Ubuntu 22.04 Printing Subsystem Flaw Allowing Arbitrary Code Execution, Thwarted by Compiler
- A flaw in the printing subsystem of Ubuntu 22.04 that allowed arbitrary code execution was stopped by a compiler feature.
- Connecting a malicious printer that reports oversized media dimensions caused a buffer overflow during initialization.
- This flaw triggered a segmentation fault within the “ippusbxd” daemon connected to an Ubuntu machine.
A recently identified flaw in the Ubuntu 22.04 printing subsystem allowed arbitrary code execution on locked laptops. Yet, the exploitation was thwarted by a compiler feature that replaces unsafe functions with more secure alternatives that can detect and prevent memory corruption.
The vulnerability was uncovered during a code audit of the macOS printing subsystem, which shares foundational components with the open-source Common UNIX Printing System (CUPS).
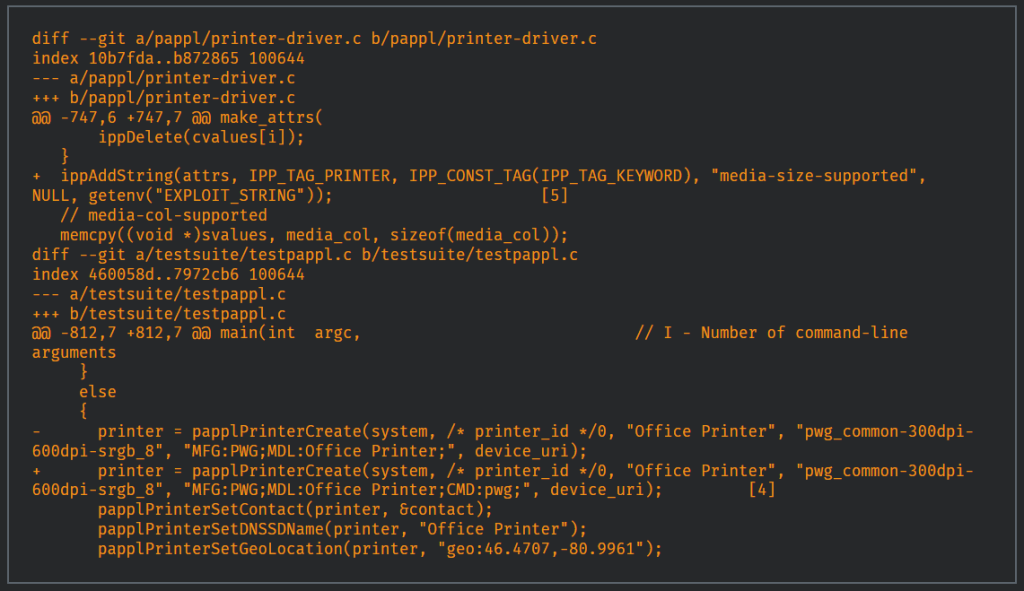
Cisco Talos Intelligence investigated the Internet Printing Protocol over USB (IPP-USB), with a focus on the “ippusbxd” package in Ubuntu 22.04, and identified a buffer overflow vulnerability in the "get_format_paper" function of the package.
The flaw stemmed from the use of the "strncpy" function, with an argument improperly derived from the source operand’s length rather than the size of the destination buffer. Specifically, attackers could exploit this flaw by connecting a malicious printer that reports oversized media dimensions, causing a buffer overflow during initialization.
To validate the vulnerability, Aleksandar Nikolich of Talos created a proof-of-concept (PoC) exploit using a Raspberry Pi Zero configured to emulate a malicious USB printer.
Leveraging the Linux USB Gadget API, the fake printer reported malicious media dimensions via a specially crafted “media-size-supported” payload, which triggered a segmentation fault within the “ippusbxd” daemon when connected to an Ubuntu machine.
While the vulnerability could cause a crash in the printing subsystem, further analysis revealed that the exploitation was thwarted by a compiler feature known as “FORTIFY_SOURCE.” This feature, enabled by default in modern compilers, replaces unsafe functions with more secure alternatives that can detect and prevent memory corruption.
Thanks to this safeguard, the vulnerability's potential impact was limited to a system crash, preempting arbitrary code execution.
Further reducing concerns, Canonical has transitioned from the legacy “ippusbxd” package to the modern “ipp-usb” package in newer Ubuntu releases. The latter is implemented in a memory-safe programming language, effectively mitigating risks like buffer overflows.
While Ubuntu 22.04 continues to use “ippusbxd” due to its long-term support status, users of newer versions can benefit from improved security provided by the “ipp-usb” package.
In other news, two aggressive botnets targeted documented vulnerabilities in D-Link routers to gain full remote control of the devices.