WannaCry Ransomware is Still Out There in Thousands of Infected Systems
- WannaCry is still alive, pinging the kill-switch domain by the thousands every week.
- Kryptos Logic remains the company that contains and monitors the malware, warning the IT world that the ransomware is still alive and well.
- More versions have been spewed by non-original authors, requiring the registering of more domains, so a rich collection of kill-switches is now up.
Almost eighteen months after the WannaCry ransomware infected the first systems, researchers say the malware is still out there in many thousands of computers, staying dormant until the situation changes again. Where situation, enter the domain registration that acted as a kill switch for the malware.
For a reminder, WannaCry was programmed to check the registration of the domain that goes as “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com”. If this domain was registered, the ransomware would stop the files encryption process and seize its self-spreading action. A team of security researchers (Kryptos Logic) analyzed the source code of the malware and then registered the domain, essentially deactivating the ransomware that caused major problems in multiple organizations, including the Russian Interior Ministry, the Chinese Universities, Telefonica, and a lot more.
The ransomware was simply deactivated, and it kept checking the aforementioned domain so as to decide whether it should reactivate itself or not. Eighteen months after these events, anti-malware software developers had enough time to update their databases and essentially enable their tools to remove the WanaCry and all of its cryptor and decryptor modules. As reported by Kryptos Logic, however, there are still thousands of systems out there that still connect to the “kill-switch” domain. The team decided to host the domain to Cloudflare in order to ensure high availability and adequate protection against DDoS attacks which would essentially reactivate WannaCry.
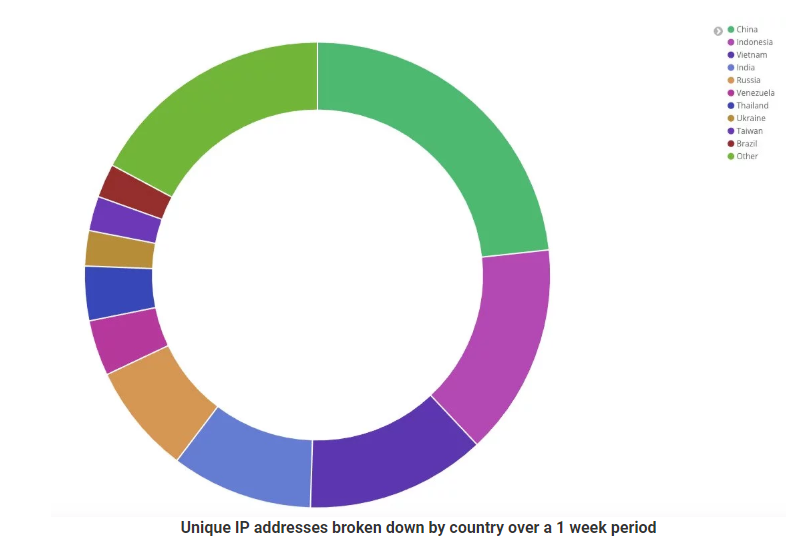
According to Jamie Hankings, the Head of Security and Threat Intelligence Research at Kryptos Logic, the number of connections to the kill switch domain reaches 630 thousand of unique IP addresses that come from 194 countries, each week. The most “infected countries” are China, Indonesia, Vietnam, India, and Russia. Should the ransomware get activated again, it would spread like wildfire around the globe, as the kill switch domain is the only thing that is keeping it from doing so right now. Kryptos Logic is suggesting that organizations use their “TellTale” service that can monitor a range of IP addresses and inform of their infection status so further action can be taken.
From the Kryptos Logic Data
While the original author of the malware hasn’t released an update of WannaCry that has a different kill-switch domain, or no kill-switch at all, others have done so either accidentally or intentionally, so there’s now a comprehensive list of kill-switch domains that is keeping everything inactive. Should the original author decide to relaunch the malware without a kill-switch, which should be trivial really, the infection rates could get much worse.
Are you using any anti-malware solutions in your system? Let us know in the comments below, and don’t forget to like and subscribe on our socials on Facebook and Twitter.