The Warzone RAT Service is Getting More Popular Among Cybercriminals
- The Warzone RAT is a powerful MaaS that is getting very popular thanks to its rich set of features.
- The developers of the malware are offering various plans, both for the exploit and for the crypter.
- The Warzone RAT is a problem for Windows installations, where it can be a silent and persistent threat.
The Warzone RAT (Remote Access Tool) is in the spotlight of Check Point researcher Yaroslav Harakhavik. These "grab and deploy" malware-as-a-service (MaaS) tools are getting more popular among cyber-crooks, and those who create and sell them are making more money than ever before. This gives them the resources to create more user-friendly, powerful, and sophisticated tools so its a positive feedback loop for the whole exploitation industry. The Warzone RAT is a characteristic example of the existing MaaS market and the current situation in the field. It appeared for the first time in autumn 2018, and it has gone a long way since then.
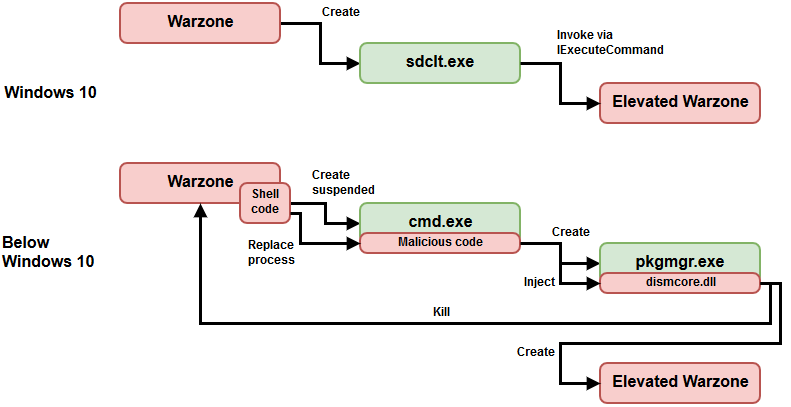
The Warzone is written in C++ and it is compatible with all versions of Windows. It is supported by a dynamic DNS service so as to remain unaffected by IP address changes. It can plant itself in the Windows startup list, bypass the UAC (User Account Control), and disarm the Windows Defender protection. Of course, there are many different versions of the Warzone RAT, so its specific capabilities can change depending on the version.
Source: Checkpoint
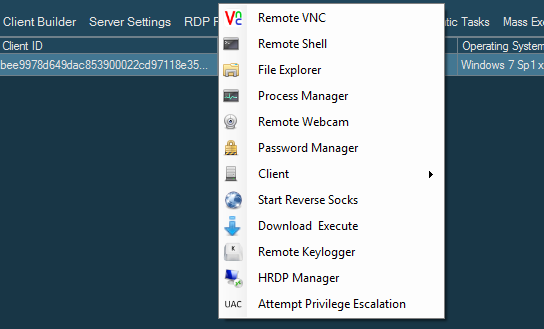
The main features, that are generally present on all versions, are the following:
- Remote desktop via VNC (Virtual Network Computing);
- Hidden remote desktop via RDPWrap;
- Wide range of privilege escalation even for up-to-date Windows 10 installations;
- Remote WebCam control;
- Password grabber that works on Chrome, Firefox, IE, Edge, Outlook, Thunderbird, and Foxmail;
- File fetching and execution;
- Live keylogger;
- Offline keylogger;
- Remote shell;
- Dedicated file manager;
- Process manager;
- Reverse proxy.
All of the above features are achieved without the need to use .NET.
Source: Checkpoint
The Warzone RAT is advertised via various online groups and forums, and on dedicated websites as well. The researcher has noted warzone[.]io and warzone [.]pw, but the domains are constantly updated. The malware author is offering various ways of communication too, using email, XMPP, Skype, and Discord.
As for the tiers offered for aspiring hackers, there’s a "Starter" pack that costs $22.95 and gives unlimited access for a month, a "Professional" plan that extends the access to three months and includes customer support and premium DDN, costing $49.95. Finally, there’s the top-tier "Warzone RAT-Poison" which carries the hefty price tag of $489. Via this last one, users get the RAT for six months, plus a rootkit, plus hidden files, hidden startup, and hidden processes.