WordPress Websites Exploited to Distribute the ClearFake Trojan and Infostealers
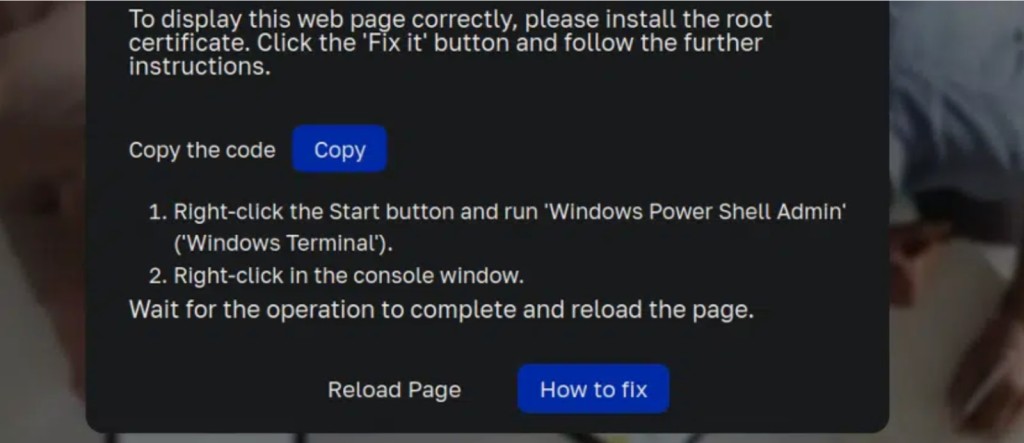
- Compromised WordPress websites were observed displaying a fake issue to lure victims into installing malware on their machines.
- The prompt urges users to install a Remote Access Trojan and details the necessary steps to do so.
- The malicious payload contains the RedLine Stealer malware, an infostealer popular among cybercriminals.
A Remote Access Trojan (RAT) linked to the malicious ClearFake campaign is pushed by hackers via compromised websites that urge users to fix a bogus issue and install the malware, Sucuri researchers say.
When visited, the compromised site displays a prompt translated into 42 languages, informing users they allegedly need to fix a loading issue by installing a “root certificate” and detailing the steps the victim would need to take.
The hackers leverage core Windows operating system libraries (user32.dll and kernel32.dll) to hide the PowerShell window from sight.
Clicking through downloads an executable file from the "short URL" service cutt.ly and creates a hidden directory, then tries to modify Windows Defender’s settings for evasion purposes, adding all the malicious additions to the exclusion list.
The executable from the short link that leads to githubusercontent installs the (RAT).
The Windows malware seems to be related to a campaign known as ClearFake, which is a fake browser update activity cluster that compromises legitimate websites with malicious HTML and JavaScript.
Proofpoint researchers note that leveraging unique social engineering to run PowerShell and install malware is a technique used in TA571 infections and their ClearFake operation, which can lead to ransomware.
The malicious payload contains the RedLine Stealer malware, which is widely used by threat actors to harvest browser data such as saved credentials, autocomplete data, and credit card details, as well as system information. More recent RedLine versions target cryptocurrency wallets and FTP and IM clients, and it can also upload and download files and execute commands.
TA571 is a spam distributor aiming to deliver and install various types of malware for their cybercriminal customers.
Recently, a novel ‘Fake Browser Update’ campaign compromised vulnerable websites to push malware downloads via Chrome update pop-ups and used legitimate plugins to evade detection by file scanners.