What Kind of Malspam Circulates in the Time of the COVID-19 Pandemic?
- The situation in malspam campaigns has been heavily affected by the ongoing pandemic.
- Spammers are impersonating health authorities or try to induce greater fear for the recipients.
- In most cases, the payloads are info-stealing trojans or remote access tools (RATs).
There’s a broad spectrum of malicious actors that are looking to exploit the current situation, using Coronavirus as the common denominator for their malspam campaigns. Naturally, there are various approaches, depending on the targets or what the actors believe will work out best for them. CrowdStrike researchers have compiled a list with the most interesting malspam types right now, so here we go.
Source: CrowdStrike Blog
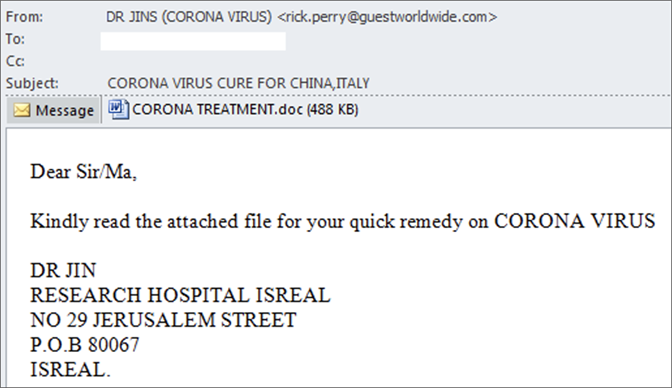
First, there are the “Coronavirus treatment” documents attached to emails supposedly sent by doctors. The documents feature malicious macros that fetch additional payloads if opened on an office suite with macros enabled. Interestingly, most of the “cure” malspam attempts pretend to derive from Israel, as the country is known for its superior research programs.
Source: CrowdStrike Blog
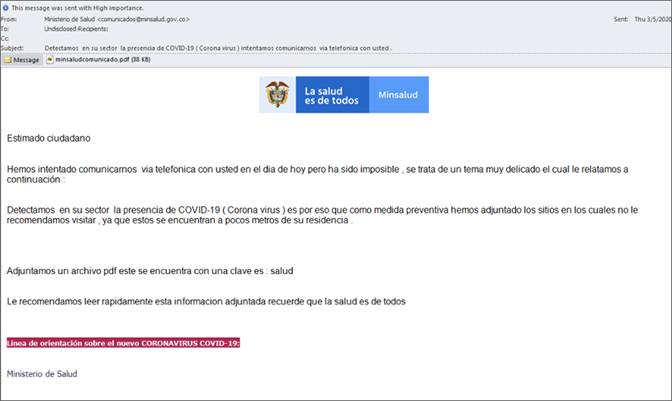
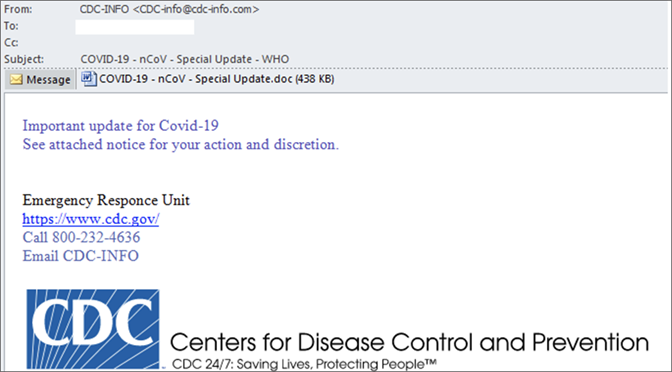
In the second example, some emails impersonate governments and the Ministry of Health in particular. These are most prevalent in South America, but they can concern other places in the world, too. In these cases, the attachment is a PDF file that contains the official letterheads of the spoofed entity, incorporating a link to a phishing or a RAT-dropping webpage. The researchers have recorded attempts to impersonate the Centers for Disease Control and Prevention in the United States, using a weaponized RTF document to drop the Warzone malware.
Source: CrowdStrike Blog
A wholly different case is that of a “screensaver” file (.SCR) that comes as an ISO attachment. The choice of the file type is meant to help trick the recipient into thinking that the file can’t be posing any risks. However, it is a Base64-obfuscated executable that serves as a dropper of batch files, executables, and libraries used for DLL hijacking.
Source: CrowdStrike Blog
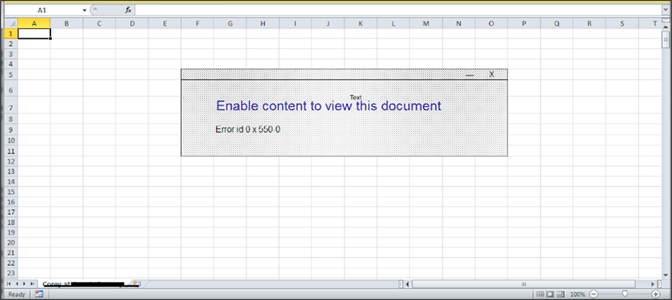
Next, there is the type of properly-crafted malspam that doesn’t come with spelling or grammar errors. Usually, these have Excel attachments that download the malware by running PowerShell scripts through macros. It results in the fetching of .dll, .exe, and .ini files onto the victim’s system. The final payload is the NetSupport Manager RAT, which supports screen recording, network discovery, and input device takeover.
Source: CrowdStrike Blog
Finally, there’s the malspam type of fear-inducing messages using phrases like “COVID-19 UPDATE!!” or “coronavirus preventive measures.” The sender in these cases is supposedly a health-related organization or authority, and the payload is usually the LokiBot trojan. To obfuscate the dropping step, the actors are using a Delphi-compiled wrapper that also helps get around debugging and virtual machines.