The Ups and Downs of the Threat Landscape in Q2 2020
- Another quarter has passed, and it’s time to look into the threat statistics as ESET recorded them.
- Most types of threats remained stable in terms of their infection volumes, but particular tools’ popularity has shifted.
- RDP connection attempts spiked, whereas cryptominers continue their downward spiraling.
ESET has released its Q2 2020 threat report, allowing us to look at what’s trending, what’s fading, and what remains unchanged. The cyber-crime and malware infection landscape is a complex ecosystem affected by numerous factors, so looking at the stats at the end of a quarter is always a great way to figure out what really happened.
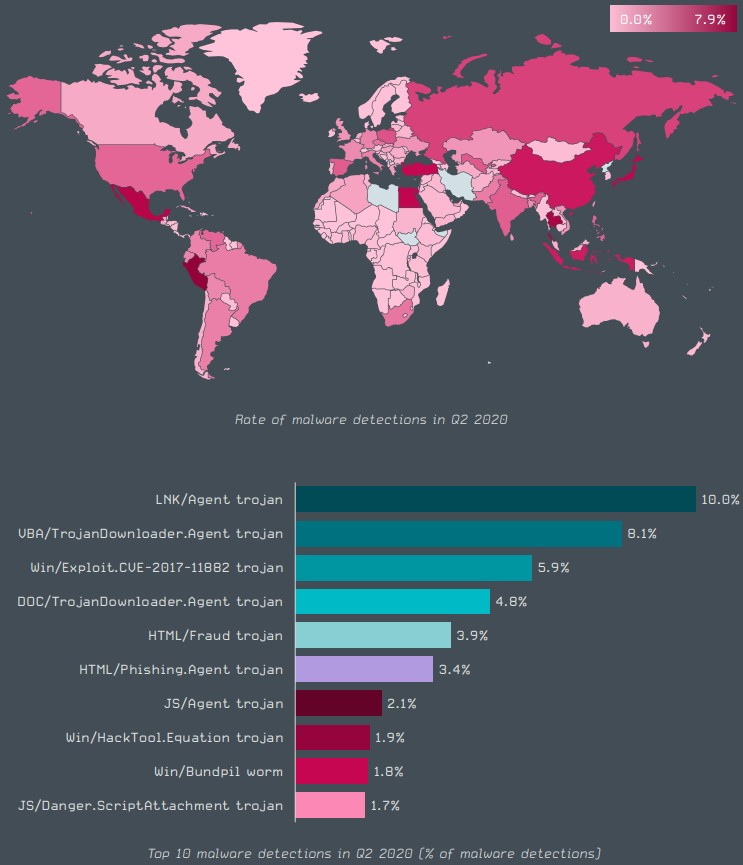
Starting with the top 10 malware detections, the first place goes to “LNK/Agent,” which is basically a piece of software that utilizes Windows LNK shortcut files to execute something else, like downloaders or payloads for example. The second most widely used malware is “VBA/Trojan,” which is typically malicious MS Office files that attempt to convince the recipient to enable the execution of macros on their suite.
Source: ESET
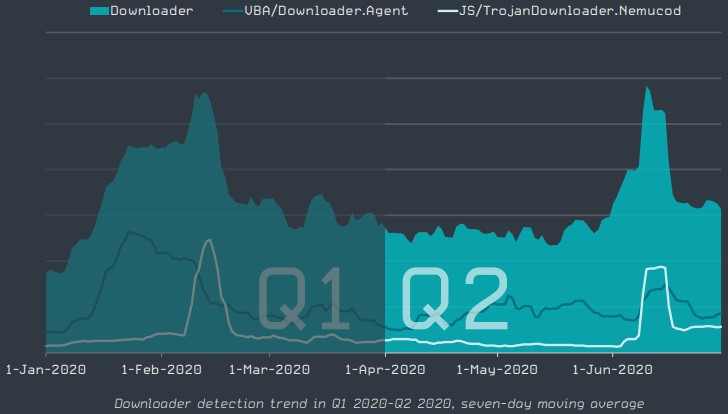
In the “downloaders” sector, ESET recorded a slight decline compared to Q1 2020. The most significant threat here was “Nemucod,” which targeted mainly Japanese internet users.
Source: ESET
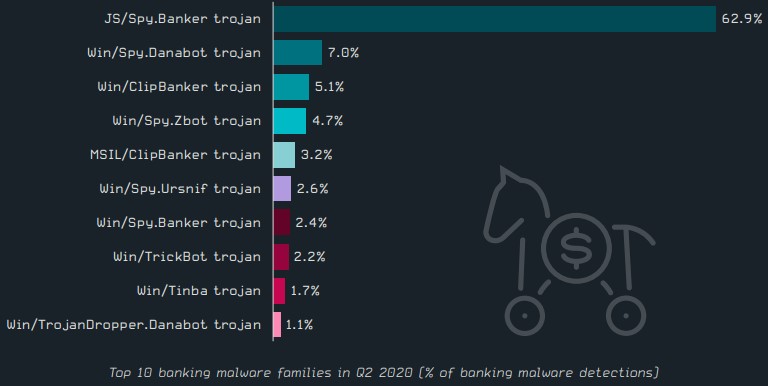
The deployment of banking malware remained more or less stable since the beginning of the year, with Spy Banker taking the lion’s share, followed by Databot in second place.
Interestingly, Trickbot, which was extensively used in Q1 2020, has now tumbled in the eighth position - accounting for only 2.2% of the detections.
Source: ESET
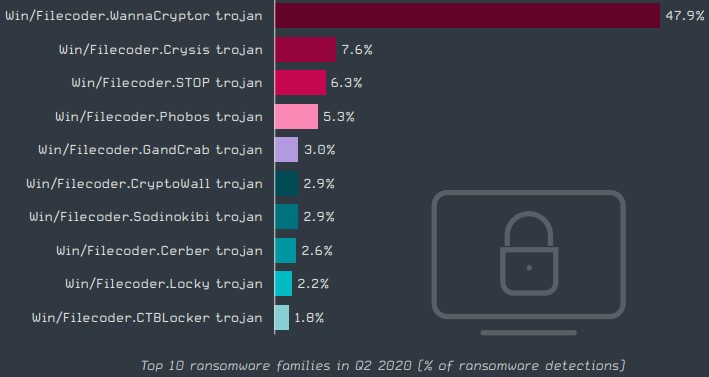
Moving forward with the always-hot category of the “ransomware” threats, the infection volume remained stable, although there were a couple of peaks caused by WannaCryptor in June. This was the most widely used ransomware family in Q2 2020, with 47.9% of all detections pointing to one of its strains.
The highly catastrophic REvil/Sodinokibi only accounted for 2.9% of detections, as the group behind it is focusing on prominent targets. Interestingly, the now unlocked GandCrab is still in the top ten, with 3.0%.
Source: ESET
Cryptominers continued to fade, and the Bitcoin halving event only secured this trend, as we predicted the halving happened. Whatever goes on in the field is taking place on Linux servers and Windows systems.
Mac and Android are completely absent from the cryptominers detection data.
Source: ESET
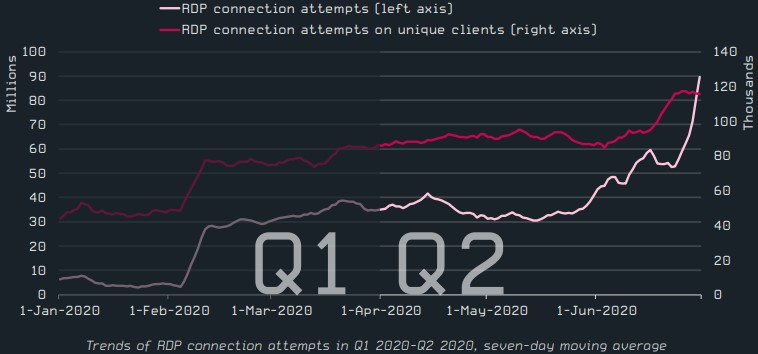
What’s clearly on the rise is RDP (Remote Desktop Protocol) connection attempts, which is attributed to the COVID-19 situation that pushed large numbers of employees to work from home.
Source: ESET
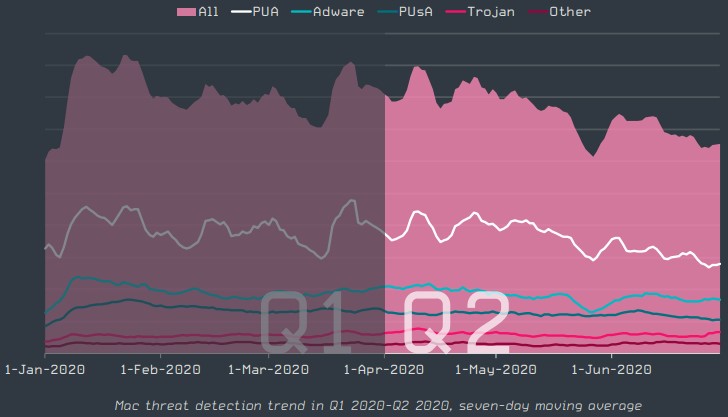
In the Mac space, the most prevalent threats concern malware that attempts to convince the user to buy overprices services they don’t need. Mac users are typically open to buying and spending, so this is what malicious actors are looking to exploit.
Source: ESET
As for the Android ecosystem, ESET’s telemetry data show a rise of 18% in the number of detections compared to Q1 2020.
The biggest problem here was hidden apps running secretly in the background - with adware and SMS trojans completing the picture.
Source: ESET
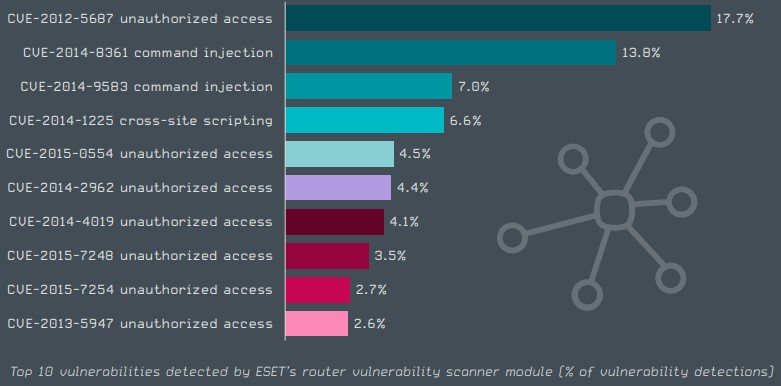
Finally, the IoT security landscape seems to be plagued by the same old “weak password” problem that has been troubling them since day one. A 17% percentage concerns unauthorized access to IoTs whose owners didn’t bother to change the default password.
Source: ESET