WordPress Plugin ‘Slimstat’ Vulnerable to Code Injection
- Slimstat Analytics plugin is vulnerable to a visitor XSS storing handout to attackers.
- The developers released a fixing patch shortly after they were notified about the problem.
- More than 100 thousand WordPress websites are affected by the flaw, so updating immediately is advised.
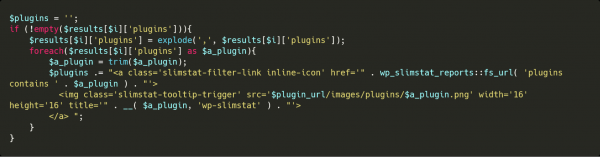
According to a report by Sucuri researcher Antony Garand, the “Slimstat” WordPress plugin is vulnerable to arbitrary JavaScript code injection in its access log functionality. XSS vulnerabilities, or “cross-site scripting” are security flaws that allow attackers to inject their own scripts into web pages, enabling them to bypass access controls that are in place. According to the researcher, Slimstat maintains a visible admin dashboard, where the access log is present, containing various details about the website visitors. The information that an attacker can gather through this includes the visitor's IP address, operating system, browser, and installed plugins.
All Slimstat plugins below version 4.8.1, which is the one that fixes the flaw, are vulnerable. This problem affects over 100 thousand websites out there, where the analytics plugin is currently deployed. The Slimstat developers have managed to fix the problem and release the relevant patch only four days after the researcher notified them of the problem, so that says something about their notable professionalism. Using a WordPress plugin made from an irresponsible developer can easily lead to complete website takeover, so treating your customers with respect and responding to security flaws almost immediately is critical.
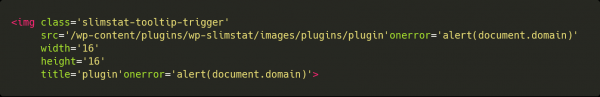
According to the details given in the report, the attacker could create an analytics request that is executed upon the next admin login on the website. The researcher has demonstrated that it’s possible for an attacker to get access to the stored XSS by triggering a “onerror” event that would be the result of an invalid image snippet injection. The fact that the attacker can have access to the access log entries makes the targeted next steps possible.
image source: blog.sucuri.net
image source: blog.sucuri.net
Unfortunately, Slimstat’s updates webpage was last updated with the 4.6.9 release, so it has stagnated, and we can’t get more details about what other fixes the latest version brought. However, if you are using Slimstat Analytics on your website, make sure that you update the plugin immediately to stop the storing of visitor XSS. By searching around, I have found that Slimstat was again troubled by XSS flaws back in 2015, which was also addressed quickly by the developers.
Are you using Slimstat on your website? How often do you update your WordPress plugins? Let us know in the comments down below, and help us reach to more people out there by sharing this post through our socials, on Facebook and Twitter.