A U.S. Supreme Court Compromised by “Conti” Ransomware Actors
- The “Conti” ransomware group has become the first to attack a US court and leak sensitive documents.
- The extortion process may have begun, but the court’s administrators may not have even realized the attack yet.
- Experts believe this could be the result of a phishing attack launched against an employee of the court.
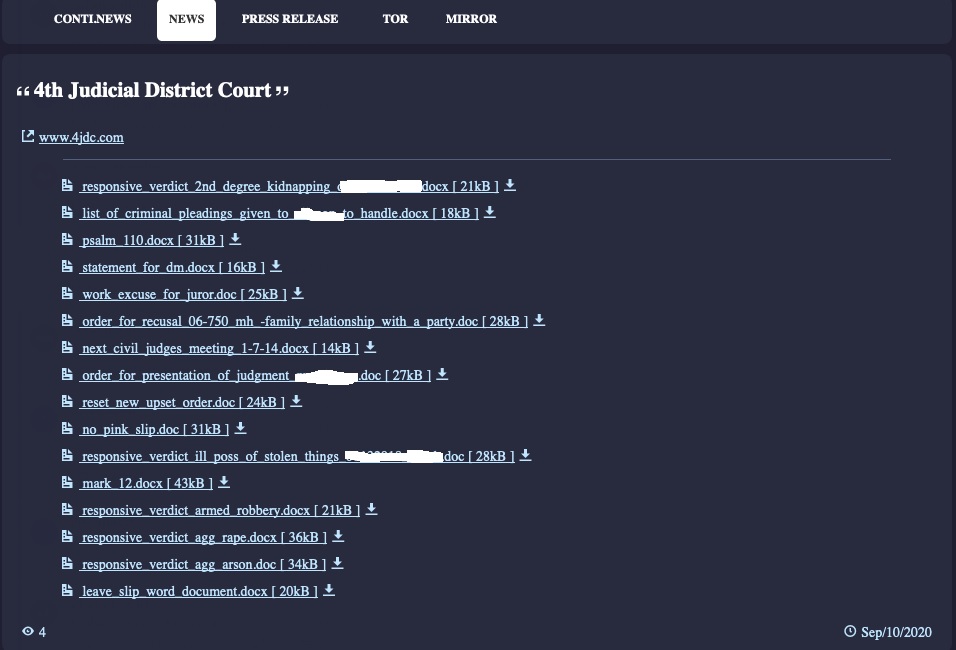
The recently formed group of ransomware actors behind the “Conti” moniker have carried out a bold attack against an American court, which is something that we see for the first time. The reported victim court has denied the incident ever happened so we had to remove the mention. However, the hackers are already leaking samples of the stolen files on their dedicated dark web page.
The files presented there include sensitive documents relevant to cases reviewed by the court, containing information about jurors, witnesses, defendant pleas, etc. The repercussions for those exposed are dire, and it is unknown if the court ever notified the affected individuals.
Source: Computer Business Review
Right now, the court’s official net portal is down and has been like that for a couple of days. Either the IT team is working towards cleaning the servers, or the actors are trying to somehow draw the attention of those responsible.
The public sector is always a tricky target because getting a response from the administrative teams is sometimes challenging. Similarly, getting payments can be proven complicated, but notorious ransomware groups have been trying that nonetheless. Still, this is the first incident that concerns a US court, and which involves data exfiltration and leakage.
The fact that this is the work of Conti was confirmed by Emsisoft, an expert in the field who tracks ransomware attacks and attributes them based on the traces left behind or other indications. They, too, confirmed that this is the first of its kind and the 207th ransomware attack that is hitting a public sector entity so far in 2020.
Conti is a particularly nasty piece of malware that executes up to 160 individual commands, trying to wreak havoc and make the work of first-responders a lot harder. Also, as we have discussed before, Conti is propagated by skillful and experienced hackers who know their way around.
Related: A Volkswagen Dealership Has Been Hit by “Conti” Ransomware
Hank Schless, the Senior Manager at Lookout, has provided us with the following comment on the incident:
We have no way to tell if this attack was the result of a phishing attempt against one of the court’s employees, but it looks like Hank is giving some serious chances to this scenario. It is highly unlikely that the victimized court will publish a statement detailing the specifics of the attack since they already denied there was a cyber-attack affecting them. That said, we’ll have to contain ourselves to assumptions on this one.