US Cyber Command Warns About Imminent PAN-OS Bug Exploit Wave
- A freshly discovered and patched critical vulnerability threatens corporate networks with catastrophic attacks.
- An actor could potentially access protected information on the unpatched systems without having to authenticate.
- System administrators have to apply the available patches or change the configuration as soon as possible.
US Cyber Command is warning the public about “CVE-2020-2021” and urges system admins to patch immediately. As the agency characteristically wrote on Twitter, foreign APTs will likely attempt to exploit this critical vulnerability very soon, so updating the below products made by Palo Alto Networks is non-negotiable at this point.
- GlobalProtect Gateway
- GlobalProtect Portal
- GlobalProtect Clientless VPN
- Authentication and Captive Portal
- PAN-OS next-generation firewalls (PA-Series, VM-Series) and Panorama web interfaces
- Prisma Access systems
Please patch all devices affected by CVE-2020-2021 immediately, especially if SAML is in use. Foreign APTs will likely attempt exploit soon. We appreciate @PaloAltoNtwks’ proactive response to this vulnerability.
— USCYBERCOM Cybersecurity Alert (@CNMF_CyberAlert) June 29, 2020
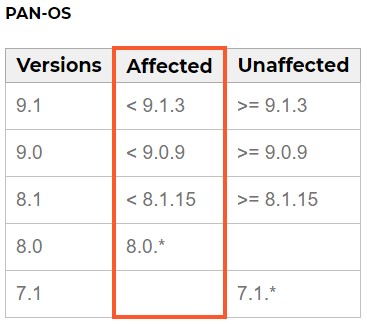
This vulnerability involves authentication bypass in SAML (Security Assertion Markup Language), potentially enabling an attacker to access protected resources without requiring any user interaction. Due to the low level of complexity involved in exploiting the bug, experts in the field fear that an attack wave targeting unpatched systems is bound to rise in the next couple of weeks or even days. To get an idea of which products are vulnerable and which versions are safe to use, check out the following table.
Source: security.paloaltonetworks.com
If updating is impossible for any reason, you should disable the “SAML Authentication” from being a valid authentication method. You can do this through Device/Panorama → Server Profiles → SAML Identity Provider. If you have the capacity to apply the update instead, just make sure that the signing certificate for the SAML Identity Provider is properly configured. Otherwise, you may end up barring your users out too.
Deciding to take no action now would be the worst possible approach, and you should bear in mind that figuring out which logins or user sessions were valid and which ones were malicious will be quite hard by looking into the system logs later on. While there’s no evidence that the flaw is already being under active exploitation right now, you should still check all logs for signs of trouble like unusual usernames or source IP addresses.
Actors love VPN flaws, and they have shown their inclination to targeting corporate systems through these entry points numerous times in the recent past. That said, there’s no margin for delays in applying the available patches. Even with the US Cyber Command office issuing warnings and the media reproducing the urgent message, some systems will remain unpatched, as always, and actors will get to enjoy a 10/10 CVSSv3 way in these systems. Hopefully, the certain configuration needed for the exploit to work won’t be commonplace, so the impact will be kept at a minimum.