Who’s Hiding Behind the “Pay2Key” Ransomware Group?
- White-hat researchers have followed the money of four ransom payments to “Pay2Key”.
- The actors have strong links with Iran, which makes sense considering their insistence on targeting Israeli firms.
- The Iranian crypto exchange they’re using could be holding their identification details.
CheckPoint has been following “Pay2Key” closely since last week, trying to figure out whatever they can about the emerging ransomware group. As the actors managed to compromise a notable number of targets, received payments, and posted stolen data online, they have left some crumbles of evidence behind.
More specifically, CheckPoint researchers have managed to trace Bitcoin transactions and gather more clues about who could be behind the wallets with the help of the ‘Whitestream’ blockchain intelligence firm.
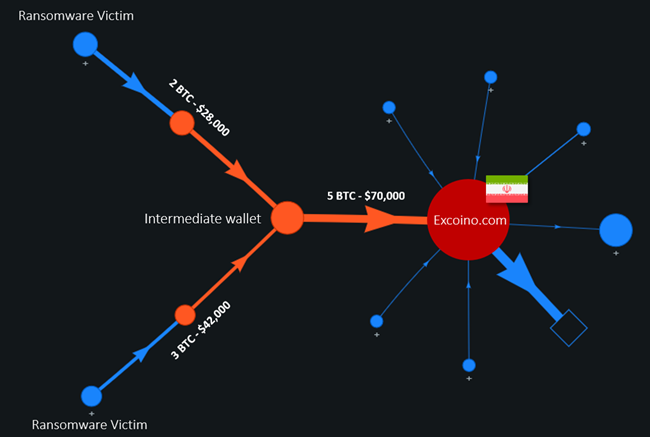
First of all, Pay2Key is clearly focused on Israeli targets, although they have had some victims from central Europe, too. Secondly, Pay2Key is no different from the “industry standard” of stealing and leaking sensitive data on a dedicated Onion domain. The most useful kind of evidence comes from the money routes, though, and the researchers had four individual cases of payment to analyze.
The payments went to Iranian cryptocurrency exchange ‘Excoino,’ which matches the assumptions made based on the insistence against Israel. The payment goes to the wallet ID provided in the ransom note, and then the actors transfer it to an intermediate wallet.
From there, the money goes through a third jump to a high-activity cluster wallet address. The researchers used a “Wallet Explorer” service to verify the link between each step and managed to develop confident ID linkages.
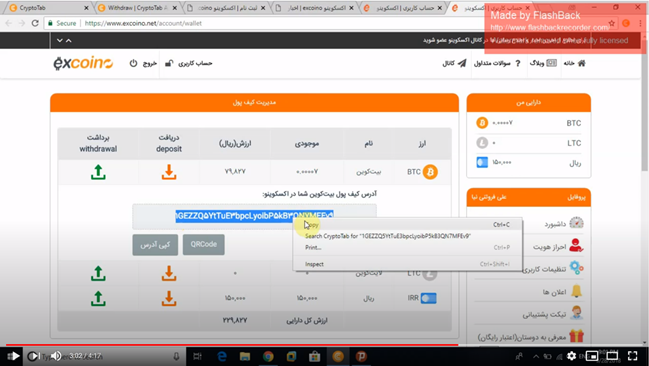
Since Excoino is a legitimate service, they require users to register using a valid Iranian phone number and ID/Melli code (national ID number). To trade in the platform, one would need to upload a copy of their ID card, so there can be no anonymous malicious activity there unless it goes unnoticed and unreported. Excoino urges people to report suspicious transactions to the Iranian Cyber Police for investigation, so this is why the CheckPoint research is so valuable in this case.
We now know that the actors are almost certainly based in Iran and that an Iranian-based exchange is involved. We also know that this platform could be holding the identification details of the actors.
Of course, stopping Pay2Key won’t stop ransomware trouble in Israel, as Iranian hackers are always active against Israeli companies. However, it is a form of reaction against crooks and proof of why white-hat research should never be considered futile.