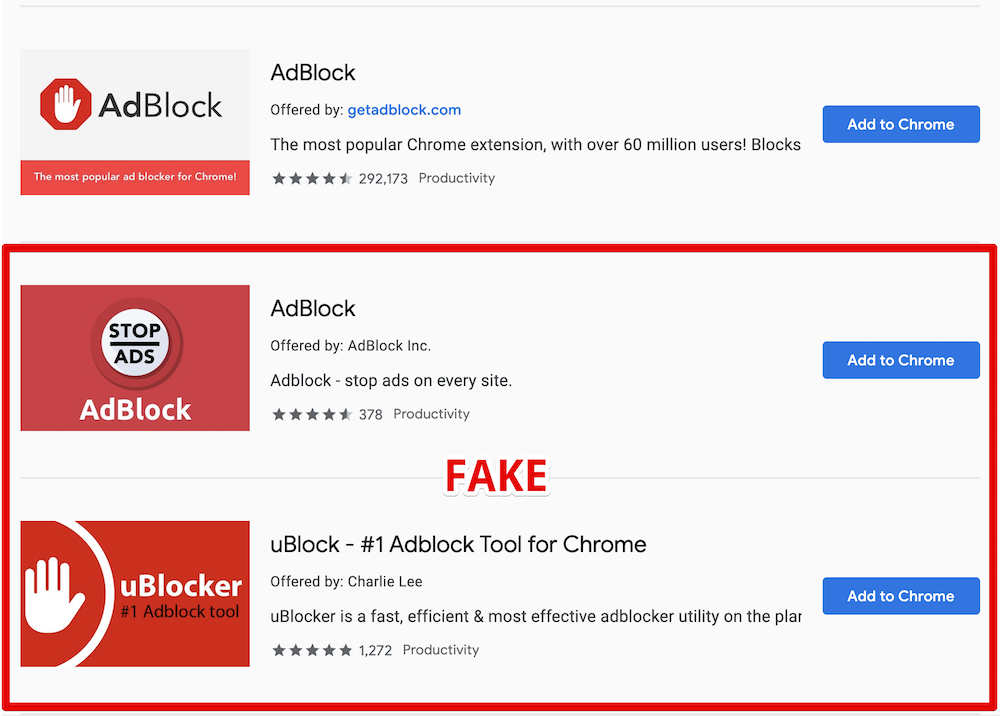
Two Fake Ad Blocker Extensions are Actually Cookie Stuffing Tools
- Two popular but fake ad-blocking extensions will fill your browser with thousands of cookies.
- The developers of the two add-ons made millions each month from fraudulent affiliate commissions.
- Google has finally removed the extensions, after numerous reports and an AdGuard study.
As reported by “AdGuard”, two extensions carrying the names AdBlock and uBlock Origin are engaged in ad fraud, indulging in cookie stuffing/dropping that covers a wide range of affiliates. The two browser extensions are fake ones, taking their names from other well-known and trusted extensions. This has helped them grow quickly and now count 800k and 850k users respectively. While the fake extensions continue to work well in terms of blocking ads, they are dropping cookies in the background, making money for the extension developers. Simply put, cookie stuffing is the process of dropping cookies that are completely unrelated to the websites the user is visiting. As an exchange for this service, the dropper receives a commission when the user buys something from an affiliate, and everyone except the user is happy.
Source: adguard.com
This is because the large number of cookies that are dropped onto the user’s browser are basically tracking them. In addition to that, a large number of cookies makes browsing sessions gradually slower, as the web browser needs to load these otherwise small pieces of code. According to AdGuard researchers who made the discovery, the two extensions wait for 55 hours after their installation before they activate the fraudulent cookie dropping mechanism. If the user has activated the developer console on the browser, the extensions stop their cookie stuffing activity so as not to get caught.
The cookies that are dropped by them belong to 300 popular websites, including Microsoft, Linkedin, Booking.com, Aliexpress, and Teamviewer. Google has finally removed the extensions from the Chrome Store, but this came after multiple reports about the two add-ons, and only after AdGuard published their detailed study. As the researchers estimate, the malicious actors must have been making millions of USD each month from this particular ad-fraud operation.
Obviously, Google didn’t do a good job in reviewing these extensions when they were submitted onto the Chrome Store. Blocking them now won’t remove them from your browser, so if you have them installed, you should delete them and clear your cookies. If you still wish to use an ad blocker, visit the website of trusted developers and pick the add-on right from there. Unfortunately, the Chrome Store does not deserve your trust, at least not at the time being. To clear your cookies, visit Chrome’s settings, hop to "Privacy and Security", select “Clear browsing data”, tick the cookies box and hit the “Clear data” button.
How do you block ads on your browser? Let us know in the comments below, or on our socials, on Facebook and Twitter.