Voxox Data Leak Exposes Over 26 Million Text Messages
- Voxox, formerly known as Telcentris has suffered a massive data breach exposing text messages with two-factor codes and password reset links.
- The affected server was not protected with a password, allowing anyone to snoop in.
- The database has already been taken down to prevent unauthorized access.
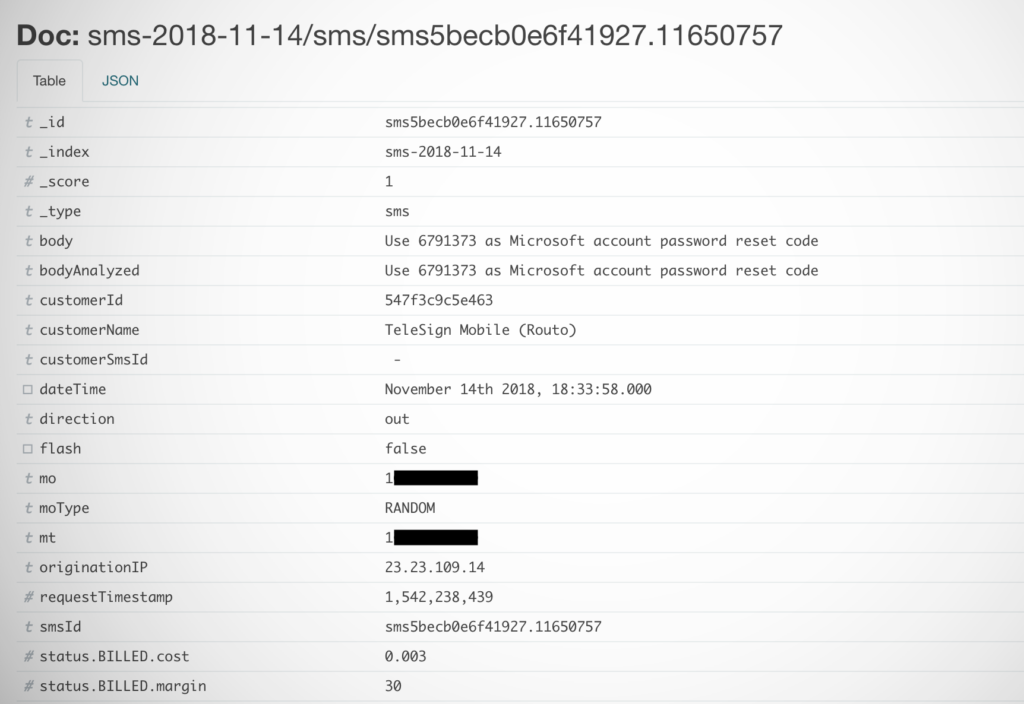
While a number of security incidents all over the world are attributed to security flaws, bugs or even cybercriminals breaking into server databases, in some cases, it is simply a lack of any protection that leads to leaks. Voxox is a communications company based in San Diego, California that had a database containing over 26 million text messages available to public access without a password.
The security flaw was discovered by Berlin-based security researcher Sébastien Kaul. The database was configured with Kibana’s front-end system and running Elasticsearch by Amazon, which made the Voxox data easily accessible to anyone. You simply needed to put in names, cell numbers or partial content in text messages to be able to search through the entire database.
Image Courtesy of TechCrunch
Voxox’s co-founder and chief technology officer Kevin Hertz revealed the company is currently looking into the matter and is abiding by the standard data breach policy. The impact of the data leak is yet to be assessed fully, and an official report may be released soon.
Voxox’s primary function as a communications company was to act as a gateway for converting shortcode to text messages and deliver them to users’ phones and tablets. After the company was notified about the breach, the database was immediately taken down. Even though it is estimated that 26 million text messages were available on the database, the visual front-end suggests that the number may be even higher.
Fortunately, most of the data in text messages is for temporary use as one-time passwords and password reset links have no value after they have been used. Even if they have not been used, there are timers set by services to make them invalid if not accessed.
SMS based two-factor authentication is slowly fading away and being replaced by app-based verification systems which are much more secure. To secure your data, you should adopt password managers, app-based authentication or hardware U2F keys to prevent such data leaks.
What do you think about the data leak suffered by Voxox? Let us know in the comments below. And also, don’t forget to follow us on Facebook and Twitter. Thanks!