The Vast Majority of Exploits Become Available Before CVEs Are Published
- CVE publication is nowadays clearly running behind exploits, in at least four out of five flaws.
- That is not taking into account zero-days that are being traded in private and black markets.
- Applying updates and fixing patches as soon as possible is critical, even if it’s not always enough.
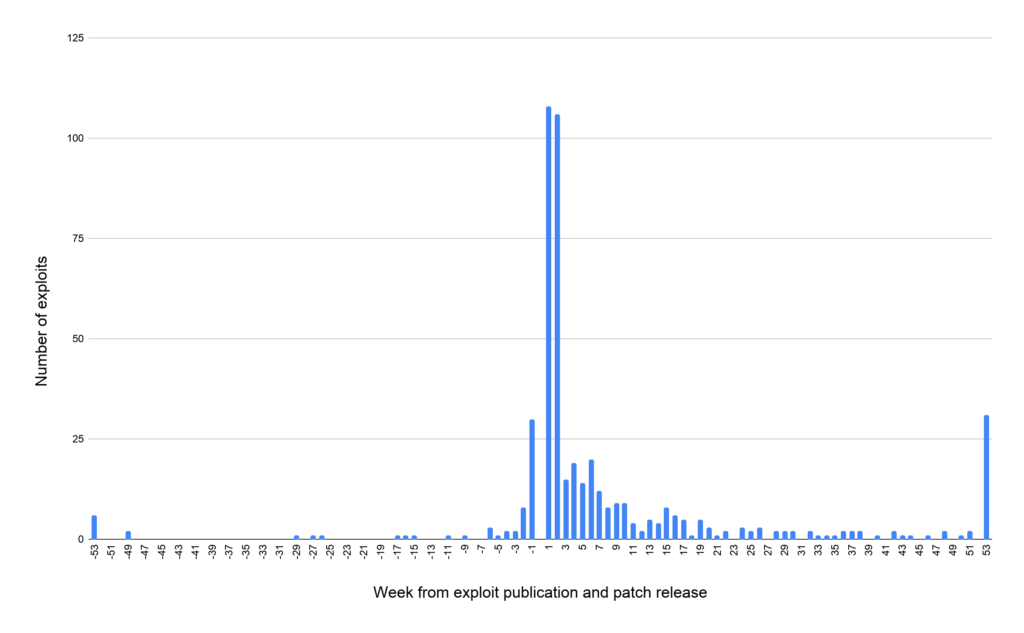
According to the data that Unit42 researchers collected and compiled into an insightful report, about 80% of public exploits out there become available before the corresponding CVE is published. Out of the 45,450 public exploits that currently populate the “Exploit Database,” only 11,079 have been assigned with CVE numbers, 14% are zero-day flaws, 23% were published a week after the patch was made available, and 50% are published within a month.
On average, the data shows that an exploit becomes available at 37 days after the patch, so not updating for roughly a month is basically entering the danger zone.
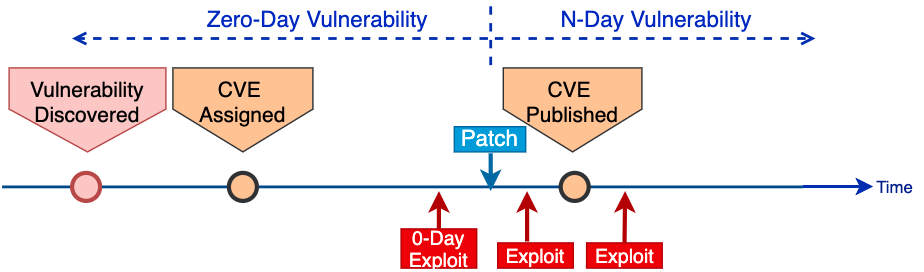
CVE stands for “Common Vulnerabilities and Exposures,” and their purpose is to officially identify a flaw. This way, researchers and developers can avoid reporting the same thing and know that they’re working to resolve a specific problem. Moreover, they can exchange details and findings, and finally reserve a space for when they can make more technical details about the vulnerability available.
Not having a CVE assigned is like not having identified a flaw, not having anyone working on fixing it in the next patch, and practically ensuring that any attempts to exploit it will be 0-days.
Source: Unit42
Publishing the CVE and the details that underpin it usually means enabling malicious actors to develop exploit code. Frequently, the publication of the CVE comes with proof of concept code, but since there’s a patch available, this shouldn’t be an issue.
As Unit42 shows, though, there are many cases where exploits appear in the wild before the CVE is published, with the actors basing their work solely on the appearance of the fixing patch.
Source: Unit42
As the security firm points out, the most problematic situations arise on open-source projects and small third-party software vendors who don’t have sufficient resources to handle reported vulnerability. These projects usually end up having to deal with 0-days before they have even assigned a CVE identificator.
A recent example that underlines this problem is the Tor Project, which has its bug reporters begging it to pay attention to their reports.
Source: Unit42
There’s an increasing number of vulnerabilities getting discovered today, as more people are involved in the process of finding them, software becomes more complex, there are far more tools out there, and entities pay more money either way (finding and plugging or finding and exploiting) since people’s reliance on software grows bigger.
The above stats do not include what exploits are traded in private and black markets, so the situation is actually much worse than what’s presented here. All that said, your best bet would be to patch as soon as possible, even mere hours after fixes arrive via an update.