Here’s What Ransomware Gangs Do With the Data That Was Paid for Deletion
- There’s been over a year since ransomware groups added data-stealing in their extortion methodology.
- We now have a clear picture of what happens with the data that was paid with the hope that it’ll get erased.
- Spoiler alert, paying the ransom doesn’t do anything to benefit the victim on that part.
Before 2020 and the trend that has ransomware groups stealing their victims’ data before encrypting it, companies had the option of keeping backups and completely skipping the whole ransom payment “negotiation” part. This has changed now, as crooks hold the data and threaten to leak it online, which often has catastrophic consequences for the victims’ business.
Thus, ransom payment rates are on the rise, and the first evidence on what happens with the stolen data is now available.
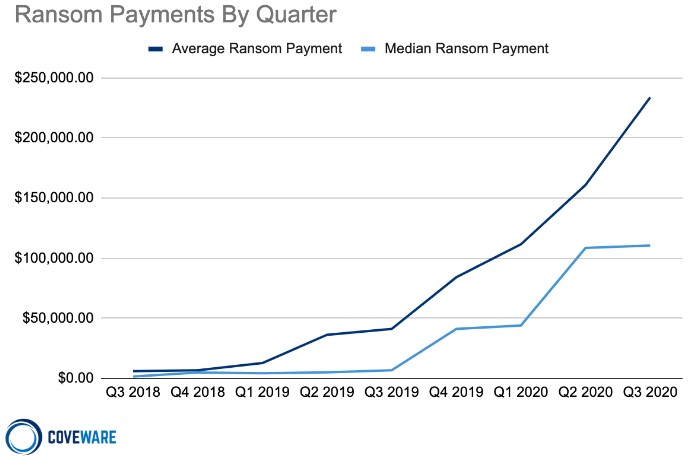
As Coveware presents in their report, not only the volume of the payments has increased in size, but also the average and median ransom payments. Ransomware actors are targeting big players and go for larger payouts, so this is to be expected.
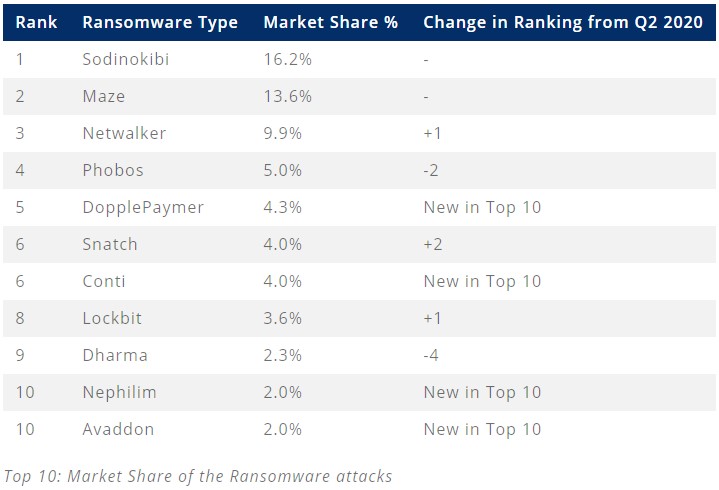
As for who does the greatest damage, Sodinokibi, Maze, Netwalker, Phobos, and DopplePayment are on the top.
If someone holds your data and this constitutes the main lever of pressure to force you to pay the ransom, would paying them guarantee the deletion? Many ransomware groups like to mention stuff like “good reputation,” which they supposedly care to maintain. So, they try to convince the victims that they are “professionals” who follow a systematic approach in what they do, and thus, paying them will have the exfiltrated data erased.
Related: ‘Mattel’ Toys Disclosed Summer Ransomware Attack That Impacted Its Business
Here’s what they actually do, though, according to Coveware:
Sodinokidi: The crooks return a few weeks after the payment for a second round of extortion using the same set of data that they promised to delete.
Maze / Sekhmet / Egregor: The stolen data had already been leaked online even before the victim had the chance to pay the ransom.
Netwalker: Data that was paid for deletion was posted online anyway.
Mespinoza: Data that was paid for deletion was posted online anyway.
Conti: The hackers showed fake files as proof of deletion, keeping the actual data for whatever purpose.
It is clear that paying the ransomware groups doesn’t guarantee anything, and it would be naive to think otherwise. Even if the threat actor deletes the stolen data, others could be holding copies of it, hoping to sell it on the dark web in the future. In some cases, we have seen the posting of the data by mistake, so there are even inadvertent leaks that could render ransom payments worthless.