WhatsApp Desktop Found to be Vulnerable to Code Injection Attacks
- A flaw in WhatsApp client for macOS and Windows could have resulted in RCE attack scenarios.
- The exploit was made possible thanks to the lax CSP rules and the outdated Electron kit.
- The vulnerability has been reported to Facebook and is already fixed now, so update your WhatsApp client now.
Researcher Gal Weizman of PerimeterX has discovered a critical flaw in the WhatsApp desktop client, reported it to Facebook, and helped them fix it. That said, if you have updated your client to the most recent version, you are no longer at risk. The researcher was initially inspired by a CheckPoint report which detailed how one could edit the messages of others, tamper with the metadata, and craft messages that can bypass all filtering mechanisms in place. He took this concept to rich preview banners that contain links and other interesting elements.
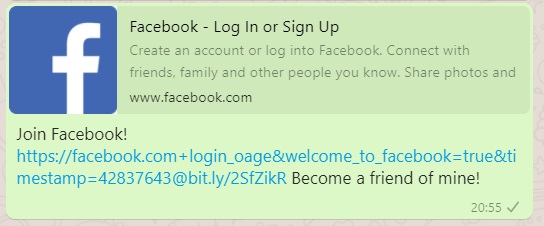
So, after working on this for a while, Weizman was able to re-create messages that appeared to derive from Facebook itself, and which could contain links that lead to malicious websites. To make the trickery even better, the man was able to craft a URL that even looked like it comes from Facebook’s official domains, following common phishing scam methods. Having done that, the researcher proceeded to experiment with JavaScript URIs, and after some trial and error, he managed to achieve one-click persistent-XSS. This flaw however only works on non-Chromium based browsers, but it’s still highly critical.
Source: PerimeterX Blog
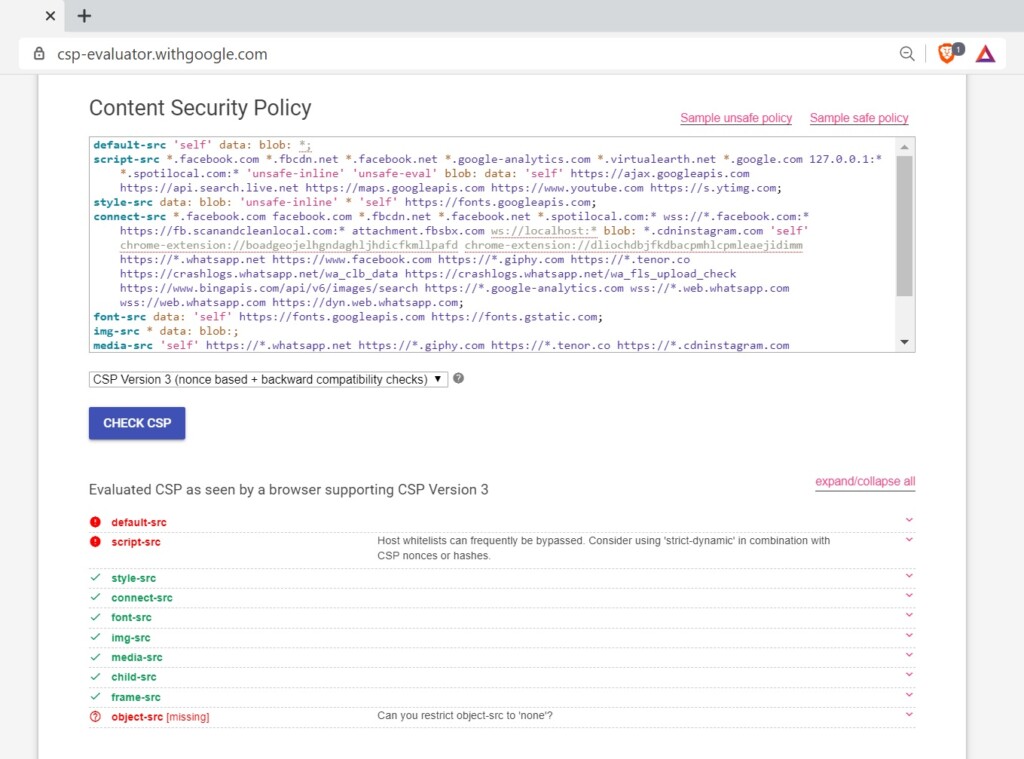
Bypassing the CSP (Content Security Policy) used by WhatsApp was the final step of the way, and the payload must remain hidden in the message for this exploit to work. Weizman took leverage of the absence of the “object-src” directive in the CSP to load whatever iframe he wishes. This means that he could link the tampered message to an external source of code execution, without any regards to the size. The final step was to execute that code on “web.whatsapp.com” through XSS side-loading. Since WhatsApp has desktop clients for both Windows and macOS, there’s a way to launch a remote code execution attack through this method.
Source: PerimeterX Blog
To stay safe from this kind of attack, you should be careful with the messages you receive, and you should always review their form. If they look more like JavaScript than casual text, then maybe someone has modified it before it reached you. If you have received any links from unknown accounts, then avoiding to click on it is a no-brainer. The researcher concludes by commenting that this exploit would have not worked if the CSP rules were properly configured or if WhatsApp didn’t opt to use a severely outdated version of Electron. As he characteristically writes: “It is 2020, no product should be allowing a full read from the file system and potentially an RCE from a single message.”