Three Widely Used VPN Products Found to Be Leaking IP Addresses
- Hotspot Shield, PureVPN, and Zenmate VPN were found to have vulnerabilities in their web browser extensions.
- One of the vendors fixed the flaws, the other one acknowledged them and offered a solution, and the third rejected the reports as outdated.
- In all three cases, the main problem was the leaking of the user’s actual IP address.
One of the main reasons an internet user deploys a VPN (a virtual private network) would be hiding their IP address. The IP address reveals your rough geographical location and links you to the ISP that is serving your internet line. It can be used as a clue to force your telco to share customer data with the law enforcement authorities and enables websites to blacklist certain users.
When using a VPN, your IP address is switched to that of the server you've selected to route your internet traffic through. At the same time, everything passes through an encryption tunnel so that nobody can work backward to look up the original IP address. In some cases, though, this doesn’t work as expected, and VPN tools can leak this sensitive information.
vpnMentor has teamed up with researchers from Cure53 and tested three popular VPN products, namely the Hotspot Shield, PureVPN, and Zenmate. Unfortunately, they found that all of them leak sensitive user data, including the IP address.
Starting with Hotspot Shield, the first problem lay in hijacking all traffic (CVE-2018-7879) through the Chrome extension. The second bug was a DNS leak (CVE-2018-7878), and the third one was an IP leak (CVE-2018-7880). Hotspot Shield received the reports from the researchers and fixed the bugs promptly. It is important to clarify that these flaws didn’t affect the solution’s mobile or desktop app, but only the Chrome extension.
Source: vpnMentor
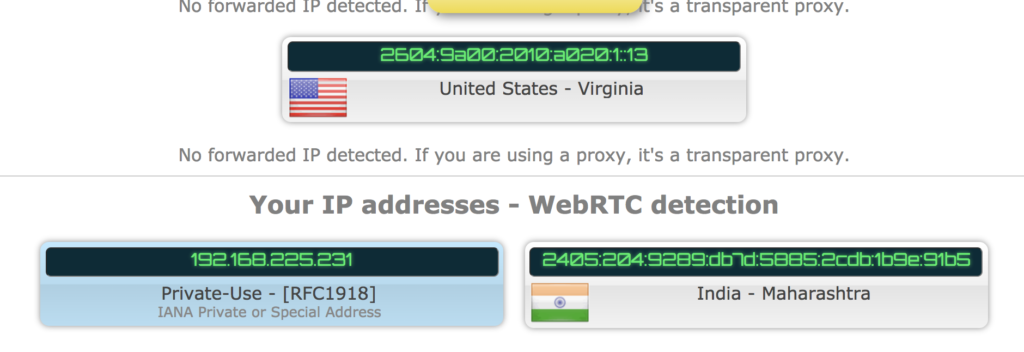
In the cases of ZenMate and PureVPN, the reception of the team’s reports wasn’t as straight forward, so there’s some confusion here. On ZenMate, the team found a webRTC leak that revealed the real IP address of the user.
The vendor responded by saying that WebRTC has known privacy-risking issues for them, but they have decided not to block it because many web services rely on it. Those who want to mask their IP address while using WebRTC are advised to use the WebRTC Network Limiter extension for Chrome.
Source: vpnMentor
On PureVPN, the researchers managed to find their real IP address by using the Firefox web browser. PureVPN hasn’t accepted that the reported flaw is still there, and believes that the researchers used an outdated version of its software, claiming to have fixed the particular bug since March 07, 2018. vpnMentor however, maintains that this isn’t the case, and warns the users to be careful while using the product.
Again, in both ZenMate and PureVPN, the flaws concern web browser extensions, and not the mobile or desktop version of the software.
Read More:
- CyberGhost VPN Releases Q2 2020 Transparency Report
- Several Hong Kong-Based VPN Apps Exposed Their Private User Data Online
- NordVPN Has Successfully Completed Yet Another “No-Logs” Audit