Windows 10 Installations in Risk from 40 Drivers of 20 Vendors
- Researchers discover severe vulnerabilities in 40 drivers from 20 hardware vendors.
- Microsoft doesn’t look like being in a position to act as the safety net for the users.
- Drivers can open the door to all types of attacks, including the most critical and catastrophic.
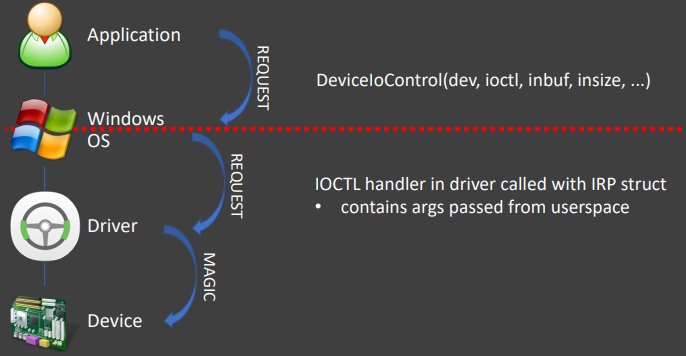
Device drivers are special types of software interfaces that link your hardware with the operating system kernel, translating instructions between the two. Due to their role and its “elevated privilege” nature, they have the potential to introduce serious risk for the user, and this is something that we have repeatedly seen in the past. According to a report that was recently published by Eclypsium security researchers, the current situation is pretty dire, as the risky drivers concern an extensive array of devices coming from twenty different vendors. This means that virtually everyone is vulnerable to an attack by people who know how to take advantage of each flaw that underpins a particular device.
image source: https://eclypsium.com
As Eclypsium reports, their analysis revealed that more than 40 drivers from at least 20 vendors are vulnerable. What makes the situation even worse is that all of these drivers are signed by Microsoft's Windows Hardware Quality Labs, so they are certified. Instead, these drivers should be identified and blacklisted, but it seems that a process of detailed scrutiny and review is not in place, neither in Microsoft nor in the development teams of the hardware vendors that are pushing the risk-inducing drivers.
The list includes high-profile hardware manufacturers, BIOS system developers, and microprocessor creators. The vulnerable vendors are ASRock, ASUS, ATI (AMD), Biostar, EVGA, Getac, GIGABYTE, Huawei, Insyde, Intel, MSI, NVIDIA, Phoenix Technologies, Realtek, SuperMicro, and Toshiba. There four more vendors that haven’t been disclosed in the relevant DEF CON presentation because they are deployed in highly critical environments and haven’t managed to push the fixing updates to all of their customers yet.
image source: https://eclypsium.com
Attackers could use the vulnerabilities of the 40 drivers to scan the target system, escalate to kernel privileges, download and install malware or spyware, stay hidden and exfiltrate user data for years, conduct DoS attacks, install ransomware, or straight out brick the infected device. Unfortunately, even if Microsoft puts the particular drivers in a blacklist, Windows have no mechanism that will stop their installation and deployment. The only way that people can stay safe is by updating their firmware and hardware drivers as soon as an update becomes available. Finally, if there’s an old driver in your system and you have already removed the associated hardware, you should remove the driver software immediately.
Do you regularly update to the latest and most up to date driver? Let us know in the comments down below, or on our socials, on Facebook and Twitter.