‘WeSteal’ Commodity Malware Is Hot Among Crypto-Grabbers
- A known malware author with previous success in cybercrime has returned with a crypto-stealer.
- Called ‘WeSteal,’ it is a commodity malware tool that can evade AV detection and steal people’s Bitcoin or Ethereum.
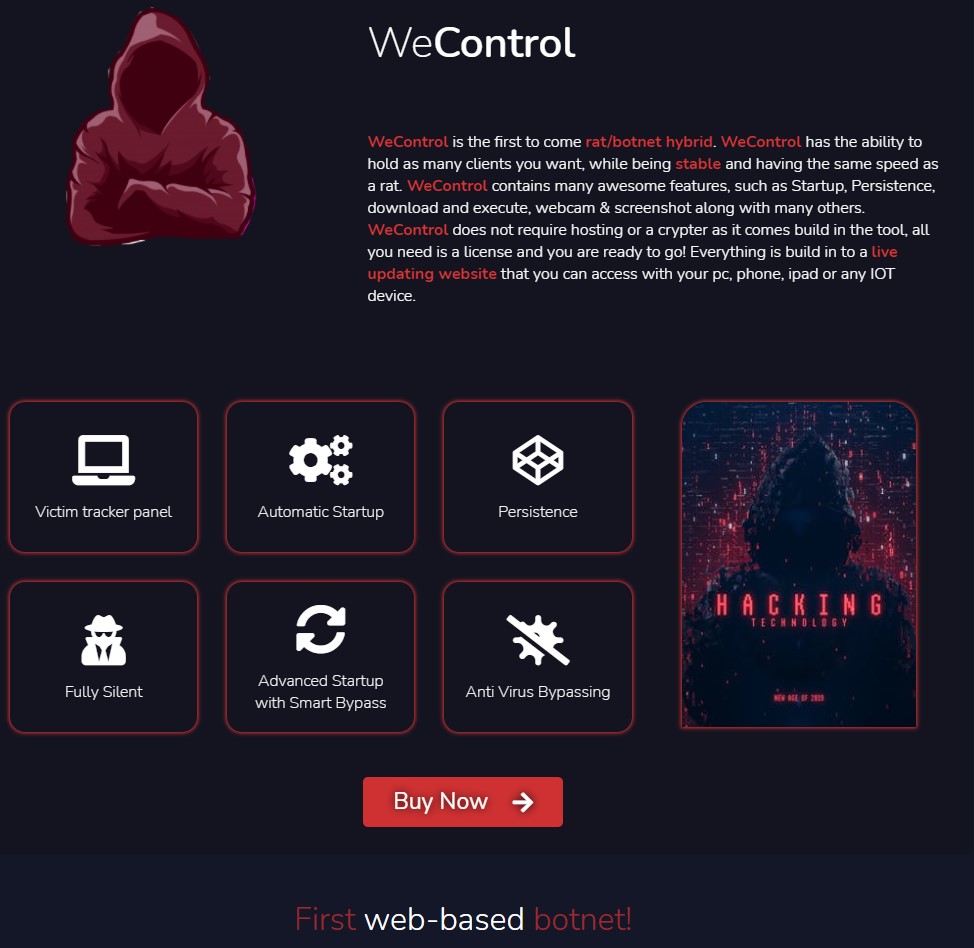
- There’s also a RAT for sale called ‘WeControl,’ featuring persistence, smart startup, and a zero-day for stealthiness.
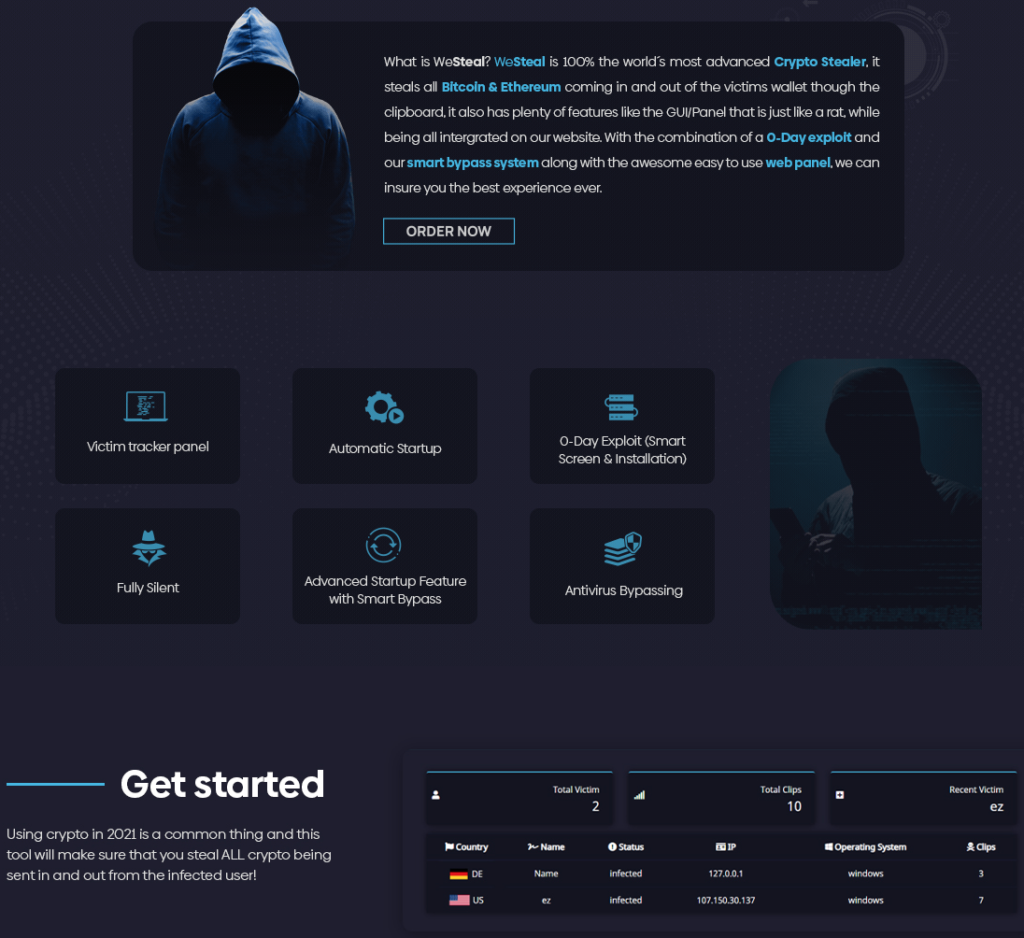
There’s a new and rising commodity malware created specifically to help crooks steal other people’s cryptocurrency called ‘WeSteal.’ Judging by the name as well as the promotional material used by the authors of ‘WeSteal,’ there’s no intention to hide what this is about, or maybe to pretend that this is some form of a pentesting tool that could be abused or whatever. It’s a crypto snatcher sold primarily for stealing crypto, charging €20/month, €50 for three months, and €125 for one year.
The seller goes by the name “ComplexCodes” and has been promoting ‘WeSteal’ since February 2021, taking advantage of the spike in crypto value prices that generated mind-boggling interest in the community. Together with this tool, there’s a commodity remote access tool (RAT) having the matching ‘WeControl’ name. According to a report from the Unit42 team, the same author, who seems to be an Italian person, previously sold the tools known as “Spartan Crypter” and “Zodiac Crypto Stealer.”
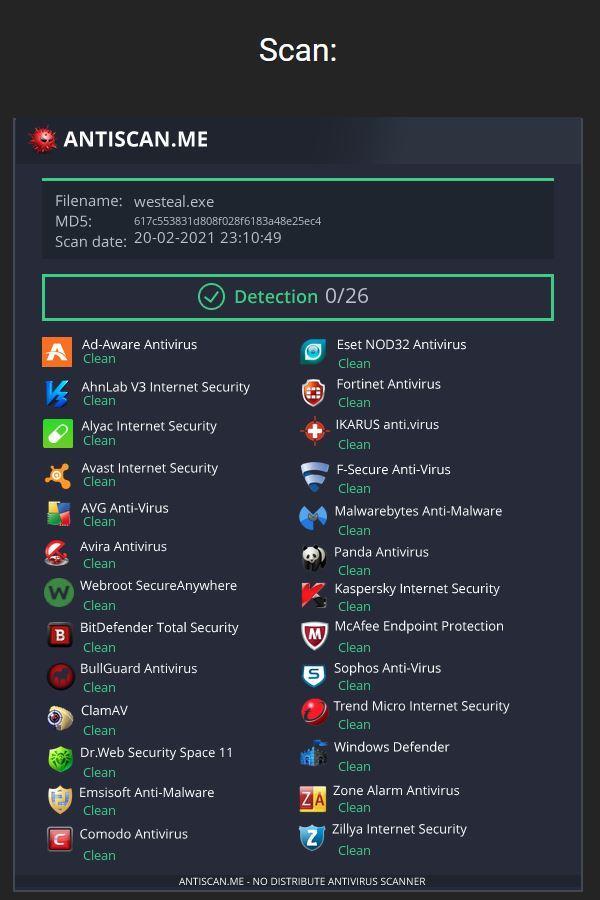
An impressive aspect of WeSteal’s capabilities is its AV detection results. It appears that no AV engine is capable of catching the threat by scanning the executable, so malicious actors can buy and use it without having to think about unexpected obstacles in their operation. To achieve this, ComplexCodes has used the PyArmor source code obfuscator, which uses AES GCM for runtime decryption when the time comes.
Upon deployment, WeSteal monitors the clipboard for strings that match Bitcoin and Ethereum wallets. When something like that appears, the malware replaces the copied wallet ID with one that the actor controls, so the transaction amount is diverted in their pocket. This is the same trick that we saw in ‘HackBoss’ and is generally a widely deployed method as it’s practically non-risky and effective.
The ‘WeControl’ RAT is a more recent release, appearing for the first time in the wild only a couple of weeks ago, so Unit42 hasn’t had the time to analyze it thoroughly yet. It seems to feature the same PyArmor obfuscation, so it should be equally capable of evading AV detection.
The promotional page makes claims about persistence, advanced startup with “smart bypass,” automatic startup, victim tracking panel, stealthiness, etc. The author claims to have incorporated some form of a zero-day exploit in the product, but any details about that are omitted.
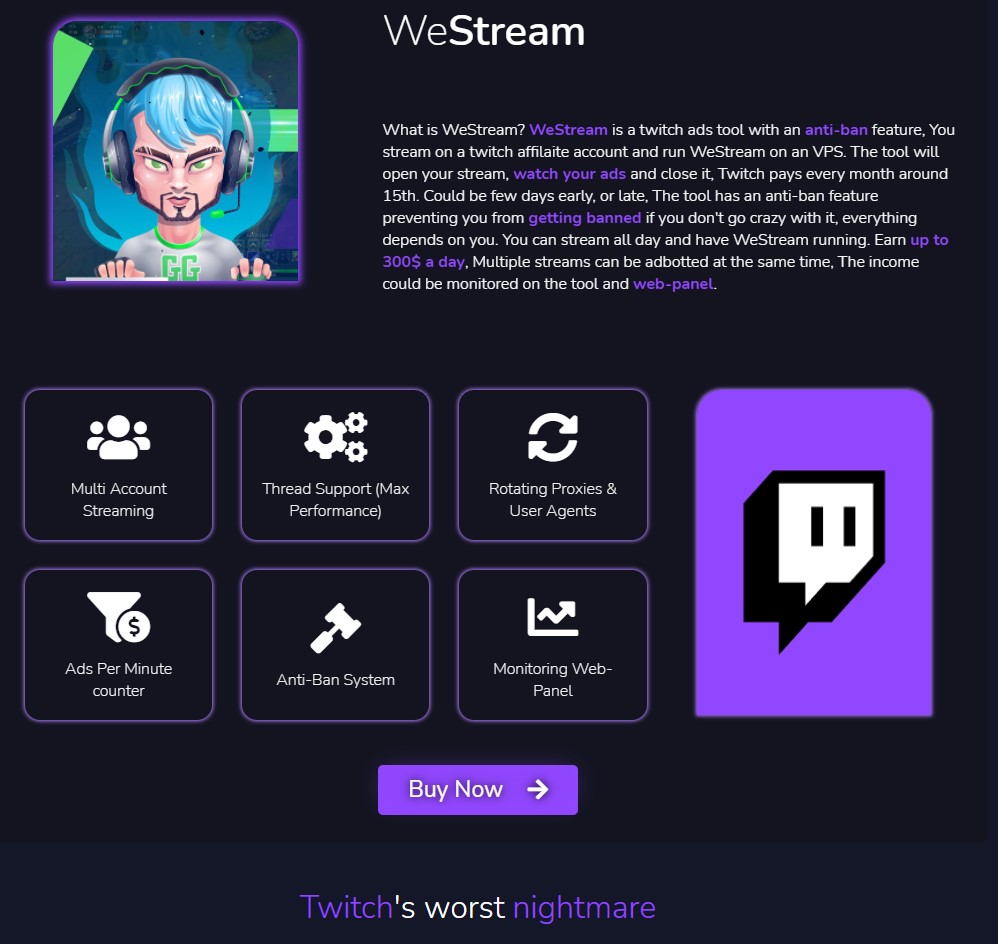
In addition to what is on the Unit42 report, we saw a third tool that is available for purchase by ComplexCodes called 'WeStream' and characterized as "Twitch's worst nightmare." This appears to be an ad tool with an anti-bad feature that generates Twitch ad revenue automatically to help streamers make up to $300 a day, allegedly.