The “Valak” Malware Has Grown to Become More Than Just a Loader
- The developers behind Valak have published thirty versions in the last six months, turning the loader into a sophisticated malware.
- Valak can now check system information, and even steal user credentials from MS Exchange servers and certificates.
- The actors behind the tool seem to have connections with the Russia-speaking cyber-crime.
Valak first appeared during the last months of 2019 and was initially used solely as a malware loader in campaigns that targeted American and German entities. However, an investigation by the Cybereason Nocturnus team of researchers that revisited the particular tool found that it’s now a malware on its own, and a quite sophisticated one too. Over the last six months, the authors of Valak have pushed 30 versions, steadily upgrading the tool and making it a powerful information stealer while maintaining its payload-fetching and dropping capabilities.
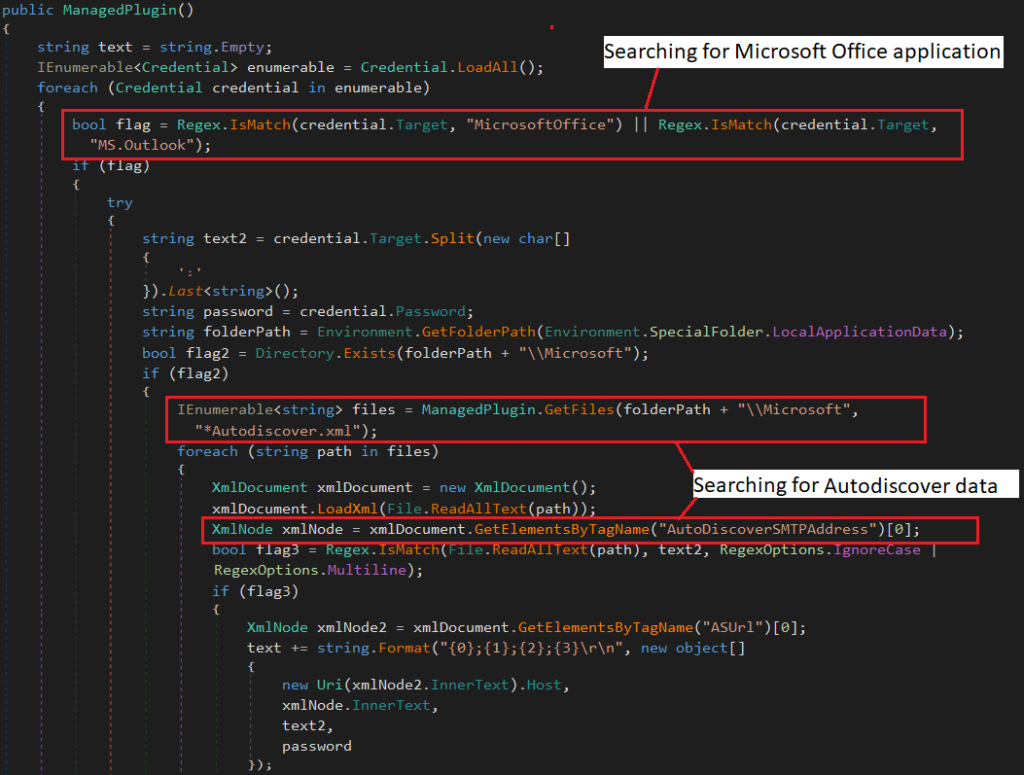
Valak continues to be used in campaigns that target enterprise entities in the US and Germany, using documents that have malicious macro code embedded in them. This code fetches a DLL file that initiates a multi-stage attack involving WinExec API calls, execution of JavaScript files, planting of registry keys, and, eventually, the setting up of scheduled tasks for persistence. One difference between older and more recent versions is the obfuscation that is deployed, as an XOR cipher is added on top of the Base64 hashing that already existed.
Source: Cybereason Blog
The latest versions of Valak are capable of stealing credentials from enterprise network users, extracting them from Microsoft Exchange server data and domain certificates. The consequences of this are grave, as it opens up the door to access key accounts, move laterally in the organization’s network, exfiltrate data, run ransomware tools, and eventually cause damage that would have catastrophic results in the brand prestige and customer trust of the victimized organization.
Source: Cybereason Blog
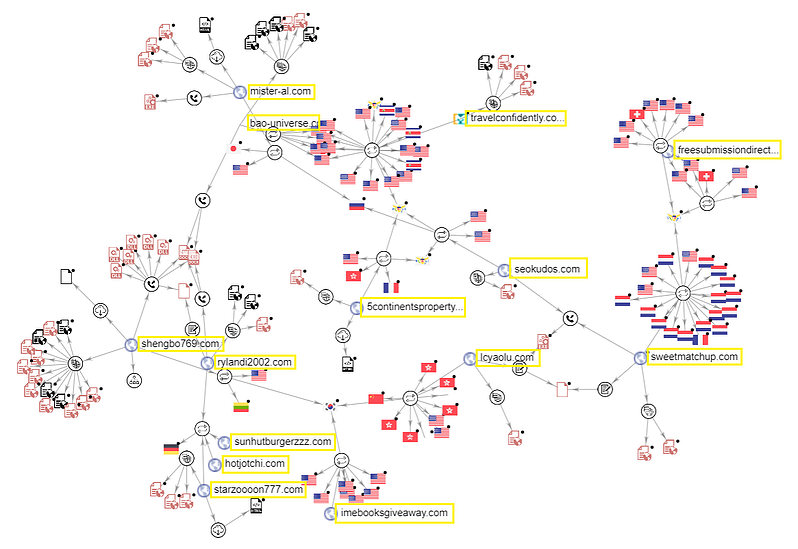
In regards to additional payloads, current campaigns fetch “IcedID” and “Ursnif,” both sourced from the same C2 server that hosts Valak. Thus, there’s a clear connection with the Russian-speaking cybercrime ecosystem, and Valak is considered to be an integral part of it.
Source: Cybereason Blog
Valak is evolving quickly, its C2 is updated continually, and even the malicious executables and scripts used are changing names with each new version. Cybereason has compiled a detailed list with the current indicators of compromise that concern Valak, so you should make sure to take a look. Other than that, disable the macros on your office suite, and only enable content for documents that you absolutely trust. Email attachments shouldn’t qualify as trustworthy, and even if they come from a business partner, they could be the result of an email account compromise. Valak’s evolution has enabled it to engage in this type of operation, so beware.