Rising Malware Campaign, WP-VCD, Plaguing Pirated WordPress Plugins & Themes Again
- A long-standing WordPress malware campaign is now on the rise again.
- The malicious software is spread through malvertising and pirated WP themes.
- The malware can move laterally, change C2 addresses, and delete itself.
Wordfence warns about a rising malware infection campaign known as WP-VCD, which is currently plaguing the WordPress ecosystem. The team of researchers has been following the activity of the campaign closely, and as they point out, it shows no signs of slowing down. For this reason, WordPress website administrators need to learn more about WP-VCD, what it is, and how to protect their sites from this threat.
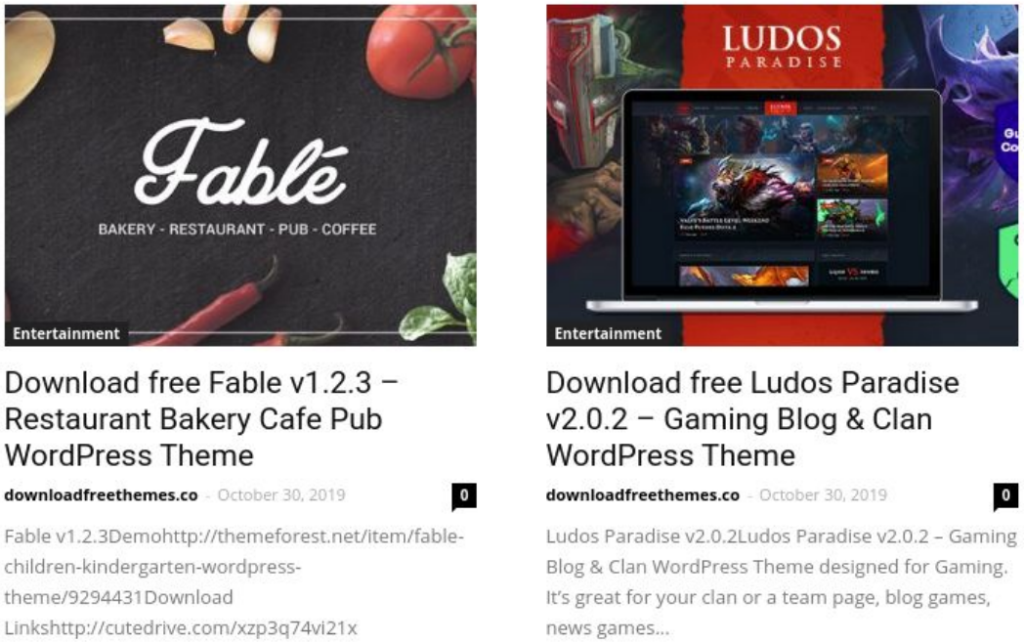
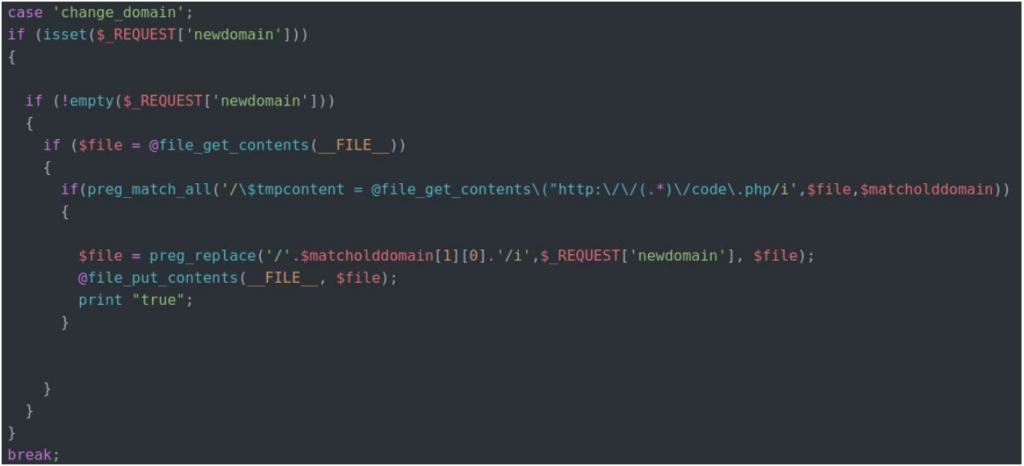
First of all, it is essential to point out that WP-VCD is hiding inside pirated WordPress plugins and themes, so most of the infections come from downloading and installing stuff you didn’t pay for. The malware connects to its dedicated C2 infrastructure, has the capacity to self-heal if needed, and features high levels of persistence. The backdoors that are injected into the theme files are Base64 encoded, while the deployer generates a unique password for it in order to prevent other malicious actors from exploiting it.
Source: Wordfence Blog
WP-VCD is also capable of lateral propagation, scanning the hosting environment and inserting the backdoor code to all WordPress themes that are found in the compromised account. Even if the backdoor is removed, it will be re-added once the site is loaded again. One of the things that the planted backdoor allows for is the creation of a rogue administrator account, which practically enables the actor to perform full website takeover.
Wordfence is trying to locate the actor behind WP-VCD, and their investigation led them to the names “Sharif Hamdy” and “Ahmed Mamdouh”. As for the registration organization, this carries the name “Autson”. As they point out, the same registrant emails and names can be associated with Joomla malware distribution campaigns from back in 2013, but the real identity of the actor cannot be determined with certainty at this point.
Source: Wordfence Blog
WP-VCD can easily change infrastructure and C2 addresses, get new commands and instructions and generally remain active in the WordPress scene for long. The simplest and most effective way to stay safe from this malware is to abstain from installing pirated plugins and themes. If a website developer is building your WordPress site, make sure that they have bought the stuff they’re using for it, or purchase the building blocks and provide them yourself. Very often, website developers grab a pirated plugin to divert some of the project money to their pocket, so you shouldn’t blindly trust anyone.
Are you using a pirated theme or plugin on your WordPress website? Share your experience in the comments down below, or on our social, on Facebook and Twitter.