UC Browser Silently Downloads Libraries and Modules Through HTTP
- UC Browser is violating Google Play’s policy by fetching and installing updates from outside the store.
- Researchers have found that it does so through HTTP communication, risking MitM attacks.
- Only the “Mini” version is safe for now, but the regular one remains available in the Play Store nonetheless.
As reported by the Dr. Web Anti-Virus team, the popular Android browser “UC Browser” is updating itself any time it wants, without letting the user know of the fact, and by bypassing Google’s app store. This goes directly against the Google Play “Privacy, Security, and Deception” policies and guidelines, which forbid apps from downloading executable code from any other source than Google Play. UC Browser has had this hidden ability since its early 2016 versions, so those who have been using it for a long time have exposed themselves to MitM (man in the middle) attacks.
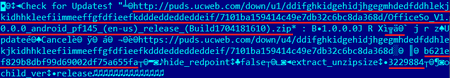
UC Browser has been downloaded many millions of times by Android users, with the latest 2019 version alone counting about 10 million users. Dr. Web researchers have confirmed the presence of the risky feature in version 12.10.8.1172, and warn of a complex modular architecture that gets constantly enriched and refreshed with new libraries and modules. This updating activity is kept secret from the user and takes place in the background with the help of the Tinker library. While this doesn’t mean that the developers of UC Browser are pushing malicious updates to their userbase, it does make the app vulnerable to MitM attacks.
image source: st.drweb.com
Since the browser app is communicating with a remote host via an unprotected HTTP channel, the door for cybercriminals to get in the middle is open, so they can push what they want to millions without the UC Browser developers even realizing. The fact that there is no verification process based on a digital signature makes the whole procedure even riskier, allowing malicious actors to hook the server response and replace the link to the downloaded update.
As the researchers point out, this practice is utterly dangerous, and the people who are using the regular Android or the desktop version should uninstall it immediately. If you wish to continue using UC Browser products, the “Mini” version of the app seems to be safer, as there’s no “under the hood updating” going on there. The developers of the UC Browser have not responded with an official statement yet, and Google has not removed the apps from the Play Store at the time of writing this. Maybe Google is hesitant to remove an app that violated their policies so blatantly because of its popularity, but still, the findings of Dr. Web have been confirmed by other researchers as well.
Are you using UC Browser, and do you plan on continuing to do so? Share your thoughts in the comments section below, and don’t forget that Technadu’s Facebook and Twitter pages are where the heart of our online community beats.