WordPress Plugin “Total Donations” Zero-Day Exploit Compromises Hundreds of Websites
- The Total Donations plugin comes with serious security holes that can lead to WordPress site takeover.
- The problem was reported by Defiant researchers who found 49 exploitable AJAX actions in the plugin.
- Users are urged to completely remove the plugin, as the development and maintenance of it seem to have stagnated.
According to a researcher working for Defiant, the Total Donations plugin for WordPress contains a severe vulnerability (CVE-2019-6703) that allows unauthenticated remote access to the website that contains it, even if it’s disabled. Defiant specializes in firewall solutions for WordPress, and are keen to explore the various security holes that may lurk here and there. In the case of the Total Donations, the team has tried to warn the plugin’s development team, but they failed, so the current advice is to completely remove it from the website.
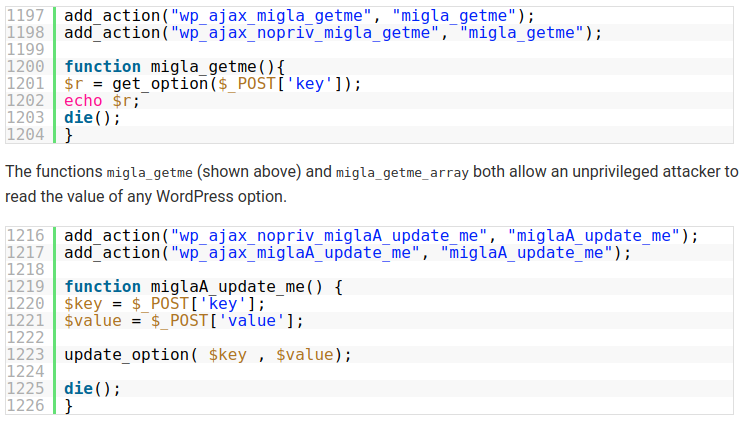
Total Donations is a commercial plugin that helps sites create donation campaigns and accept payments from their visitors. The official plugin’s website, however, seems to be inactive for quite some time now, and users complain that no one responds to their bug reports for over a year now. Defiant researchers have located the problem in the incorrect access control in migla_ajax_functions.php, allowing attackers to arbitrary set WordPress option values, and essentially take control of the website. As the development team has seemingly abandoned the project (without this having been confirmed through any kind of an announcement though), there is no fix to be expected any time soon, and so all users of the particular plugin are advised to remove it from their websites entirely.
Even if the plugin is deactivated, the attackers could call the file directly, still gaining unauthorized access to the vulnerable websites. More specifically, Defiant found that out of the 88 AJAX actions that are registered to the website by Total Donations, the 49 are exploitable and can potentially lead to the acquisition of sensitive data. While the site takeover is the scariest scenario, it’s not the only one. Total Donations vulnerabilities also allow access and modification to the set payment plans, access and modification to the mailing lists (either on MailChimp or Constant Contact), and even more. In general, there seems to be no access control security implemented to the tool, so it’s inherently unsafe.
Image source: wordfence.com
The plugin is no longer available for purchase as it has been delisted from the marketplace of the developer, but as no abandonment notice was circulated to the users of the plugin, many valuable WordPress websites out there are open to takeover. With the revelation that came from Defiant, attackers are bound to point their scans towards the existence of Total Donations, so removing it immediately is now of exigent urgency.
What are your thoughts on the use of plugins on WordPress sites? How do you determine the safety and reliability of those that you are using on your site? Let us know in the comments below, and don’t forget to share this story through our socials, on Facebook and Twitter.