Vehicle Manufacturers Struggle With Poor Car Keys Encryption
- Researchers managed to reverse engineer the way immobilizers in cars communicate with key fobs.
- What they found was that some manufacturers inexplicably downgrade the intrinsic security of the system.
- Thus, they were able to create cloned keys that work exactly like the original ones for Toyota, Kia, and Hyundai.
As reported by a team of researchers from KU Leuven and the University of Birmingham, the “DST80” vehicle immobilizer systems used by Tesla, Toyota, Kia, and Hyundai are very easy to crack. The immobilizer is an anti-theft system that locks the ignition of the vehicle to prevent hot-wiring. When the original car key is in range or is slotted into the wheel column cylinder, a cryptographic key stored in its transponder unlocks the immobilizer and the ignition system is freed to start the engine. The DST80 system uses an 80-bit cryptographic key to encrypt a 40-bit challenge generated by the reader.
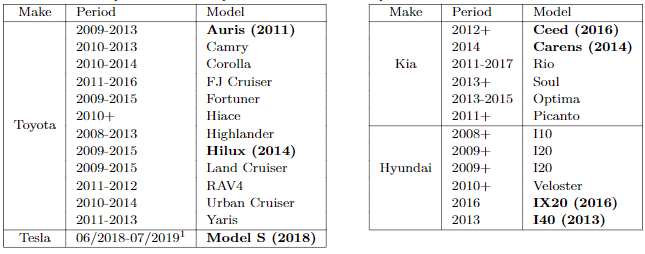
The researchers have proven that by using a Proxmark RFID reader/transmitter device near the car keys, they can steal enough information to derive the secret cryptographic key and create a fake key that can seamlessly start the car. There’s an extensive list of cars affected by this vulnerability, including the Toyota Auris, Land Cruiser, Corolla, RAV4, Hilux, and Yaris, the Tesla Model S, the Kia Picanto, Seed, and Soul, and the Hyundai I10, I20, I40, and Veloster. We should point out that Tesla was the only manufacturer to plug the problem via a firmware update that they pushed to the S owners.
The trick is done by reverse-engineering the cipher that Texas Instruments is keeping a secret since the release of the DST80. The problem is that car manufacturers simplified the otherwise robust anti-theft system for their convenience. For example, Toyota is using the vehicle serial number in the cryptographic key that’s transmitted. This significantly reduces the number of random bits that potential attackers would have to guess in order to reconstruct it. As for Kia and Hyundai, those two decided to use only 24 bits of randomness, essentially making it possible for someone with a mediocre laptop to be able to brute-force the key in a few milliseconds.
Hyundai responded by saying that no cars with low-entropy keys were sold in the United States, so I guess they were meaning to say that such systems are only deployed in countries where crime rates are low? Toyota responded by stating that the vulnerability applies to older models and that their newer cars are using a different system. Contrary to Tesla, neither Toyota nor Hyundai can do anything about the vulnerability, as a firmware update wouldn’t fix the flaw. The only thing that they could do is to offer replacements for the immobilizers or the key fobs, but so far, they haven’t offered anything like that to their customers.