Vulnerable Fortigate VPN Servers Now Targeted by the ‘Cring’ Ransomware
- Unpatched Fortigate VPN servers have one more trouble to deal with, called ‘Cring.’
- This is a new RSA-encryption ransomware strain that is being actively developed by its authors.
- The actors are demanding the payment of 2 Bitcoin from the victims for the decryption key.
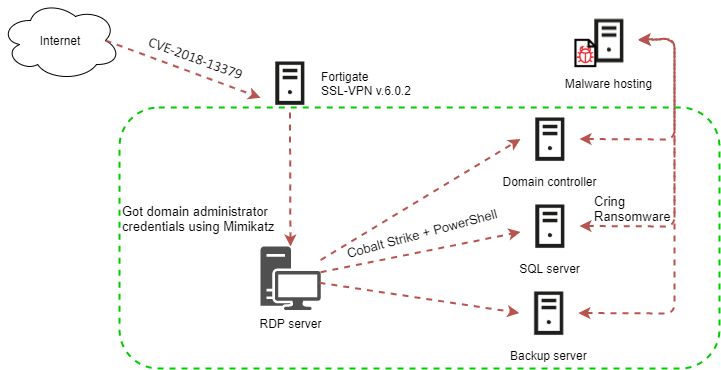
Yet another attack vector has been added in the galore that concerns vulnerable Fortigate VPN servers, one of the most targeted VPN products of the past year. As detailed in a report by Kaspersky, actors are scanning for unpatched Fortigate VPN products or even buy IP address lists compiled by others.
Next, they are establishing presence and attempt to steal credentials by using the Mimikatz utility. This is followed by planting Cobalt Strike to aid in compromising the admin account and enabling the actors to move laterally on the compromised network. Eventually, when all valuables have been exfiltrated, and the reconnaissance operation is over, the actors run a new ransomware strain called ‘Cring’ to encrypt everything.
The PowerShell responsible for the decryption of the fetched payload is named “kaspersky,” so the popular security firm is being impersonated here by the actors hoping this will mask their payload's malicious nature. According to the researchers, the Cring ransomware is currently under active development, as they were able to source multiple samples of increasingly newer versions within a short period of time.
Cring stops all Microsoft SQL server operations to encrypt database files successfully and also terminates the Veritas NetBackup process to ensure that no backup copies will be taken and that those present will be wiped. The SstpSvc service is terminated, too, possibly to stop members of the cyber-incident response team from connecting to the infected system remotely via VPN, potentially disrupting the encryption process.
Upon the successful encryption of the 23 file formats supported by Cring, the victim gets a ransom note which requests the payment of 2 Bitcoin. In today’s exchange rate, that would be about $113,300. As usual, the actors are warning the victim that the decryption key will not be kept by them for long (no deadline is given though), urging them to contact a Tutanota email address as soon as possible.
All that said, the best way to protect your systems (and your job) from all this trouble is by patching the Fortigate VPN product. The actors are still exploiting CVE-2018-13379 to get started with the particular attack workflow, so this is still the entrance point.
For those who still haven’t patched even after all this time and the numerous warnings to do so, there must be a good reason for still choosing to show up on those scans. If you happen to be in this category, at least make sure to restrict VPN access between facilities, close all ports that aren’t used, store multiple backups offline or on separated servers, and keep your security solutions and OS up to date.