Verizon Introduces “Number Lock” for Protection Against SIM Swapping
- Verizon is taking an important step to protect subscribers against SIM swapping scammers.
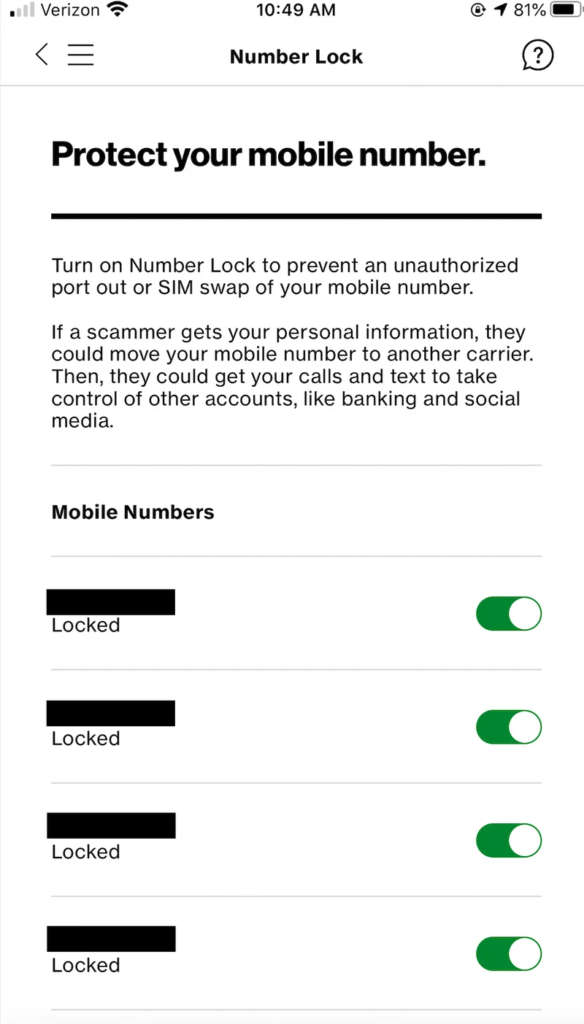
- The telco introduced a number lock feature on its mobile app, preventing agents from performing ports.
- There is still a way to override the user’s setting, but it’s not as easy or simple as it was before.
SIM swapping or “SIMjacking” is a nasty type of a phone number takeover attack that is done for purposes of bypassing the SMS-based two-factor authentication step that is protecting an account. Fraudsters are calling the target’s telecom provider and try to trick the agent into porting the requested number to their SIM card, presenting some stolen identification details to convince them of their identity. In some cases, they collaborate with the agent who is knowingly engaging in the illegal act, and receives a generous reward from the scammers. Verizon has recently introduced a new feature that will hopefully make SIM swaps harder, calling it “Number Lock”.
https://twitter.com/verizon/status/1275127270152306688
Telecom providers have been offering half-baked solutions to their customers thus far, so seeing something like “Number Lock” is very important, even though it isn’t absolutely perfect or safe. The feature is available through the Verizon mobile application, allowing the users to just switch the slider to the “locked” position for the phone number they want. Even if a scammer calls the Verizon customer support service and asks for a number port, and even if the representative is bribed and willing to do it, the user’s setting will stop the process as there’s no way to override it. Or is there?
Source: Motherboard
All mobile apps and online services have a back-end, and there are always users (telco employees) who have access to that back-end's dashboard. So, the scammers would just have to bribe someone who is working on a higher level, and they could change the target's setting to the “unlocked” position. Of course, this is not as simple as it sounds, and companies keep login logs for back-end access, etc. Even then, someone could use stolen credentials to perform the trick. Remember, SIM swappers are going after big money like crypto wallets that hold millions of USD, so the motive for everyone involved is strong.
We cannot deny that Verizon has just made a move in the right direction, but using SMS-based 2FA should still be considered relatively unsafe. If you have valuable online accounts, protect them with an authenticating USB stick, or use an authenticator app instead. If you have no other option than to receive one-time-passwords via SMS, use a phone number that nobody else knows and don’t share it online for any reason. If hackers don’t know which number to target, they have no way of porting anything onto their blank cards.
Read More:
- Nine SIM Swappers Arrested and Charged With Fraud in the US
- SIM Swapper Sentenced to 10 Years in Prison After Stealing $5 Million
- AT&T Faces $1.8 Million Lawsuit for Not Doing Enough Against SIM Swapping