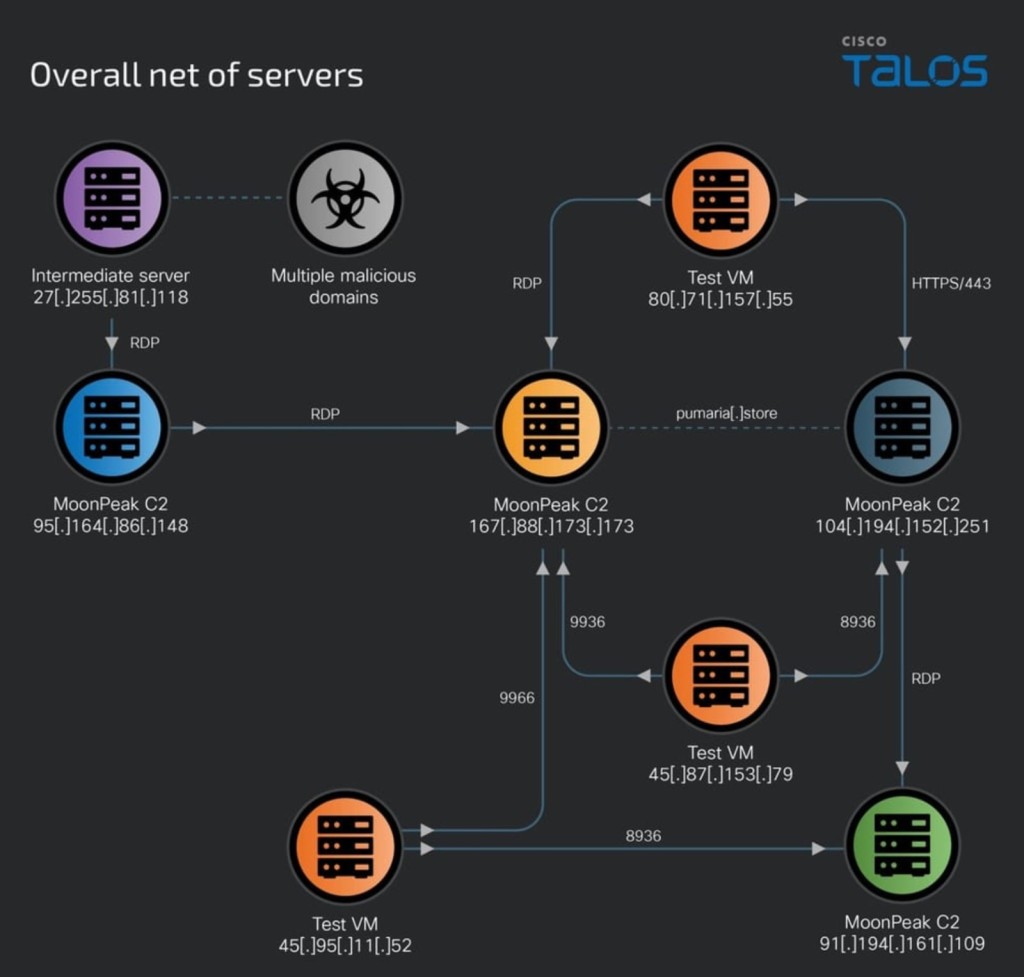
The analysis indicates that the threat actors set up a new infrastructure and modified existing servers, employing both command and control (C2) servers and staging servers while using virtual machines to test their implants.
Researchers discovered several instances of two virtual machines hosted on public IPs that reached out to various MoonPeak C2 servers over ports configured in the malware.
In several cases, the hackers accessed existing servers to update their payloads and retrieve logs and information MoonPeak collected. The threat actors also used VPN nodes to access their infrastructure.
An early variant of XenoRAT was recently seen in a spear-phishing campaign by AhnLab in June, which shows the open-source RAT family is still relevant to the hacking gangs out there. After this report, UAT-5394 hosted their malicious payloads on attacker-controlled systems and servers instead of using legitimate cloud storage providers.