Update to iOS 14.4 Now to Plug Three Actively Exploited “Zero Day” Bugs
- The iOS 14.4 has landed, and it fixes three zero-day flaws that are under active exploitation.
- Apple hasn’t shared much info about who exploits them or who’s the target, and neither do we have technical details.
- The attack chain may be click-less, as two of the flaws lie in Safari’s web engine, WebKit.
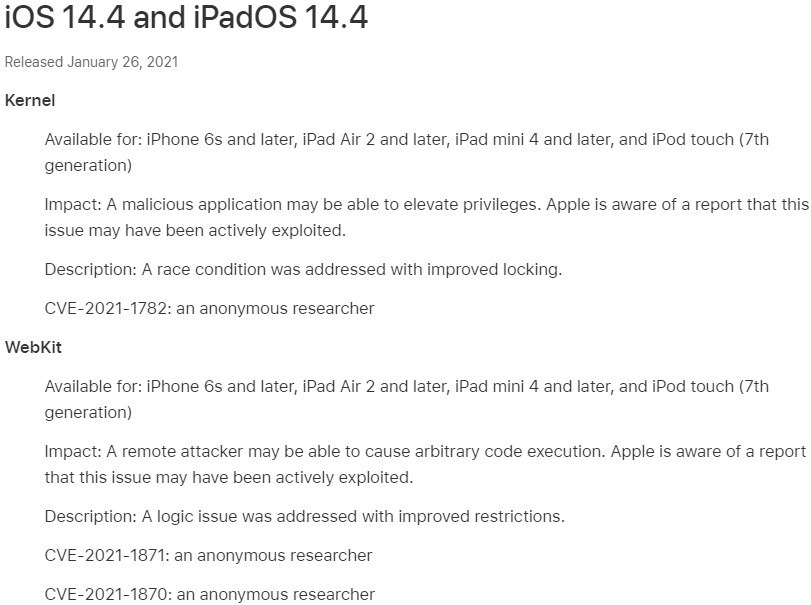
Apple has released iOS 14.4 and iPadOS 14.4, fixing three flaws that, according to the company, may have been actively exploited. These are CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871, which are all privilege escalation leading to remote code execution bugs.
There are no in-depth details in the release notes about these flaws because obviously, there’s still a large number of people who haven’t updated to iOS 14.4 yet, so giving away the details of how to exploit these vulnerabilities isn’t the standard practice. Also, the discovery was attributed to an “anonymous” researcher, so we’re not expecting to see a write-up on a blog out there soon.
Two of the vulnerabilities are in WebKit, which is Safari’s engine, while the other one is on the OS kernel. The first two were fixed by improving restrictions that addressed a “logic issue,” while the kernel flaw that relied upon a race condition was dealt with through improved locking. Due to the nature of the bugs, we would suggest that the attacker compromised the targets by alluring them to specially crafted websites, similar to what we’ve seen being deployed in the past against Uyghurs in China.
Having no actual details about the adversaries, the targets, the extent of the problem, and the exploitation process, all that we can say to you right now is to upgrade to iOS 14.4 immediately and forget about the rest.
Along with the fixes on the above issues, iOS 14.4 will bring the following fixes:
- Image artifacts could appear in HDR photos taken with iPhone 12 Pro
- The fitness widget may not display updated Activity data
- Typing may be delayed, and word suggestions may not appear on the keyboard
- The keyboard may not come up in the correct language in Messages
- Audio stories from the News app in CarPlay may not resume after being paused for spoken directions or Siri
- Enabling Switch Control in Accessibility may prevent phone calls from being answered from the Lock Screen
As for the new features and improvements, this is a minor release, so there aren’t many new things. Apple is introducing some tweaks to help the camera recognize smaller QR codes, added an option to classify Bluetooth device type in Settings for correct identification of headphones (for audio notifications), and added notifications for when the camera on the device cannot be verified as genuine.