VeryMal Malvertising Campaign Can Bypass Scanners on Mac OS
- A new malicious ad campaign has been discovered that is capable of triggering as many as 5 million times a day.
- The ad is hidden in JavaScript code and does not trigger anti-malware scanners.
- The ‘VeryMal’ malware was first discovered by security firm Confiant.
Security firm Confiant released a report that details a new malware that is capable of triggering advertisements on Mac OS systems. Dubbed VeryMal, the malvertising campaign cleverly hides so well that anti-malware software is not even capable of spotting it. The most common method of spreading malware is code obfuscation, but most malware scanners have adapted to the method which led to the developers of VeryMal using the steganography method.
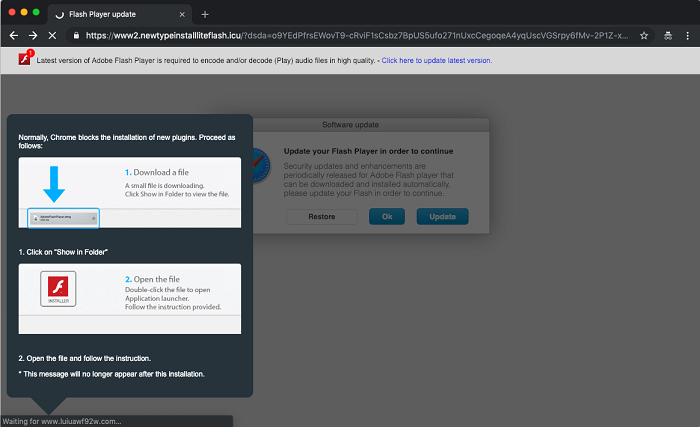
Image Courtesy of Confiant
The VeryMal malware’s advertising domain veryield-malyst.com managed to trigger image-based ads as many as 5 million times between January 11 and January 13. The images contain JavaScript code with links to a malware embedded in them. If visitors head to the malicious link on the ads, they can unknowingly allow a trojan payload to be injected on to their systems. The malware’s advertising campaigns tell internet users that their Flash Player is out of date and redirects them to a malicious download page that hosts the malware itself. Similar ad-campaigns have become popular on the internet, and it is up to users to be careful about their online activity.
VeryMal is far more effective at hiding itself compared to generic code obfuscation methods, and it uses a method known as “steganography” not to get detected. According to Confiant researcher Eliya Stein “The output of common JavaScript obfuscators is a very particular type of gibberish that can easily be recognized by the naked eye. Techniques like steganography are useful for smuggling payloads without relying on hex encoded strings or bulky lookup tables.”
The most effective way to avoid campaigns like VeryMal is to use ad-blocking software like browser extensions of dedicated desktop apps. Some browsers have started offering built-in ad-blocking features which you may want to look at. Malvertising has been on the rise in recent times with advertisers losing an estimated $1.13 billion due to internet users using ad-blockers.
What do you think about the VeryMal malvertising campaign? Let us know in the comments below. Come chat with us on Facebook and Twitter.