Trickbot Now Passes Through Email Spam Filters via Google URL Redirection
- Malicious actors are using URL redirection to take victims to their Trickbot-downloader site.
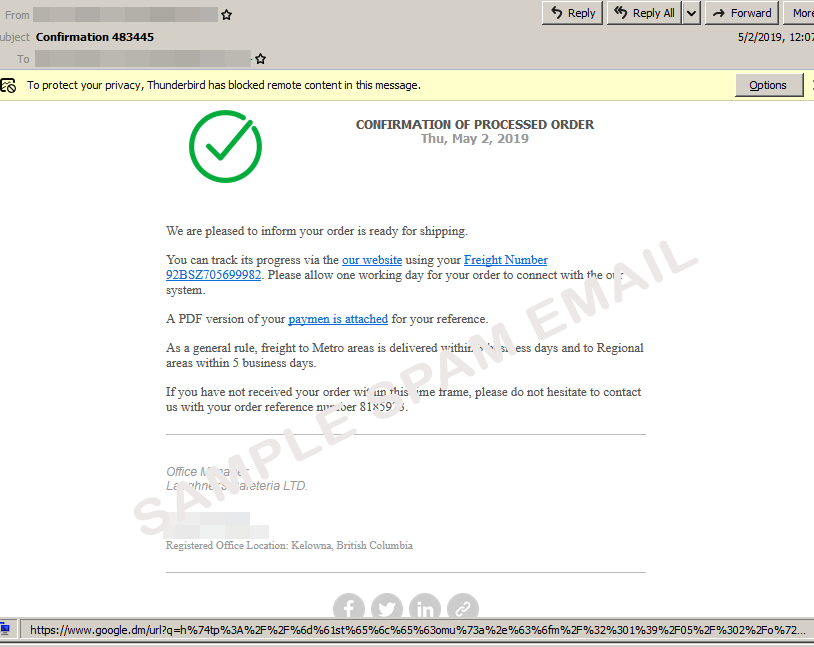
- The message lures the recipients by presenting an order which has been shipped.
- The Trickbot that is propagated is the same old powerful banking trojan that can steal information from a wide range of locations.
Trend Micro researchers have discovered a new variant of the Trickbot banking trojan that is now better at passing through spam filters. More specifically, the new variant uses a Google redirection URL in the fake email, which leads to the malicious URL in the next step. Using a Google URL is a solid practice to help create an image of legitimacy, and when combined with a well-written email, embedded social media icons, and a complete email signature, the end result is pretty convincing for the recipient. The message that is currently used by the actors concerns a supposed order that is ready for shipping, offering links to the tracking number and the payment receipt.
Image source: blog.trendmicro.com
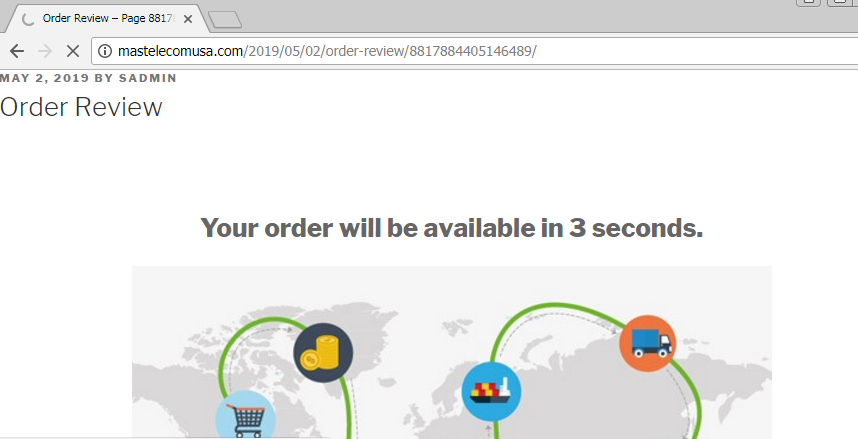
People who will click on the link will be met with a redirection notice, but this could be easy to miss. The main point of the Google URL is to minimize the chances of the message ending up in the spam folder, and the trick seems to be working. While the user is waiting for three seconds for their order status to load, what actually happens is that they’re getting a .zip file containing a Trickbot downloader.
Image source: blog.trendmicro.com
Through a module analysis, the researchers have figured out that the Trickbot that is used in this 'URL-redirection' campaign is already known. However, that is not to say that Trickbot isn’t dangerous or capable of a series of nasty functions. Here are its main capabilities as supported by Trickbot's individual modules:
- Steal browser history data and cookies.
- Inject tracking code into the browser and steal banking information.
- Search and find email addresses in the local filesystem.
- Profile POS terminal networks via LDAP.
- Steal credentials from Outlook, WinSCP, and Filezilla.
- Gather full system and user information.
- Conduct lateral movement by exploiting MS17-010, and propagate to the compromised network.
What is important about this story is the fact that messages that pass through our spam filters should not be trusted. You should always check the address of the sender and consider whether you were waiting for a message from them or not, read the message carefully and look for grammar errors, and not accept any redirections whatsoever. If you have downloaded a file from such a message by mistake, do not ever attempt to execute it, as this is where Pandora’s box opens.
Care to share your thoughts on the above? Feel free to do so in the comments down below, or on our socials, on Facebook and Twitter.