Recently Patched Windows Flaw Exploited as a Zero-Day in Infostealer Attacks
- A recent Windows MSHTML spoofing zero-day flaw was added by CISA to its Known Exploited Vulnerabilities catalog.
- The actively exploited vulnerability allows a remote attacker to execute arbitrary code.
- Void Banshee APT leverages this exploit in a campaign that deploys infostealers.
The recently patched Windows MSHTML spoofing zero-day bug, exploited by the Void Banshee APT hacking group, has prompted CISA to take action. U.S. federal agencies have been directed to secure their systems against this critical vulnerability by October 7.
Initially disclosed during the latest Patch Tuesday, Microsoft classified CVE-2024-43461 as not exploited but later confirmed exploitation in attacks.
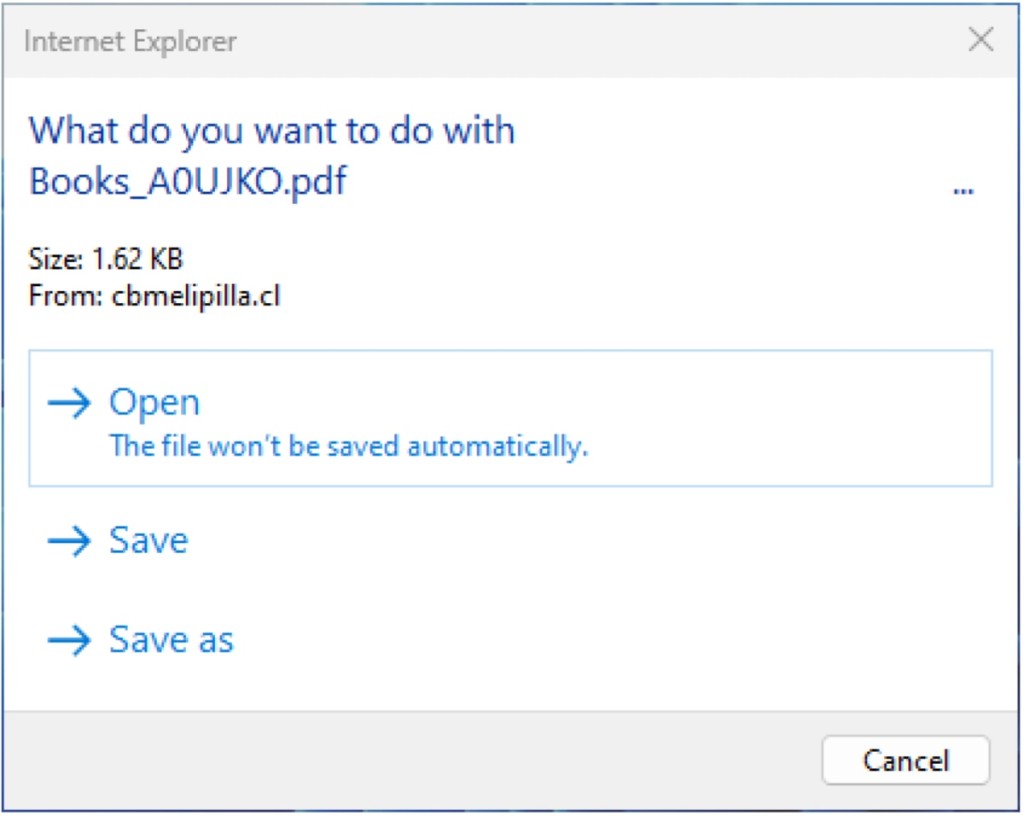
Remote attackers can execute arbitrary code once they deceive users into accessing malicious web pages or files. The flaw exists within the way Internet Explorer prompts the user after a file is downloaded.
Exploitation involves disguising HTA files as PDFs using encoded braille whitespace characters to obscure the file extension.
This vulnerability enables the deployment of the Atlantida info-stealing malware, which can extract passwords, authentication cookies, and cryptocurrency wallets. The Void Banshee attacks primarily target organizations in North America, Europe, and Southeast Asia for financial theft and data exfiltration.
Used in conjunction with CVE-2024-38112, another MSHTML spoofing vulnerability, it forms a critical exploit chain that was utilized by attackers before July 2024, as Microsoft revealed.
Microsoft's September 2024 Patch Tuesday provides security updates for 79 flaws, including 3 actively exploited and 1 publicly disclosed zero-days, and fixes for 7 critical vulnerabilities, which were either remote code execution or elevation of privilege flaws.
In August, security researchers discovered that attackers with sufficient knowledge of CSS could bypass Microsoft 365's measures for preventing phishing by manipulating the email’s HTML code.