When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
Phishing Attacks B-Gone (What Is Phishing and How to Protect Yourself From It)
Pretty much everyone has heard of phishing attacks by now. It's hard not to since you see "phishing" plastered everywhere online. But how many of you actually take it seriously?
A recent study showed that many people underestimate phishing attacks, and believe they're less likely to fall for them than other people.
"It won't happen to me," many of you likely tell yourselves as you open an email from PayPal and click the link inside it without even checking if the sender's address is correct.
Maybe you're lucky, and nothing happens because the email was legit. Or perhaps you end up on a phishing website that impersonates PayPal, and you hand over your login credentials to hackers.
Contrary to what you might think, the chances of you falling for a phishing attack are pretty big right now. These cyber-attacks are currently at an all-time high, and any wannabe hacker can set up a phishing site. A custom phishing page only costs between $3 and $12.
So we strongly recommend you stick around and keep reading. We put together this complete guide to teach you everything about phishing. Don't worry - we kept things simple and made the format easy to scan too.
- What Is Phishing?
- How Much Damage Can Phishing Cause?
- Types of Phishing
- Is Pharming the Same as Phishing?
- Does a VPN Protect You from Phishing?
- How to Spot Phishing
- How to Protect Yourself from Phishing
- What to Do If You’re Dealing With Phishing
- How to Report Phishing
- What to Do If You Interacted With Phishing Emails
What Is Phishing?
The simplest way to define phishing is as hackers trying to scam people out of their money and/or sensitive information (like Social Security Numbers). Normally, they use emails, but they can also resort to phone calls and social media messages.
Originally, phishing attacks were part of massive spam campaigns that targeted huge numbers of people. They operated on the idea that at least a small percentage of people would interact with them.
But people eventually grew more aware of how dangerous spam was. Also, email service providers started filtering spam messages. So, hackers had to adapt.
That's why today's phishing attacks are so sophisticated. They're more likely to target specific groups of people (the elderly, teens, CEOs, PayPal users, etc.). Also, cybercriminals do more research on their victims to personalize their messages, making them more relevant to their targets.
How Phishing Works
Phishing attacks vary a lot, so we can't use one simple explanation. All the "work" that goes behind one phishing attack can be completely different for another attack.
Still, we put together a list of patterns that are usually common among most phishing attacks. In short, here is what hackers do behind the scenes:
- First, they set up a fake website or web page. Usually, it will copy legitimate brands like payment processors, banks, or social media sites. In some situations, scammers don't use fake sites at all.
- Next, they target people with fake emails. They'll pretend to be someone in a position of authority (police officer, bank clerk, IT support, CEO, etc.). They can also contact people on social media or call them. Sometimes, they might not contact people at all. Instead, they'll use MITM (Man-In-The-Middle) attacks to redirect people to phishing sites.
- Most of the time, they'll try to convince you to click on a link. Naturally, the link will take you to the fake sites they set up. The website will either infect your device with malware or try to trick you into typing sensitive information (like credit card details or login credentials), which it will log.
- Alternatively, hackers might try to convince you to download an attachment. Obviously, it's just a malicious file that takes over your device if you interact with it.
- If scammers contact you over the phone, they'll try to trick you into revealing valuable information - credit card details, passwords, or sensitive company data.
- Attackers will almost always use a tone of urgency to pressure you into deciding on the spot without thinking about it. They might act threatening by claiming you're under investigation for fraud, or they might be overwhelmingly energetic and cheery, claiming you won a special prize.
Phishing Attack Examples
If we were to offer an example of every type of phishing attack, this article would never end. Or it would, but it'd be novel instead of an article, and it would need 24/7 updating.
So, we'll offer you some examples of what a phishing attack looks like instead. Here are three that should give you an idea of what to expect:
PayPal Messages
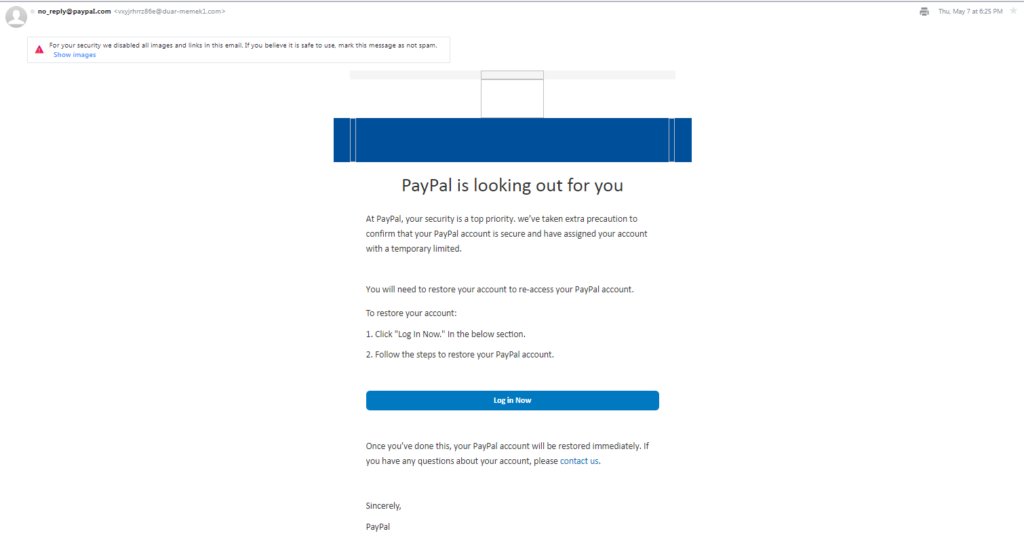
PayPal is one of the most popular payment processors on the Internet. It's also a favorite target for cybercriminals. So much so that PayPal-related phishing is at an all-time high right now.
Scammers will usually pretend to be someone from PayPal and claim you need to access a link to restore your account.
That, or they might say your account was compromised, and you need to follow their instructions to secure it.
Or that you need to confirm you're the account holder by clicking a shady link, downloading a weird attachment, or sharing sensitive personal information.
Here's a screenshot of how a PayPal phishing message looks like:
COVID-19 Messages
The COVID-19 pandemic has the world turned upside down. And cybercriminals are taking advantage of that by pumping out dozens of coronavirus-themed phishing attacks.
Back in April, Google apparently saw 18 million instances of COVID-19 phishing and malware over the course of a single week. And that's in addition to the 240+ million daily COVID-19 spam messages they registered, which are likely used in phishing attacks.
In their words, Google blocks "99.9%" of those threats. That still means 0.01% phishing messages are getting through. Not to mention people who don't use Gmail are even more at risk.
Fake cures and vaccines, made-up donations, tax refunds, non-existent guidelines, false links for Zoom meetings. The list just goes on and on. Here's an example of a COVID-19 phishing attack from the Google Cloud article we linked above:
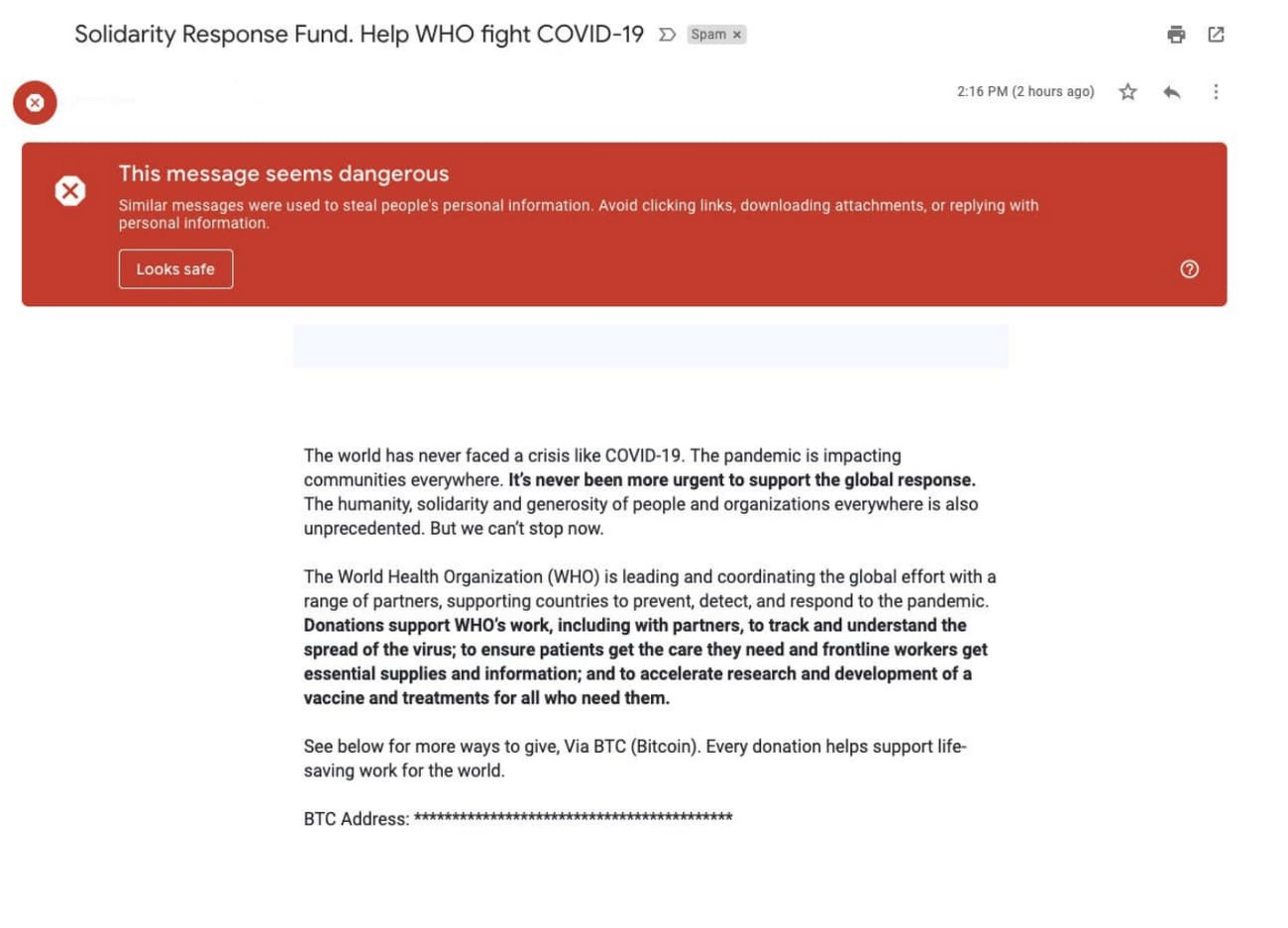
BTC donations for the WHO. Yes, that seems totally legit.
If you want to see more examples of COVID-19 phishing attacks, we recommend checking out these articles:
- 10 COVID-19 scams spreading right now that people are falling for
- COVID-19: Real-Life Examples of Opportunistic Phishing Emails
- Coronavirus: How hackers are preying on fears of Covid-19
Related: How Hackers Use Coronavirus Panic to Their Advantage
Dropbox Messages
Dropbox is a pretty popular tool for storing and sharing files - especially among businesses. So it's no wonder hackers love to target Dropbox users with phishing emails.
Most of the time, they'll send messages like this one:
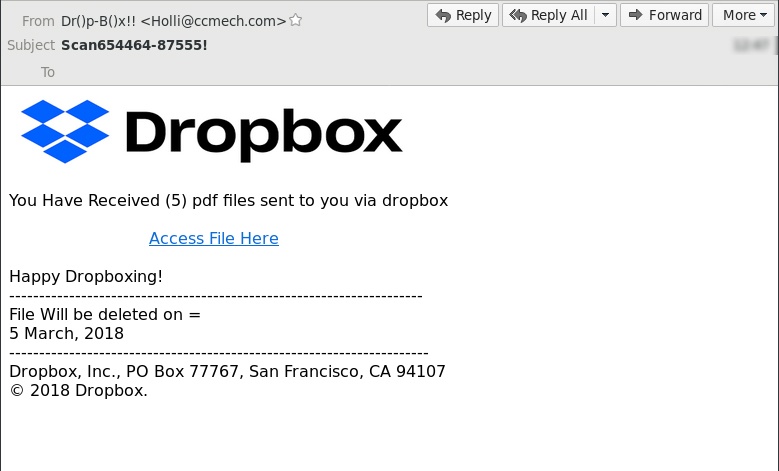
It's simple and makes people click without even looking. The idea is to redirect you to a site that will capture the Dropbox login credentials you type. Scammers likely hope they'll get access to some juicy information - like customer billing information, for example.
How Much Damage Can Phishing Cause?
A lot.
For companies, It's one of the main reasons they suffer data breaches. According to research, around 32% of data breaches involve phishing. And even more data shows that US businesses lose approximately half a billion dollars per year because of phishing attacks.
Overall, here's how phishing damages businesses:
- It causes loss of intellectual property.
- It results in the theft of valuable company data.
- Phishing attacks compromise employee accounts and customer data.
- Phishers steal money from business and client accounts.
- It compromises company networks and devices with malware.
- It damages a company's reputation.
And things aren't better for regular Internet users either. Because of phishing, they become the victims of identity theft, credit card theft, malware infections (especially ransomware), compromised accounts, and even sextortion scams.
Related: Data from Old Breaches Used in “Sextortion” Scam – Barracuda Labs
Types of Phishing
You already know about the average phishing emails - the ones where scammers pretend to be IT support, police officers, bank managers, payment processors, and so on.
Besides that phishing method, there are also many others:
Spear Phishing
Speak phishing is a regular phishing attack, but it's much more personalized. Also, it tends to target specific people (like CEOs or bloggers) instead of a large number of random addresses.
Scammers do a lot of research beforehand: they check the victim's social media, check company websites, read articles about them, and track their activities on online forums or in online games.
They do all that to craft a customized message that is 100% relevant to their victims. They're much more likely to interact with malicious links and files or share sensitive data this way.
Whaling
Whaling attacks normally target people in senior management positions at large companies.
These attacks rely on heavy research to make the phishing messages very hard to detect. Usually, the hacker will even go as far as learning the corporate lingo associated with their target to communicate in a more familiar tone with the victim.
Once the scammers compromise a senior manager's account, they will try to steal sensitive corporate data. They might also attempt to use scare tactics to pressure employees (like pulling rank) into sending large funds to an account owned by the hacker.
Vishing
Vishing is just phishing - but over the phone. The scammer will use a spoofed ID to make the call to trick the victim into thinking they're getting a call from a trustworthy source.
Usually, they'll pretend to be a bank employee who needs to verify the victim's identity because they saw suspicious activity on their account. They'll normally ask for their login credentials, full credit card number, CVV codes, and PIN codes.
Another scenario involves scammers targeting the elderly, posing as their nephews/nieces or grandkids, and convincing them to wire a large sum of money to their account because they're in trouble and don't want their parents finding out.
Zombie Phish
The name is creepy, and so is the method. A zombie phish involves a hacker taking over an account, and using it to "necro" old conversations - basically, respond to discussions that took place months or years ago.
This method takes people by surprise but also doesn't raise a lot of red flags because the people involved in those conversations will be familiar with the compromised email account. So they'll be more likely to click a shady link or download a malicious attachment.
Clone Phishing
In this scenario, scammers clone a legitimate email that was previously delivered to someone - like a ToS update notification from a bank. However, the hacker will replace all the original content with malicious links and attachments.
Smishing
This is phishing through SMS messages. Scammers will send eye-grabbing messages with aggressive, time-sensitive CTAs to get victims to act fast.
Usually, they will try to trick people into revealing sensitive information like login credentials and credit card details.
Search Engine Phishing
That sounds like hackers would set up their own fake search engine, but that's not really the case.
Instead, they create a fake site and run a paid ad campaign to get it to show up among the first results you see on a search engine (the ads).
Is Pharming the Same as Phishing?
Many people get the two confused and often use them interchangeably. But pharming isn't the same as phishing, just like a MITM attack isn't the same as phishing.
Yes, pharming has the same goal as phishing - to steal sensitive data. And yes, pharming also employs fake sites. But here's the thing - like MITM attacks, pharming is used alongside phishing. Also, phishing can be used to help hackers run a pharming attack.
Feeling confused? No problem - let's take a look at two types of pharming attacks. After that, you'll get a better idea of how it's not the same as phishing.
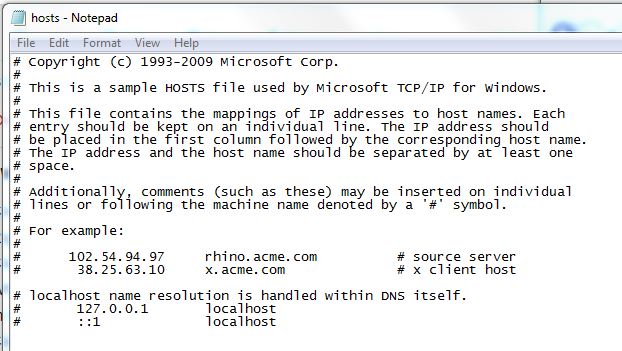
1. Hosts File Pharming
The hosts file is part of your operating system. It's a plain text file on your computer that maps hostnames (website names) to IP addresses. It looks something like this:
In this instance of pharming, hackers modify the hosts file to redirect you to phishing sites. So let's say PayPal's address is 64.4.250.361. They'd change that to the IP address of their fake PayPal site.
Now, whenever you type paypal.com into your browser, you're automatically taken to the phishing site.
And how do scammers get access to your hosts file? Through phishing! They target you with fake emails. If you interact with them, your device will get infected with malware which gives hackers remote access to your PC or automatically modifies your hosts file.
2. Poisoned DNS Servers
In this case, hackers take over a DNS server - usually ISP servers. They target them because they resolve DNS requests. Basically, they're responsible for translating the website names you type in your browser into IP addresses so that you can connect to them.
Once cybercriminals compromise a DNS server, they change its DNS table so that legitimate website domains point to IP addresses belonging to fake sites.
The term "poison" is used because the fake DNS entry can spread to other servers that interact with the compromised DNS server.
Does phishing play any role in this scenario? Of course - pharming aids hackers' phishing attacks by redirecting people to fake sites. Also, hackers can use phishing to compromise DNS servers.
The Bottom Line
Pharming and phishing aren't the same thing. But they go hand in hand:
- Phishing can be used in pharming attacks.
- Pharming is used to redirect people's connection requests to phishing sites.
Does a VPN Protect You from Phishing?
The thing that was on everyone's mind is whether a VPN can keep you safe from phishing.
Well, yes and no.
A VPN isn't exactly designed to offer phishing protection. It can hide your IP address and encrypt your traffic, but it can't do anything to stop phishing emails from landing in your inbox. And it definitely can't prevent your device from getting infected with malware.
However, there are two ways a VPN can offer some protection against phishing attacks:
1. Traffic Encryption
When you use a VPN, all the data that goes between the client on your device and the server is encrypted - including the DNS queries.
That comes in handy when hackers try to use MITM attacks to redirect your traffic to phishing sites - which can actually happen on public WiFi networks where there's no encryption or when you accidentally connect to fake hotspots set up by hackers.
Because VPN encryption makes your traffic surveillance-proof, hackers can't intercept and redirect it anymore. If they try to monitor your data, they won't see connection requests to "paypal.com." Instead, they'll see gibberish like "XBEZGjznYDBsVYLarkcQAw==."
Even if they somehow manage to intercept and redirect your encrypted traffic (highly unlikely) to a PayPal phishing site, you're going to be mighty suspicious when you initially requested a connection to Facebook. So you'll be much, much less likely to interact with it.
Read More: What’s The Deal With VPN Encryption & How Secure This Security Protocol Can Be?
2. Blocklists
Some VPN providers offer advanced features that block connections to phishing sites. So even if a hacker somehow redirects you to one, or you accidentally click a phishing link, the service should stop you from connecting to it.
Here are some examples of these kinds of features:
- CyberSec from NordVPN (Read Review)
- CleanWeb from Surfshark (Read Review)
- R.O.B.E.R.T. from Windscribe (Read Review)
Of course, you shouldn't consider this guaranteed protection from phishing attacks. Some malicious domains can slip by undetected if the blocklist isn't updated fast enough. Also, if you interact with a malicious attachment, the VPN's blocklist can't stop malware from infecting your device.
How to Spot Phishing
The good news is phishing has a lot of red flags that give it away. You just have to pay attention to them. According to our research, these are the most obvious signs you're dealing with phishing attacks:
The Usual Role-Play
As a general rule of thumb, phishers will try to use the following scenarios (or variations of them):
- Offering a deal that's just too good to be true - like you winning thousands of dollars in a contest you never entered, or inheriting a huge fortune from an uncle you never heard of.
- Threatening to shut down your account if you don't follow their instructions. Or saying they noticed suspicious activity on your account, and you need to take action. They usually claim to be someone from your bank, payment processor, or the social media site you use.
- Claiming they're from tech support, and that they need access to your device. Or that you have to download an attachment or click a link to perform a vital update or fix a serious security flaw.
- Saying you're under arrest or under investigation, and claiming to be from your local police department or the FBI/CIA/Interpol/NSA/etc.
Wrong URLs and Email Addresses
Most people would tell you to make sure you're on an HTTPS site. If you're not, it means it's a phishing site.
While some phishing websites are hosted on HTTP, it's not all of them. According to research, a large number of phishing attacks are now hosted on HTTPS. So just checking the SSL badge isn't enough.
Instead, you need to look for mismatched URLs. For example "facebo0k.com" instead of "facebook.com."
Similarly, check the sender's email address. If it's from "paypaI.com" or "[email protected]" it's pretty obvious it's not a legitimate email from PayPal.
Invasive Requests
PayPal will never ask you to verify your account by revealing your password. And no website will need your Social Security Number to validate or restore your account.
Also, your bank will never ask you to confirm a card, account, or transaction by giving out the whole credit card number alongside its CVV code. At most, they'll ask you to confirm the last four digits of your credit card.
Basically, if it feels like the sender is asking for way too much information, it's because they are.
Poor Spelling and Grammar
Scammers only pay very close attention to this when they focus on large targets like a shareholder or a CEO. When they target large numbers of people, they get sloppy. And it shows.
Phishing messages will generally contain obvious spelling mistakes, grammatical errors, and just downright weird phrasing - the kinds you wouldn't see in a legitimate message.
Stuff like "we have assigned your account with a temporary limited," "we need more informations from you," or "activate you're acount" means you're very likely dealing with a phishing attack.
An Aggressive and Urgent Tone
Phishers will almost always try to get an immediate reaction out of you. They will often use an aggressive writing or talking style and be very pushy so that you don't have time to think before making a decision.
Phishing attacks also employ urgent language and intense FOMO (Fear of Missing Out) to add more pressure on you.
You should already know this by now, but a regular email message or phone call from a legitimate organization, company, or government agency doesn't use such a tone at all.
Generic Greetings
It goes without saying that an email from your bank or PayPal won't start with "Dear Customer," "Dear User," or "Dear Guest." That just feels robotic and random. Legit messages address you by your full name or the alias you used when signing up.
Also, if they do use your name, make sure it's capitalized right. Sometimes, phishers forget to do that to the middle name ("Bob john Smith" instead of "Bob John Smith").
Shortened Links
When phishers use malicious links, they hide them with services like Bitly to shorten them so that they don't look so weird.
For example, instead of "paypaI.com/user/login/password" you'd see something like "https://bit.ly/2Lv60it."
And a very shady link that would normally raise questions like this "http://ppal.org/das24-43adas-31231/4324f" would look like this "https://bit.ly/3628KgJ."
Weird Attachments
No, a file called "COVID-19 Health Guidelines" that has a .exe or .bat extension isn't a document from your local government. It's a malicious executable that's just waiting for one double-click to infect your device.
Generally, if you see a file that has a mismatched extension, it's very likely malicious.
Cryptocurrency Payments
Phishers love requesting cryptocurrency payments because they're much, much harder to track than wire transfers.
If you see someone claiming they're from your bank, PayPal, the FBI, or the WHO, and saying you can make donations or pay fines in Bitcoin (or any other altcoin), it's a scam.
How to Protect Yourself from Phishing
We already said you could use a VPN for some level of protection, but you can't rely on it alone. Alongside using a VPN, you also have to:
Get Antivirus Protection
Phishing attacks usually rely on malware to get access to your device and data. So antivirus software (Click here to get the Best Free Antivirus) is realistically the best way to stay safe if you accidentally click a phishing link or download a malicious attachment. It will automatically quarantine the infection and stop it from doing any damage.
Also, most antivirus tools have a blocklist of shady domains. So they can block your connections to potential phishing websites. Pair that with a VPN with a similar blocklist, and you'll improve your odds of staying safe.
Just make sure you keep the software on at all times. Also, never skip an update. Otherwise, new strains of malware might slip through.
Use Password Managers
A password manager is an online tool that encrypts all your passwords, keeping them safe in one place. Their highlight is the auto-fill feature, which automatically fills in login fields with your credentials on designated websites.
In theory, if you end up on a phishing site, the password manager shouldn't fill in the login fields. What's more, some of them will even warn you that you're on a shady website.
Related: Find Out the Best Password Managers Here
Enable 2FA/MFA on All Accounts
2FA (Two-Factor Authentication) and MFA (Multi-Factor Authentication) won't stop a phishing attack - but they can prevent phishers from taking over your accounts.
Both 2FA and MFA add an extra step in the login process. After you type in your username and password, you usually need to type in a randomly generated code you get through an app on your phone or a text message.
So, if you somehow fall for a phishing scam, a hacker won't be able to compromise your account without also having access to your phone.
Just make sure you set the 2FA/MFA option on your phone, not an email account. It's easier for phishers to compromise the second one. And if the platforms you're using don't have 2FA/MFA, we recommend switching to sites that do. The risk is simply not worth it.
Use Anti-Phishing Extensions & Script Blockers
Extensions like PhishDetector, NetCraft, and MetaCert are great ways to stay safe, but we prefer using Stanford's Anti-Phishing Browser Extensions. They have four awesome tools that:
- Detect phishing sites and warn you about them.
- Secure your browser cache from context-aware phishing attacks.
- Secure visited links from context-aware phishing attacks.
- Generate phishing-resistant passwords.
Script blockers like uMatrix and uBlock Origin also come in handy. While they don't directly protect you from phishing, they can prevent malicious scripts from loading on sites.
So, for example, a script blocker could stop a phishing pop-up from starting up on a legitimate website. They could also prevent crypto-mining scripts from loading. Or they can prevent a login field on a phishing site from properly displaying or working.
Don't Click Links (Hover Instead)
Your first instinct when you get an email (especially one you didn't expect) shouldn't be to click on the links or CTA buttons you see. Instead, you should access the site directly.
For instance, if you get a message from your bank with a login link, head to their website instead, and log in securely there.
But if you really, really need to use the link in the email, mouse over it first. It should reveal the real URL destination.
An anchor text in a PayPal phishing email might say "click here to log in," but if you hover over it, you might see an address like "http://www.p4ipaI.org/site/login/password." Obviously not somewhere you'd want to end up.
Other Tips
- Always be suspicious of emails or phones you weren't expecting. If you don't recognize the sender or the number, don't answer and consider blocking the sender's address/number.
- If you run a business, reserve some time to train your employees to handle phishing. Maybe book a workshop for them or put together a PDF presentation that they can all easily follow.
- Also, as a business, consider getting an SDP (Software-Defined Perimeter) for remote connections. It can actually protect your network from phishing attacks by refusing connections from compromised devices. Our personal favorite is Perimeter 81.
- Try not to share too much private information about you on social media - or, at the very least, make your profiles private. Those are the kinds of details phishers can use to create personalized messages.
- Don't download attachments if you don't have your antivirus software running.
- Google search parts of the email between quotes. You might find Reddit or Facebook posts where people are calling that message a scam.
- And finally - if it sounds too good to be true, it's because it is.
What to Do If You're Dealing With Phishing
Your first reaction should be to ignore the message, delete it, and block the sender's address. If you're on the fence about doing that, research the sender - Who are they? Is their business legitimate? Is the name they're using real?
Google the names used in the emails to see what you find. If you suspect someone is impersonating someone from your bank, call them to see what they have to say about this.
And if the phisher starts getting aggressive and threatens you, don't be afraid to contact the police.
What if you're dealing with vishing?
Well, if your gut is telling you something is off, just hang up. Alternatively, ask the caller for detailed information about who they are, their business, where you can find them, etc. If they become annoyed or change the subject, it's a scam.
And obviously, block the number. If they start calling you from other numbers, change your own number and consider getting the police involved.
How to Report Phishing
Most email services will let you report phishing messages with a few clicks. For instance, with Gmail, you just need to hit the three-dot button next to the reply option and choose "Report phishing."
Also, if you found a phishing site, you can report it to Google right here.
Here are other things you can do:
- Report the scam to the FTC.
- Forward the email to [email protected].
- Forward phishing text messages to SPAM (7726).
- Report the attempt to Scamwatch.
- Check out this long list of ways to report Google scams.
- File a complaint with the IC3 (FBI).
- Use the numbers on this page to report different types of scams.
You should also check the laws in your country to see what other options you have. You can start by googling "[country name] + report phishing."
What to Do If You Interacted With Phishing Emails
If you're worried that a phisher got their hands on your data, follow the guidelines from IdentityTheft.gov. They have instructions for specific scenarios.
If you're not from the US, you should contact the police ASAP. They should tell you what to do next.
You should also contact your bank. Tell them to cancel your credit cards and cancel any new transactions that show up on your account.
Besides that, you need to run an antivirus scan of your device to remove any potential malware infections. If you're dealing with ransomware, try this link to see if there's anything you can do.
Finally, reset all your passwords and usernames - or at least the ones on accounts that are very valuable to you. Also, consider setting up a new email and linking all your accounts to it.
It's a lot of hassle, yes, but nobody said being the victim of a phishing attack was going to be easy.
What's Your Experience With Phishing?
Did you receive any shady messages or calls? Who was the phisher claiming to represent? Also, what measures do you usually take to avoid phishing attacks? Oh, and what other wacky phishing scenarios have you heard of?
Go ahead and let us know in the comments or on social media.