TrueDialog Exposed Millions of SMS Messages in Unprotected Database
- More than 100 million customers of TrueDialog had their highly sensitive data exposed.
- The company left one of their databases unprotected and accessible to anyone online.
- The implications of the exposure are severe, and they will also be long-lasting.
TrueDialog, an enterprise-grade business SMS solutions provider has blundered by leaving a massive database unprotected online. The misconfiguration was discovered by vpnMentor’s Noam Rotem and Ran Locar on November 28, who reported the problem to TrueDialog immediately as the ownership of the database was apparent. The tech firm responded quickly and secured the database on November 29, 2019, but the total duration of the exposure remains unknown. The consequences of this data leak are definitely pretty dire though.
TrueDialog has been serving various high-profile entities for a decade now, and its clientele constitutes of small and large businesses, educational institutes, organizations, marketers, and even individuals. Currently, they count over five billion subscribers around the globe, although this particular exposure concerns U.S.-based customers only. According to the researchers, the number of compromised customers is approximately 100 million people. The data entries in the database contained the following information:
- Full Names of recipients, TrueDialog account holders, and TrueDialog users
- Content of messages
- Email addresses
- Phone numbers of recipients and users
- Dates and times messages were sent
- Status indicators on messages sent, like Read receipts, replies, etc.
- TrueDialog account details
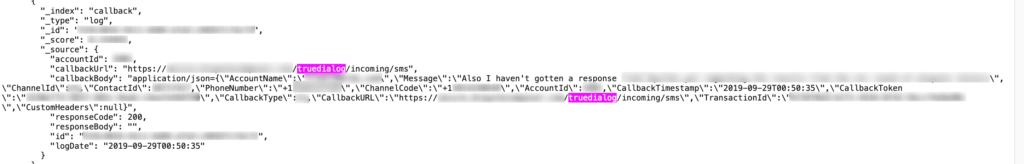
Source: vpnMentor
Besides the sensitive personal data, there were also technical logs in the database that could make it easier for the actors to infiltrate deeper. All things considered, the impact of this incident is dire, both for the reputation of TrueDialog and also for the customers who have been exposed. From account takeover to corporate espionage, and from identity theft to phishing attempts, the exposed individuals are running multiple and long-lasting risks. That said, if you are a customer of TrueDialog, be careful with how you respond to unsolicited messages that come from people whom you don’t know. Since it is your full names, email addresses and phone numbers that have been leaked, you may be approached by a scammer even years from now.
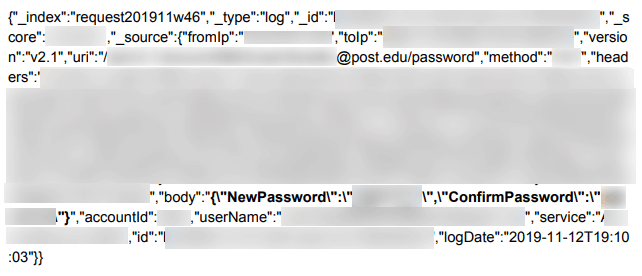
Source: vpnMentor
The vpnMentor team has also discovered passwords of TrueDialog accounts, so resetting your credentials should be your first immediate action right now. There’s a mix of cleartext and base64 encoded passwords, so there are different levels of severity for the exposed users. However, even the encrypted set of passwords are easy to decrypt this time, so no one is safe. Next, contact TrueDialog and ask for details and clarifications, and then finally, contact the data protection authorities and inform them of the incident, urging an investigation.
Are you using TrueDialog’s SMS services? Will you continue to trust the company from now on? Let us know where you stand in the comments down below, or on our socials, on Facebook and Twitter.