UAT-5918 Threat Actor Targets Critical Infrastructure Entities in Taiwan with Mimikatz
- The group relies on open-source tools such as FRPC, FScan, Earthworm, and Neo-reGeorg.
- UAT-5918 overlaps with some Chinese-linked APT groups targeting similar verticals for intelligence.
- Tools such as Mimikatz, LaZagne, and browser credential stealers are also deployed.
A newly reported cyber campaign tracked as UAT-5918 has been identified targeting critical infrastructure entities in Taiwan, which is believed to be executed by an advanced persistent threat (APT) group focused on long-term information theft through sophisticated intrusion techniques.
Active since at least 2023, UAT-5918 is an APT leveraging tailored tactics, techniques, and procedures (TTPs) to infiltrate and maintain persistence in victim environments. The campaign’s primary focus has been on critical infrastructure in Taiwan, such as telecommunications, healthcare, and IT.
The group primarily exploits known vulnerabilities in unpatched internet-exposed web and application servers to gain initial access, Cisco Talos Intelligence Group revealed in a recent report.
Once inside a network, their strategy revolves around manual post-compromise activities to gather critical information, steal credentials, and create backdoors for sustained access.
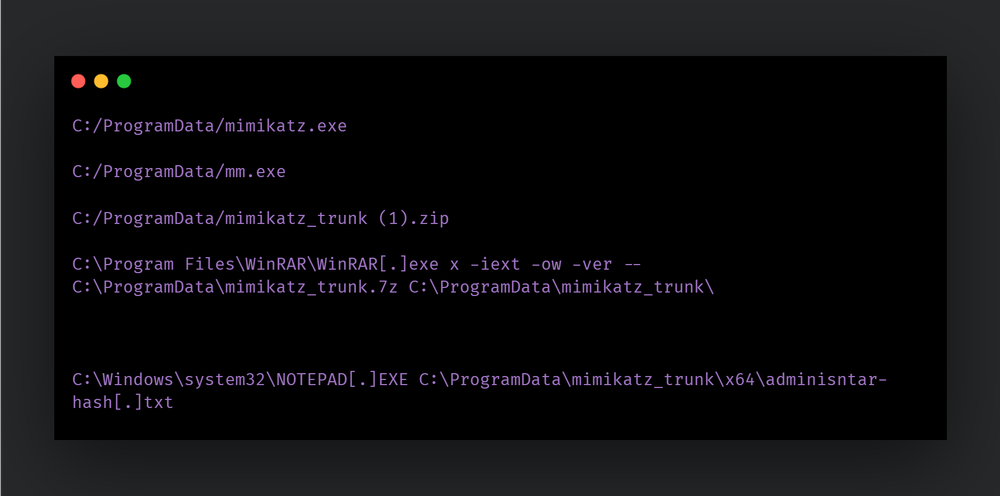
Key activities observed include the deployment of Web shells to establish entry points for continued access and credential harvesting via tools like Mimikatz, .NET-based password cracker SNETCracker, and browser credential extractor BrowserDataLite, a tool to extract Login information, cookies, and browsing history.
Open-source tools such as FRPC, FScan, Earthworm, and Neo-reGeorg are employed for reconnaissance, lateral movement, and establishing reverse proxy tunnels.
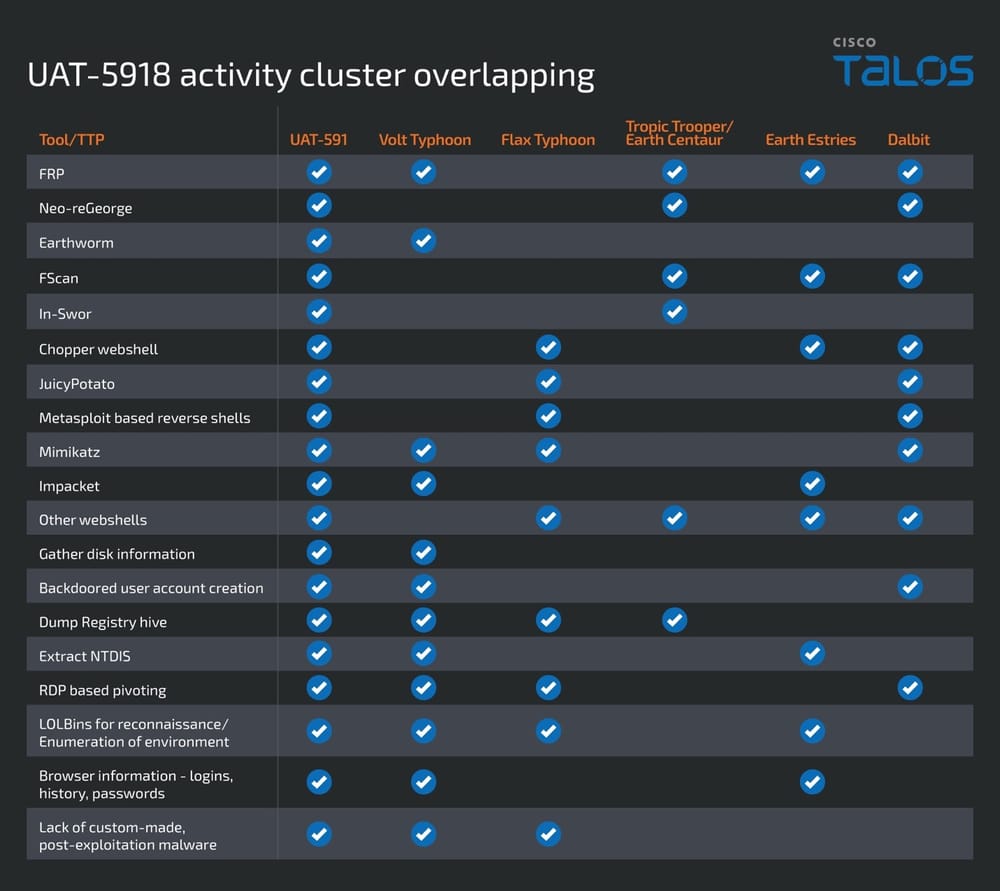
UAT-5918 shares significant TTPs and tooling with other well-documented APT groups, such as Volt Typhoon, Flax Typhoon, Earth Estries, and Dalbit.
- Volt Typhoon Overlaps: Similar use of tools like In-Swor, FRP, Impacket, and a strong focus on living-off-the-land methodologies. Volt Typhoon has been attributed to Chinese state-sponsored activities targeting U.S. critical infrastructure.
- Flax Typhoon Overlaps: Commonalities include web shells (e.g., Chopper), Mimikatz, and PowerShell tools. Flax Typhoon is also linked to Chinese government-sponsored hacking.
- Additional Overlaps: Tools like JuicyPotato and Tropic Trooper-associated utilities further align UAT-5918 with notable APT operations.
However, UAT-5918 stands apart with specific tools such as LaZagne and SNetCracker that are not widely seen in use by other actors, suggesting unique or lesser-documented capabilities. These alignments suggest that UAT-5918 shares strategic objectives with other Chinese-linked APT groups targeting similar verticals for geopolitical and economic intelligence.
Once access is established, UAT-5918's operations demonstrate meticulous planning and execution. Commands like ping, tasklist, and whoami are used to map out compromised environments.
Sensitive organizational data is staged locally and exfiltrated, including database backups via utilities like SQLCMD, while Web shells and reverse Meterpreter shells are deployed across critical systems, alongside privileged user accounts for long-term control.