ViperSoftX Data-Stealing Malware Distributed Under the Guise of eBooks Torrents
- ViperSoftX, which uses torrents as its main distribution channel, was now seen hiding in malicious eBooks.
- The files in the torrent link appear to be legitimate but secretly include the data-stealing malware.
- The same cunning infection is distributed via cracked software, pirated apps, and more.
The ViperSoftX malware is now being spread via apparently legitimate eBooks on torrent websites, but it is no stranger to this distribution method since it hides in functional pirated software. This highly sophisticated malware can exfiltrate sensitive information from Windows machines while remaining undetected. ViperSoftX can also automate the execution of multiple commands without direct user interaction.
Attackers leverage existing scripts rather than building new code. They adapt components of offensive security scripts, selectively modifying only the necessary elements, which leaves space for improving their evasion tactics.
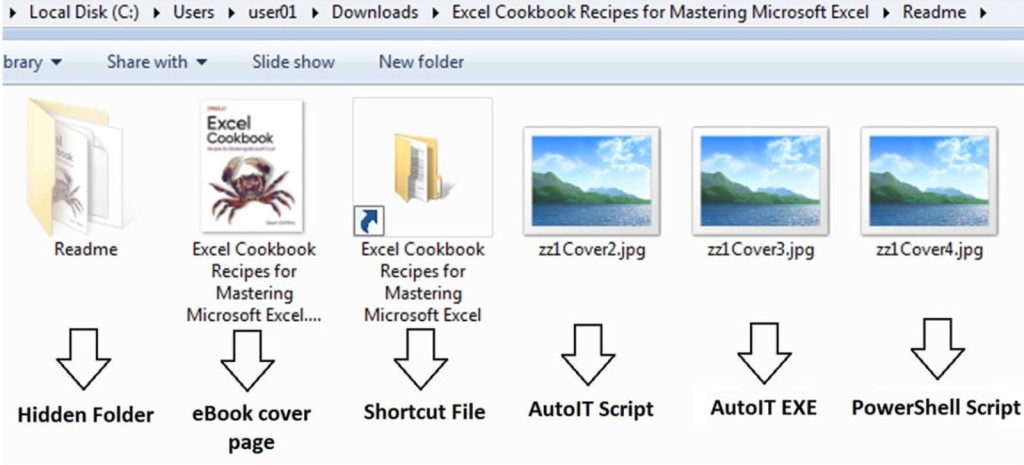
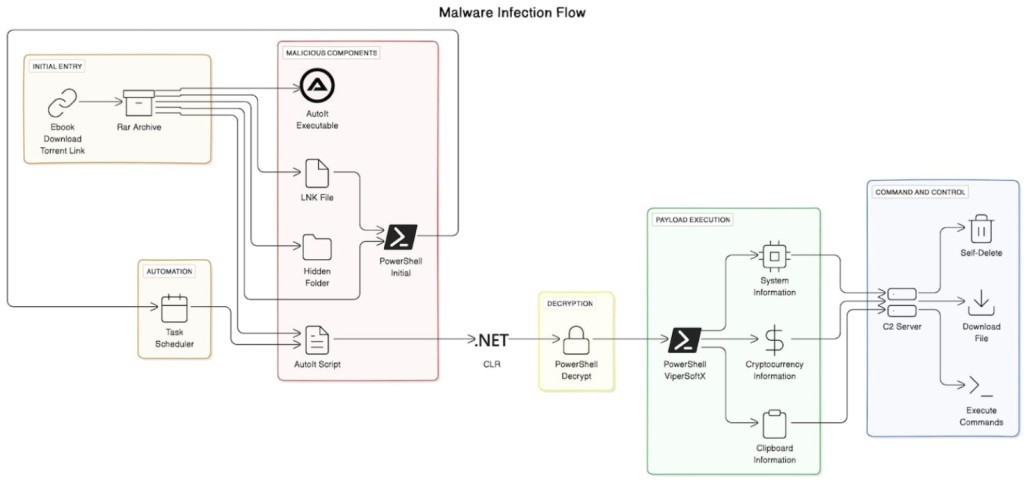
The malware lurks in what may seem like a harmless eBook in a torrent link. Besides the PDF or eBook document, the RAR file the user downloads includes a hidden folder, a shortcut file, and JPG files that are actually a PowerShell script and the AutoIT script and executable.
Executing the shortcut file initiates a command sequence. The PowerShell code is hidden within blank spaces, and the AutoIT scripts hide the cybercriminals’ malicious actions, who carefully obfuscate these scripts to avoid detection.
The current variant of ViperSoftX uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands within the weaponized AutoIT, seamlessly integrating PowerShell functionality and tricking detection tools.
AutoIT does not by default support the .NET CLR framework, but its user-defined functions (UDF) offer a gateway to its library, and threat actors can use AutoIT to secretly execute PowerShell commands via Automation Classes that can interact with PowerShell modules, cmdlets, and scripts within an unmanaged runspace.
ViperSoftX uses a function that patches the Windows Antimalware Scan Interface (AMSI), neutralizing it before the malware starts executing PowerShell scripts. This prevents it from being detected by security solutions that depend on AMSI.
ViperSoftX was first detected in 2020, and with each new version, it showed increased complexity and advanced capabilities, becoming a formidable threat.