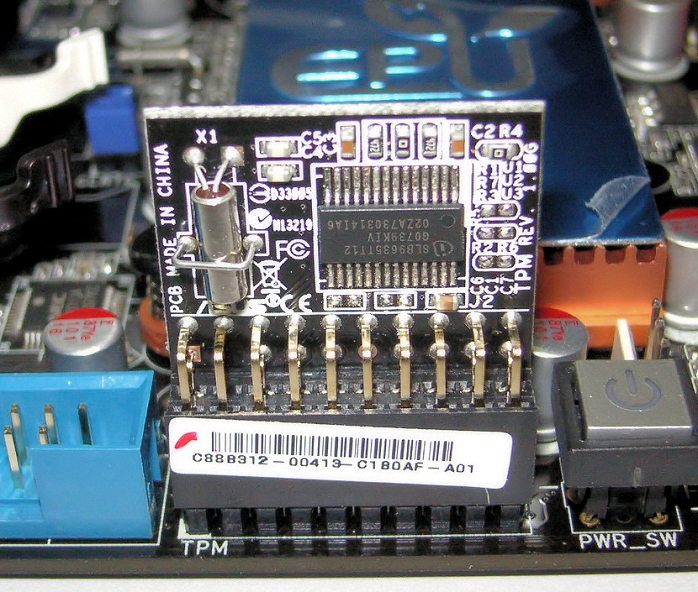
What’s This “TPM” You’ve Heard About?
Full disk encryption is becoming a somewhat common security measure on modern computing devices. If you have a modern smartphone, especially a flagship model, you were probably prompted to encrypt the whole machine.
The same goes for modern computers running Windows 10. If it’s a work machine, it’s likely to have full disk encryption enabled using something like BitLocker.
Full disk encryption means just what the name suggests - everything is encrypted. So if someone steals the device or just removes the drive, they can’t access any files at all. This is, in contrast, to just using software to encrypt a portion of your drive. Such as a specific folder and all the files in it.
While anyone can download some encryption software and apply it to their whole disk, some encryption solutions need something called a “TPM”. If you’ve bought a business laptop or something similar recently, chances are you’ve already got one. But, what exactly is a TPM module?
Hardware Helper
The TPM or Trusted Platform Module is a hardware component that lives on your computer’s motherboard. It contains a dedicated processor known as a cryptographic processor. Additionally, it has dedicated storage space inside it. So in effect, the TPM is a simple computer in its own right.
Its primary job is to generate robust and randomized encryption keys. It then stores a part of the key in its internal memory and the rest of the key on the disk itself. This means that you need both the TPM and the disk to decrypt the information. Stealing or otherwise getting access to the disk won't help you decrypt it since no one part of the system has the full key.
Let's take a closer look at the components of a TPM.
The Cryptoprocessor
A cryptoprocessor is a type of microprocessor that's dedicated to doing operations related to cryptography. That means its nothing like the CPU that runs all the software you use on your computer.
Because this processor is designed from the ground up to do a small range of jobs, it tends to be very fast and efficient. These sorts of processors are found all over the place. They are in smart cards, ATMs, and mobile devices.
Some cryptoprocessors are capable of general purpose code execution, but most are not.
TPM Cryptoprocessor Components
The cryptoprocessor in a TPM has several core components that allow it to do its job. The first is the random number generator. All encryption keys require a source of randomness in order to make the key as strong as possible. If a number generator has a predictable pattern, then it can be exploited.
It also contains an RSA key generator. RSA is an incredibly powerful encryption algorithm with very long keys. 2048-bits long in many cases. While RSA would be slow if used for full disk encryption, it is commonly used to encrypt the keys that in turn unlock the encryption of the disk itself. Whatever the RSA key is needed for, the TPM can generate them.
The processor also contains a hash generator. Hashing is a special one-way encryption method that allows for authentication of digital signatures and passwords.
TPM Memory
The TPM also has to store cryptographic information. So each TPM has the internal secure memory which stores keys and other information related to authentication and encryption. However, there's no reason to think that getting access to the TPM itself will give someone access to that information. Since this data also has its own strong protection.
Do I Have a TPM?
If your computer has a TPM, it will almost certainly be listed in the spec sheets. If you can't find it, it makes sense to look for it under the motherboard's features.
Of course, you could simply try to use a TPM-dependent encryption program such as BitLocker. If you don't have one, it won't work.
Even if you don't have a TPM in your computer, all may not be lost. Some motherboards have a slot where you can install a TPM bought separately. This is mostly true of desktop computers, but some laptops may also provide a way to add a TPM. Just make sure you get one specifically recommended by the motherboard maker.
The TPM Isn't Perfect
TPM's are widely used in corporate and professional context. They provide a strong implementation of key generation, management, and authentication. That doesn't mean they are the final word in enterprise device encryption.
For one thing, TPM modules are black boxes from our point of view. The companies that make them could ostensibly use TPMs to spy on or manipulate the computer it is installed in.
There are plenty of full-disk encryption packages out there that don't support TPMs at all. This is mainly due to the argument that TPM is only effective against physical tampering. At the same time, with physical access to a computer and some time, the TPM could be defeated in some ways. For example, sticking a USB keyboard logger into a target machine and retrieving it later would not be mitigated by a TPM at all. Just about any security feature can be beaten if you have unlimited time and energy, so this is not a specific weakness of the TPM.
Should You Care?
If your computer didn't come with a TPM, is this a major issue? The truth is that trusted computing isn't all that important to the average user. It has a useful function within the context of a large enterprise, but the average person shouldn't spare much concern.
Unless you've bought a business class computer, you are not likely to get a TPM. That makes it a pity that you can't take advantage of the disk encryption software that comes with the latest version of Windows. Then again, many excellent software products do pretty much the same thing and don't rely on the TPM to work. Either way, if you are privacy conscious full-disk encryption is well worth looking in to.