US Charges Russian Civilian Connected to WhisperGate Malware Targeting Ukraine
- The U.S. returned an indictment charging a Russian citizen with conspiracy to hack into and destroy Ukrainian computer systems and data.
- The defendant is alleged to have helped with an attack launched prior to Russia’s February 2022 invasion of Ukraine.
- This is known as the WhisperGate malware campaign and targeted several Ukrainian ministries, exfiltrating data and selling it online.
The U.S. Department of Justice (DoJ) charged a Russian civilian with conspiracy to infiltrate and destroy Ukrainian government computer systems via data-destroying malware known as WhisperGate in January 2022, a hacking effort by Russia before the Federation’s illegal invasion of Ukraine in February 2022.
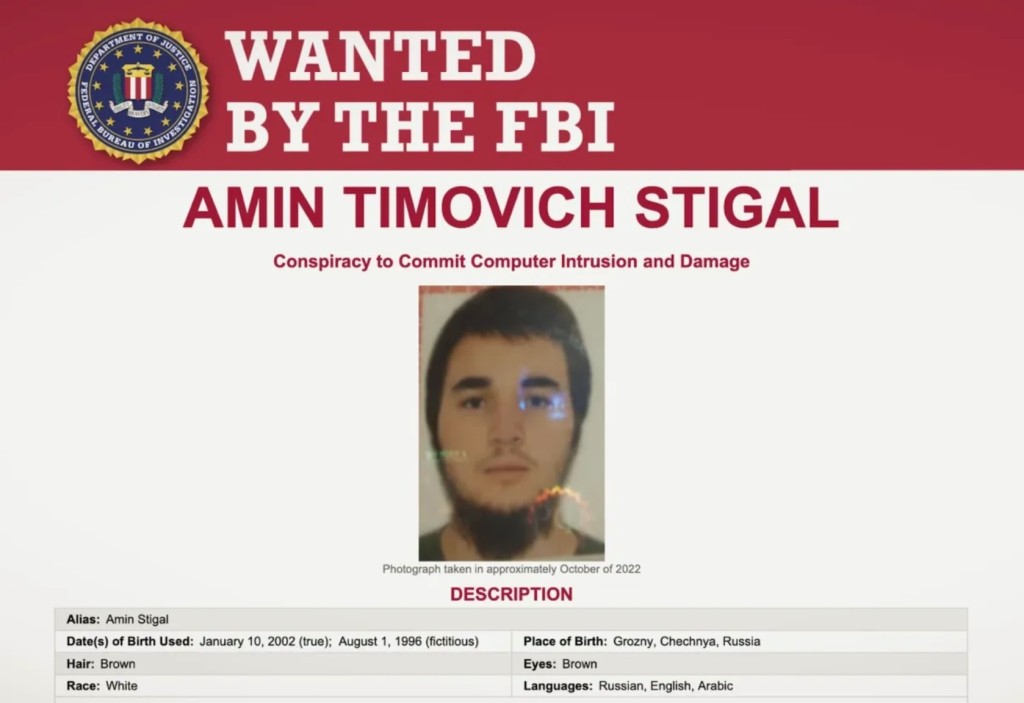
Amin Timovich Stigal, 22, is wanted for “helping to set up servers used by Russian government hackers” in the WhisperGate cyberattack on Ukrainian ministries. The U.S. Department of State’s Rewards for Justice program is offering a reward of up to $10 million for details on the civilian’s location or malicious cyberactivity. If convicted, Stigal could face a maximum penalty of five years in prison.
The indictment alleges WhisperGate was actually a cyberweapon created to “completely destroy the target computer and related data.” The U.S. government, allies, and partners attributed this cyberattack to the Russian military and condemned this and similar destructive cyber activities against Ukraine in May 2022.
Court documents say Stigal and members of the Main Intelligence Directorate of the General Staff (GRU) of the Russian Federation conspired to use the services of a company based in America to infect with the WhisperGate malware and destroy the computer systems of dozens of Ukrainian government entities.
On January 13, 2022, GRU infected the Ukrainian Ministry of International Affairs, State Treasury, Judiciary Administration, State Portal for Digital Services, Ministry of Education and Science, Ministry of Agriculture, State Service for Food Safety and Consumer Protection, Ministry of Energy, Accounting Chamber for Ukraine, State Emergency Service, State Forestry Agency, and Motor Insurance Bureau computers and networks with malware designed to look like ransomware.
GRU compromised several Ukrainian computer systems, exfiltrating sensitive data, defacing the websites, and immediately putting the hack for sale online to generate concern among the Ukrainians regarding “the safety of government systems and data.”
The indictment says that between August 2021 and February 2022, GRU leveraged the same computer infrastructure they used in the Ukraine attacks to probe the computers of a federal government agency in Maryland using the same tactics. In August 2022, GRU reportedly hacked the transportation infrastructure of a Central European country that was supporting Ukraine.
The latest news on espionage groups says the SneakyChef gang expanded its scope to EMEA and Asia government agencies, deploying a remote access trojan dubbed SugarGh0st onto the infected systems.