WannaCry is Still Haunting IT Administrators as New Variants Pop Up
- New WannaCry iterations pop up all the time, targeting systems from all around the world.
- Researchers have detected over 12000 different versions and counted millions of infection attempts in August.
- The problem is intensifying, as IT administrators still choose not to apply system patches after two years.
Two years after the WannaCry malware spread like wildfire over the world, IT admins still have to deal with the menace and fight against new variants. As we warned back in December 2018, there are still thousands of systems that are pinging the kill-switch domain that was set up by Marcus Hutchins. With that original version having been subdued, malicious actors turned to the creation of other versions with different kill-switch domains, or no kill-switch at all. As Sophos claims on their most recent report, there are 12000 variants of WannaCry in circulation right now.
Source: news.sophos.com
The particular security company alone has detected and blocked more than 4.3 million attempts to spread a variant of WannaCry to a protected endpoint, only in August 2019. The majority of the WannaCry variants that Sophos analyzed are broken in some way, so they are incapable of encrypting the files of their victims. They are still able to propagate on networks that constitute of unpatched Windows machines though, and this is still a security problem.
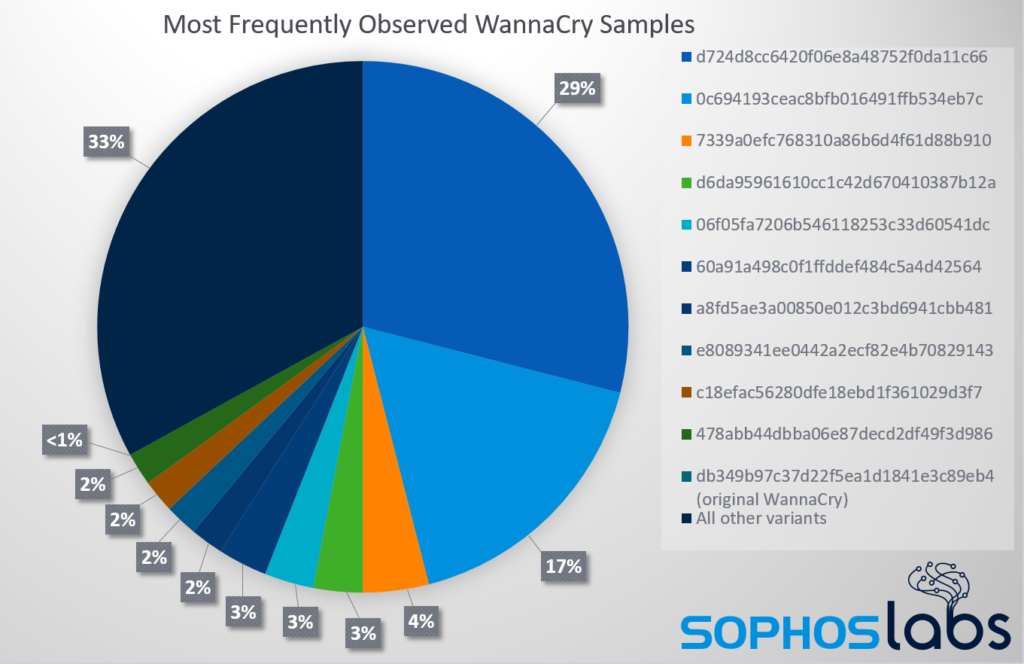
Sophos has compiled some interesting data about WannaCry variants that they monitored between September 2018 and December 2018, and here are the highlights:
- All of the variants analyzed contained some form of a bypass for the kill switch code.
- 66.7% of detections concerned ten WannaCry iterations, while the top three accounted for 50.1% of detections.
- The original WannaCry was only seen in 40 instances, which is probably security researcher activity.
Source: news.sophos.com
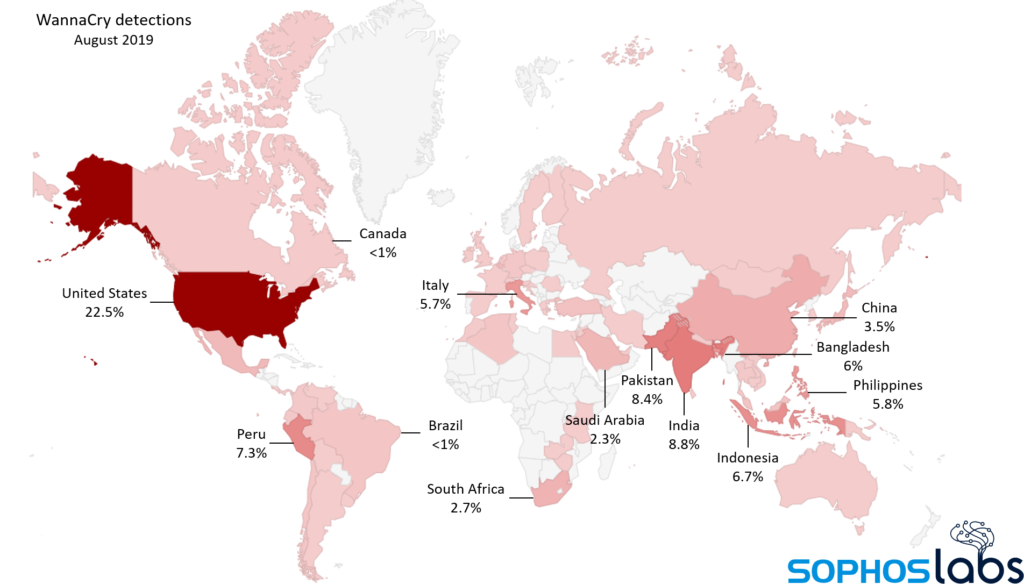
As for the current situation, most samples target systems that are based in the United States (22.5%), followed by India (8.8%), Pakistan (8.4%), Peru (7.3%), and Indonesia (6.7%). In general, the targeting is global, and the actors are multiple.
Once again, the only thing that makes the above situation possible is the fact that system administrators don’t want, or choose not to update their Windows systems. There are multiple reasons to follow that risky path, with the main being the introduction of incompatibilities with 3rd party software that these systems are expected to run unproblematically. Keeping those systems online, however, is giving WannaCry actors a reason to continue their effort to create a powerful enough iteration of the malware. The rise in this activity is characteristic right now, and those who haven’t patched their Windows systems for two years now have a lot to worry about, besides WannaCry.
Have something to comment on the above? Feel free to do so in the section down below, or on our socials, on Facebook and Twitter.