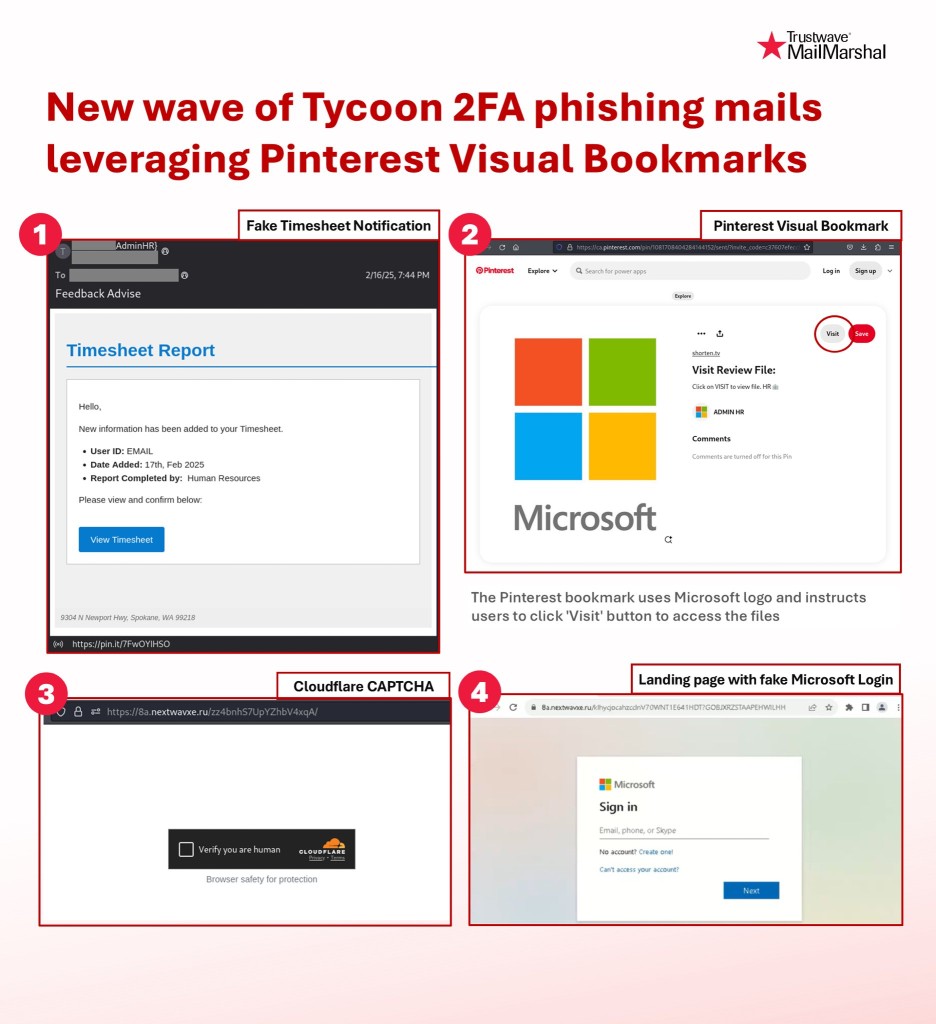
Tycoon 2FA Phishing Campaign Uses Fake Timesheet Report Emails
- A sophisticated phishing campaign leverages Pinterest Visual Bookmarks and the Microsoft logo.
- Hackers begin with an email pretending to notify the receiver about an alleged timesheet report.
- Adding CAPTCHA verifications for perceived legitimacy, the campaign ultimately runs the Tycoon 2FA PhaaS.
Hackers use fake timesheet notification emails to compromise user credentials and bypass Multi-Factor Authentication (MFA). They employ the Tycoon 2FA phishing kit and deceptive tactics, leveraging Pinterest Visual Bookmarks to enhance credibility.
Cybersecurity experts at SpiderLabs have revealed this discovery via a post on X (formerly Twitter).
The attack initiates with a phishing email titled “Timesheet Report,” which claims new information has been added to the recipient’s timesheet. The email invites the victim to click a “View Timesheet” button, redirecting them to a link hosted on Pinterest.
Using Pinterest Visual Bookmarks as an intermediary is an unusual and potentially effective strategy. This step capitalizes on the trust Pinterest commands, presenting a page with a prominently displayed Microsoft logo and a “Visit” button.
Once the user clicks “Visit,” they are redirected to a .ru domain, which prompts them to complete a Cloudflare CAPTCHA challenge. While this CAPTCHA step further adds to the campaign’s legitimacy, it also filters out automated bots, ensuring that only human users proceed.
The final stage of the attack displays a fake Microsoft login page, where visitors are prompted to input their credentials. Any information entered is immediately harvested by the Tycoon phishing kit, granting attackers access to sensitive accounts while bypassing MFA security measures.
Security analysts at SpiderLabs emphasized that these new methods, particularly the use of Pinterest and CAPTCHA verification, signal an evolution in phishing tactics aimed at tricking well-informed users.
By incorporating layers of perceived legitimacy, this campaign is highly effective at bypassing MFA and harvesting credentials.
Tycoon 2FA is a phishing-as-a-service (PhaaS) platform first observed in August 2023 that operates as an adversary-in-the-middle (AitM) phishing kit. It can sidestep multifactor authentication (MFA) protections and lately targets Microsoft 365 and Gmail session cookies.