The Vast Majority of Home Routers Are Vulnerable in One Way or Another
- Many router models that are sold in Europe are vulnerable to exploitation using known flaws.
- Most vendors are using unsafe securing methods, don’t push fixing firmware updates, and use unsupported OS versions.
- Netgear, ASUS, and AVM scored relatively well, although none featured absolute security.
The 2020 FKIE (Fraunhofer-Institut Fur Kommunikation) home routers security report paints a dire picture on the overall situation, highlighting the risks that this entails during the COVID-19 situation that has forced large numbers of people to work from home. The FKIE report analyzed 127 router models from seven different vendors that are sold across Europe. The researchers focused on when the devices were last updated, what OS they’re running, which vulnerabilities plague the OS kernel versions that are used, and what defense techniques are being deployed. Moreover, they looked into whether or not there were hard-coded login credentials in the devices, and if the firmware images contained private cryptographic key material.
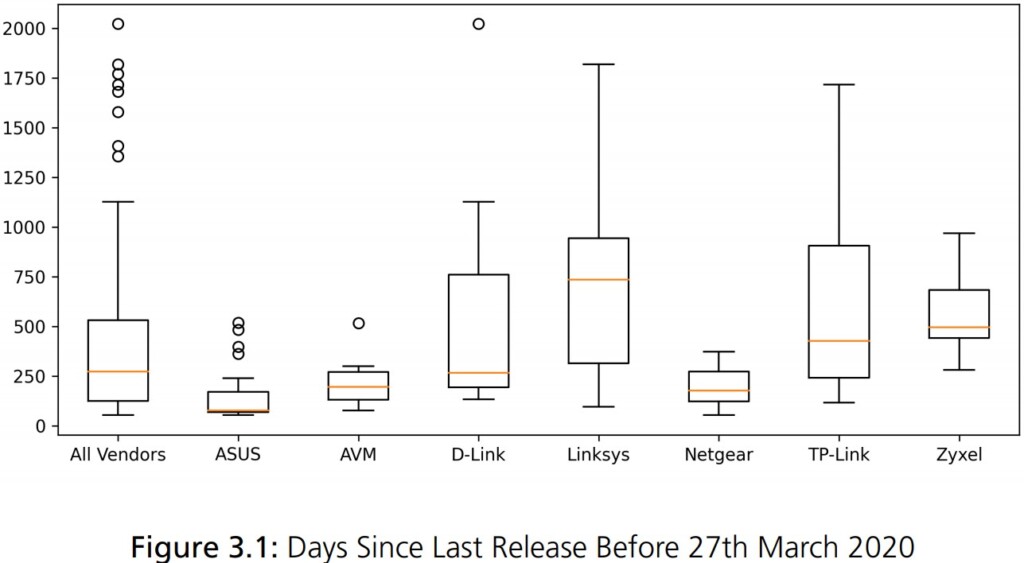
Of the 127 routers that were tested, none come out as completely secure. 36% of the router models didn’t even receive any security updates in the last 12 months, so they are vulnerable to exploitation through known and publicized flaws that often accompany PoC (proof of concept) code. Of the rest, some have easily-guessable credentials, lack any securing crypto mechanism or exploit mitigation system, and others use overly deprecated operating system versions that come with a rich set of vulnerabilities.
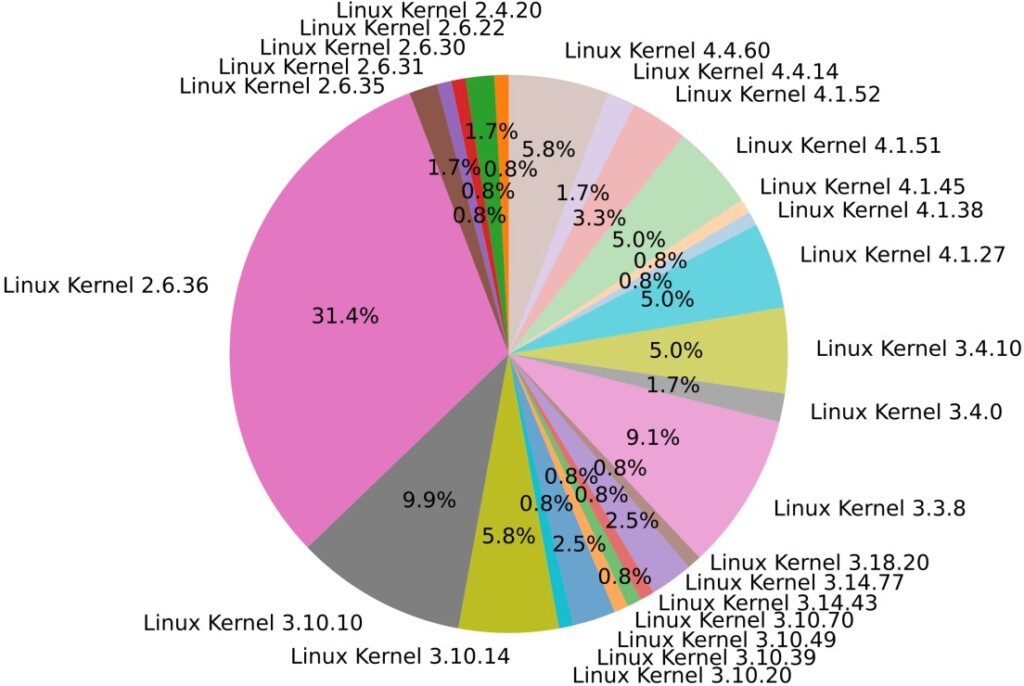
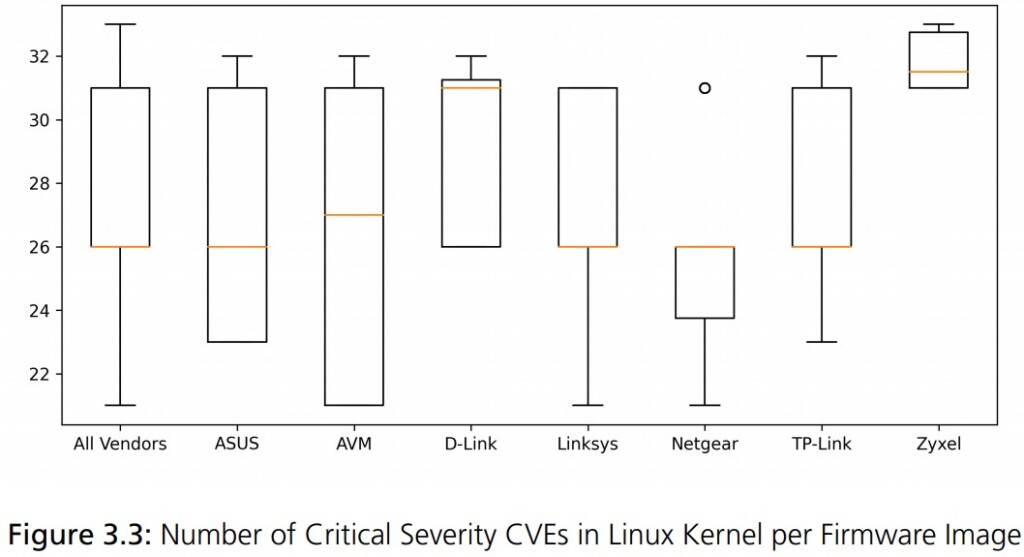
The vendors that seem to perform better in terms of how often they push firmware updates on their devices are ASUS, AVM, and Netgear. Those that fared worse are TP-Link and Linksys. As for the use of older OS kernel versions, Netgear did well on that part, and Zyxel was found to be using the most insecure systems. To get a clear picture of the situation, 90% of the analyzed routers are running Linux, and many of them still use Linux kernel 2.6, which is basically ancient. The v2.6 branch started in 2004, and support for it ended in 2016 with version 2.6.32.71. Support for Linux 2.6 was dragged over 12 years exactly because there were so many devices still using it.
FKIE explains that the above data shouldn’t be treated as absolutely conclusive, because some vendors may develop their own kernel patches, and may carry out in-depth testing and debugging procedures even though this is unlikely.
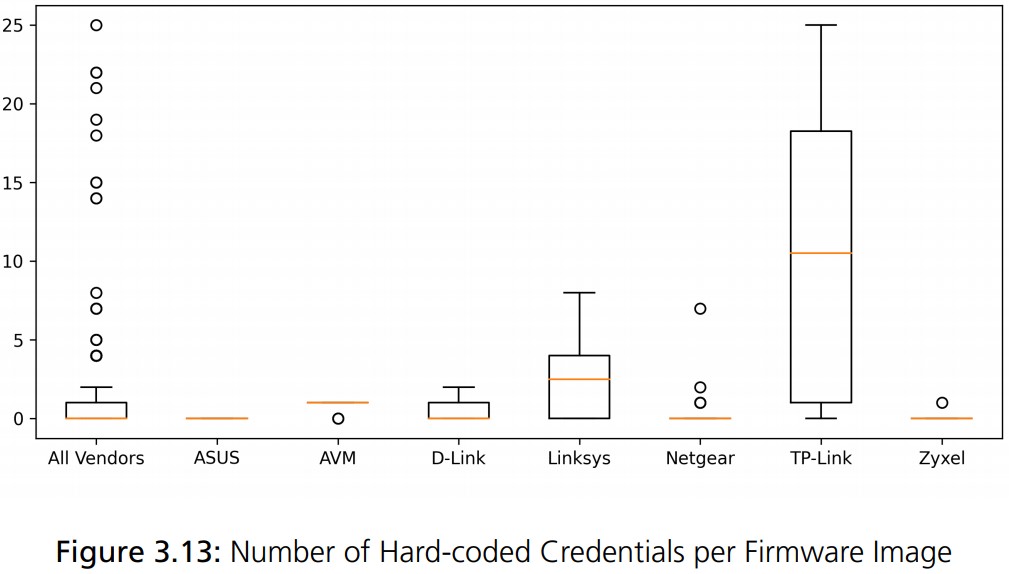
In regards to the hard-coded credentials, TP-Link is following this unsafe practice, while ASUS, AVM, Netgear, and Zyxel avoid it entirely. AVM also scores well in the area of the private keys that are published through firmware images, whereas Netgear is sharing up to 13 private keys in a single firmware image.
So, if you’re wondering what the implications of this situation are, the answer would be multi-dimensional. From Mirai bot infections to full device takeovers, and from MITM attacks to cryptojacking, anything is possible when your router is vulnerable. As for what you can do to mitigate the above as much as possible, that would include applying firmware updates when they become available, changing the default credentials into something stronger, and maybe even replacing your device with a newer model that is actively supported by the vendor.